Tampilkan postingan dengan label English Version. Tampilkan semua postingan
Tampilkan postingan dengan label English Version. Tampilkan semua postingan

Windows 7 not only attracted much attention from the press as a high-tech, but also there are many new interface changes, such as the redesigned taskbar, new file management features, libraries and others. Several tools have been enhanced which is then included with the OS. Here we discuss 10 of the best tools windows 7 which makes the job easier computing.
1. Action Center
Centralized management is hot in Windows 7 and gives you one-stop shopping site where you can take care of security, troubleshooting, and recovery, rather than searching for an applet for each part. Everything is combined in an easy to use Control Panel, where you get a maintenance and safety messages and can view performance information, change the UAC settings, and more.
This is a development from the Security Center in Windows Vista. It makes sense to combine the security settings, system maintenance, and recovery. Action Center has emerged as an icon in the system tray, which displays a red X symbol if there is a problem that needs you are looking for.
2. Problem Steps Recorder
One of the coolest new tool in Windows 7 is the Problem Steps Recorder (PSR), mainly to provide technical support to users of Windows. No matter how hard they try, but users often have problems to accurately describe their problem and steps they take before or after the experience. Sure, Remote Assistance can be a blessing in this situation. But we can not always connect to a user's computer in real time. That's when PSR come in handy.
Problem Steps Recorder is a type of software that records all actions keystrokes, mouse clicks, including screenshots etc. and save the sequence of events in an MHTML document pages. You can start by entering psr.exe PSR in the Start Search box via the command prompt option.
3. ISO burner
ISO image file is a file type that is often used to distribute software. In Windows 7, Microsoft included this as an answer to many users wish list for a long time. Now you do not need to download and install a third-party program to burn ISO files to disk. Suppose you want to create a bootable CD use this tool. This is a simple process: Once you've downloaded. ISO to your hard drive, simply double click and Windows 7 will open the Burn Disc Image dialog box to burn the disc.
4. Biometric device management
In previous Windows versions, biometric authentication and management of biometric devices (fingerprint sensor) required third party software that may or may not be well integrated with the OS. Now in Windows 7 already built in. Windows Biometric Framework, which gives developers the API that you can use to build biometrics into applications. Fingerprint sensor hardware makers, such as UPEK and AuthenTec, in cooperation with Microsoft on developing its framework. Biometric can be accessed through the Control Panel.
5. Credential Manager
Credential Manager is a new feature in Windows 7. This tool is similar in some ways premises password management features in Vista User Account but this is more sophisticated. You can manage the Windows credentials for the various computers that you are signed onto, certificate-based credentials, and others (for e-mail accounts, web accounts, etc.). This is all saved by default in Windows Vault.
Perhaps the best feature new in Credential Manager is the ability to backup anhttp://www.blogger.com/img/blank.gifd restore Vault. Microsoft recommends that you keep backing up on removable drives, such as flash drives, to back up if you experience a hardware failure. For more information, see Windows 7: Windows 7: Exploring Credential Vault Manager and Windows directly from the website.
6. Projection display and the Windows Mobility Center
If you give many presentations, you will be greeted by a new tool in Windows 7 that makes it easy for you to display projectors in the desktop Windows 7. Just press the Windows logo key + P and you will see a pop-up box where you can make the choice of presentation. The first is the default settings and displayed on computer screens only. The second clone display settings on the computer screen to the projector. A third setting to extend the desktop on both computer screen and projector, and the fourth displays only the settings through the projector and turn off the computer screen.
7. Text tuning and color calibration
Your computer might not work, but your screen is what you see throughout the day. If it does not look good, you do not get the most from your computing experience, and can even cause you eye strain. In Windows 7 there are two tools to customize the look to suit your preferences. You can access the ClearType Text Tuner from Control Panel or from the command (cttune.exe). If you have multiple monitors, you can adjust according to each monitor.
This tuning tool works much like the eye chart at the optometrist's office, and please you choose one that looks best for you. In addition to text tuner, Windows 7 provides color calibration tool. It can be accessed from the Control Panel or from the command line (dccw.exe). It helps you to adjust gamma, brightness, contrast, and color rendition on your monitor to display the best.
8. Disc Repair System
Actually, the Vista Service Pack 1 Beta already lets you easily create disc repair system with friendly graphical interface, but has been removed and re-released in the final in SP1. Windows 7 to improve this function. Just click [Start] and type [System Repair] in the Search box. Click [Create A System Repair Disc] to open the dialog box. To use the disc, please mesukkan in the drive and reboot the computer from the disk. (You may need to set the CD / DVD drive as primary boot device in BIOS) Then you will get a list of system recovery options, which include:
- Startup Repair
- System restore
- System image recovery
- Windows Memory Diagnostic
- Command prompt
9. Better backup utility
In previous Windows versions already include a backup utility, but this tool has been perfect significantly in Windows 7. Vista backup program is user friendly but not very flexible. Windows 7 provides more detailed control over what you want to backup. You can run the Backup And Restore from Control Panel or by typing a backup in the Search box on the Start menu. You can back up files to local hard disk, removable disk, DVD, or another computer on the network (origin diisinkan on the network). Then you can also choose to create a backup folder or individual libraries. You can also exclude certain folders when backing up.
10. PowerShell v2
Windows PowerShell (Figure P) is a shell command-line interface and scripting tools that make it easier for Windows administrators to automate tasks using cmdlets, which are commands that perform a single command, and scripts, which consists of several cmdlets for complex tasks , multi-step tasks. Earlier versions of Windows includes a command-line interpreter (command.com or cmd.exe), but PowerShell is much more powerful, also provided the UNIX environment, this command can automate nearly every function of the GUI.
PowerShell can be downloaded and run on Windows XP or Vista, but in Windows 7 is included in a built-in. PowerShell v2 adds about 240 new cmdlets, as well as APIs and new features, such as the ability to call the PowerShell scripts and cmdlets on remote computer. You can find out more about PowerShell on Microsoft's website.
Voice over IP (VoIP) systems today are gaining in popularity today for several reasons, most notable are the availability of so many open source and commercial options, the high degree of available interface devices that allow you to connect to existing circuit based networks and hardware, and the ability to create full end to end IP based solutions using available high-speed links or gateways with commercial trunk providers. However, it is still easy to make a poor purchasing decision unless you take a good look at the basic requirements of what a communication system needs to provide to be effective in your business and help you achieve your cost savings while still maintaining your ability to be connected to your clients and vendors in an effective manner. My intent here is to help outline the 5 standard features that your VoIP system should have for it to be considered the proper solution for your enterprise.
Examination
Standardization and Flexibility
Just like Henry Ford grew the automobile business based upon the obvious concept of standardization, the VoIP industry gained its recent focus and popularity based upon the same ideals. Gone are the days of having to select and architect a solution based upon the supported protocols of one vendor and become locked in. The two major signaling protocols you will see today, H.323 and SIP are the largest players, with H.323 starting to lag behind as SIP gains in popularity and support, more compliant vendors, and continued enhanced to support more media streams and tighter device integration that up until recently has been what was keeping H.323 ahead in the game. Keeping in mind that H.323 is still the more mature technology, currently it is holding its ground in the carrier space and is used quite extensively as a trunk side protocol. This has allowed SIP to comfortably gain foothold in the enterprise space as a local carrier style protocol that is simpler to implement, troubleshoot, and extend with new features as needed. It is clear that for a system to be considered future proof it has to support the currently prevalent standards but also allow ‘plug ability’ and offer support for emerging standards, or alterations to the existing standards as well.
Integration Options
Unless you are starting from scratch you are most likely attempting to integrate a VoIP option into your existing infrastructure as part of a phased deployment strategy. The current list of options to accomplish this is growing longer and longer every day, and that has many benefits for the consumer with regards to architecture, cost, interoperability options, and the quicker movement to tighter standards compliance between vendors. There is no longer a need to consider the move to VoIP to be an all or nothing deal with the introduction of gateway devices that allow you to leverage your current investment in older TDM based equipment and enhance it with the newer IP based messaging solutions. Doing this allows you to add new devices to the newer IP network while maintaining a rich level of integration with the legacy TDM equipment until it lives out its natural (and still depreciable) life span.
Security
As with everything today, security is a huge consideration when you start to think about moving to VoIP. If it is not something that you have already though about, or your vendor has not discussed it deeply with you then I urge you to stop reading this right now, go to your vendor and ASK how secure your current VoIP implementation (or the one you are planning to install) is.
Security is so critical in today’s business market, but because people have felt so safe in the past using TDM voice infrastructures where ‘tapping’ meant actually making a physical connection to the ‘wires’, the thought of security quite often eludes people when you starting the talk about VoIP. It is so easy to fire up a copy of Wireshark on your network, collect some packets, and use the tools built right into the GUI to listen to VoIP conversations. So, what do you do? The answer is simple. You turn on encryption and ensure that every device you use within in your IP infrastructure involved in the call supports the encryption scheme that you pick. Keep in mind that while encryption is good, it does add CPU load to your devices, can cause higher network utilization because the packets can get larger, and can add complexity to any troubleshooting efforts, but you should NOT implement any VoIP system without taking security into consideration. One fine option that I have used is to consider your internal network to be secure and just encrypt the calls that pass via IP between external parties (over your IP based trunks if you use them) or between all your company locations using the public IP network. It’s my feeling that as long as you keep your internal IP infrastructure secure (IE: tight controls on who can enter your IT area, and you are using switches rather than hubs), bothering to encrypt internal IP connections is not always needed because in a properly configured environment you will not be able to capture VoIP data other than what is directed to you. If you are using hubs then all bets are off of course. That is a subject for another article.
Support
As with most other technologies, part of your purchasing and deployment planning MUST be to take the support model into consideration. Don’t just assume that your existing vendor that supports your current internet connection to the external world is going to be there if you have IP trunk problems, understand what terminology like QoS, jitter, and other VoIP lingo means, or even how to correct them if problems occur. As when introducing any new technology you need to have a sit-down with everyone involved in the proposed value chain and establish an understanding of expectations, possible support needs, costs, and schedules. You may find out that your provider is by default blocking the native ports that the typical VoIP protocols require simply because they are not used to requiring them to be open for other clients. If you are ready to move to IP for your voice communications just understand that while you may have been willing to put up with slowness in the afternoons when you tried to use the web to order your dinner so you could pick it up on the way home, a slow data connection can wreak havoc with voice quality and the ability to establish a call. You may need to consider a separate IP connection just dedicated to voice, and in fact you may need to start considering redundant connections using two different providers for your voice if you have not already done so for your data. Additionally, ensure that your vendor has the proper debugging tools in place, knows how to use them, and is willing to offer training to your staff, or that you are willing to use third parties to get them trained, so that they can be used to keep the system running in top condition. Remember that voice communication is still considered a top priority in today’s business world and loosing that, even for a few hours, can make a customer start looking for someone to replace you as a vendor.
Extension Points
Many people today are used to just using the phone to talk, or maybe send faxes, but once the move to IP is made the benefits will start to bring on questions about other methods of application integration, and additional ways to leverage the new communications system. One thing that you should always consider on any new system, not just VoIP, are ways that you can utilize it going forward for things other than just your current needs. A car would not be much use if you could only drive it back and forth to work would it? The same goes for your telephony solution. Right from the start you should consider investigating the extension areas of all the solutions you look at and at least gain an understanding of the features and benefits that each system may or may not offer. For example, it could be very disappointing to get a system all in place and six months latter determine that you still need to add a bank of analog trunk lines to and receive faxes because your solution did not include the ability for Fax over IP (FoIP) codecs. Making blanket assumptions like ‘just because traditional faxes use our existing voice lines the VoIP system should also do fax’ can lead to some very tense moments across a boardroom table. Also consider integration with other areas like Instant Messaging (IM) and application integration such as the ability to build basic Interactive Voice Response (IVR) menus (IE: ‘To talk to support, please press 1, to talk to sales, please press 2,…) into the system and create simple auto attendant applications. These simple features can help add some great value that may not have been considered previously, and allow you to recoup the costs of a VoIP implementation over a shorter timeline than previously anticipated. Areas like this can allow you to bring systems together under one area and thus cut down the size of your external vendor list.
Conclusion
As you can see, the move to VoIP is fraught with decisions, technical considerations, and even some simple human capital management opportunities, but the gains in productivity, efficiency, and the ability to leverage existing infrastructure and gain some valuable benefits in the areas of long term manageability, application integration, multi-modal communications options and simpler to manage infrastructure far outweigh the potential problems as long as the map forward is well thought out and planned. As with most IT based business decisions it is always good to ensure that everyone understands the possible features and benefits as well as the potential risks and how they can be mitigated to derive the value that is expected.
Disclosures and References
As part of my previous experience in VoIP technology I spent 10 years as a product and training specialist working for both Intel Corporation and Dialogic Corporation in the area of Digital PBX TDM to IP interfacing with regards to the Netstructure PBX/IP Media gateway product line. In addition, my secondary focus was working closely with vendors offering tightly integrated VoIP solutions such as Microsoft Exchnage Unified Messaging and IBM Lotus Sametime using these devices as well as the design and development of product training classes, certification programs for user and administrative positions, and product documentation collateral.
READ MORE
Examination
Standardization and Flexibility
Just like Henry Ford grew the automobile business based upon the obvious concept of standardization, the VoIP industry gained its recent focus and popularity based upon the same ideals. Gone are the days of having to select and architect a solution based upon the supported protocols of one vendor and become locked in. The two major signaling protocols you will see today, H.323 and SIP are the largest players, with H.323 starting to lag behind as SIP gains in popularity and support, more compliant vendors, and continued enhanced to support more media streams and tighter device integration that up until recently has been what was keeping H.323 ahead in the game. Keeping in mind that H.323 is still the more mature technology, currently it is holding its ground in the carrier space and is used quite extensively as a trunk side protocol. This has allowed SIP to comfortably gain foothold in the enterprise space as a local carrier style protocol that is simpler to implement, troubleshoot, and extend with new features as needed. It is clear that for a system to be considered future proof it has to support the currently prevalent standards but also allow ‘plug ability’ and offer support for emerging standards, or alterations to the existing standards as well.
Integration Options
Unless you are starting from scratch you are most likely attempting to integrate a VoIP option into your existing infrastructure as part of a phased deployment strategy. The current list of options to accomplish this is growing longer and longer every day, and that has many benefits for the consumer with regards to architecture, cost, interoperability options, and the quicker movement to tighter standards compliance between vendors. There is no longer a need to consider the move to VoIP to be an all or nothing deal with the introduction of gateway devices that allow you to leverage your current investment in older TDM based equipment and enhance it with the newer IP based messaging solutions. Doing this allows you to add new devices to the newer IP network while maintaining a rich level of integration with the legacy TDM equipment until it lives out its natural (and still depreciable) life span.
Security
As with everything today, security is a huge consideration when you start to think about moving to VoIP. If it is not something that you have already though about, or your vendor has not discussed it deeply with you then I urge you to stop reading this right now, go to your vendor and ASK how secure your current VoIP implementation (or the one you are planning to install) is.
Security is so critical in today’s business market, but because people have felt so safe in the past using TDM voice infrastructures where ‘tapping’ meant actually making a physical connection to the ‘wires’, the thought of security quite often eludes people when you starting the talk about VoIP. It is so easy to fire up a copy of Wireshark on your network, collect some packets, and use the tools built right into the GUI to listen to VoIP conversations. So, what do you do? The answer is simple. You turn on encryption and ensure that every device you use within in your IP infrastructure involved in the call supports the encryption scheme that you pick. Keep in mind that while encryption is good, it does add CPU load to your devices, can cause higher network utilization because the packets can get larger, and can add complexity to any troubleshooting efforts, but you should NOT implement any VoIP system without taking security into consideration. One fine option that I have used is to consider your internal network to be secure and just encrypt the calls that pass via IP between external parties (over your IP based trunks if you use them) or between all your company locations using the public IP network. It’s my feeling that as long as you keep your internal IP infrastructure secure (IE: tight controls on who can enter your IT area, and you are using switches rather than hubs), bothering to encrypt internal IP connections is not always needed because in a properly configured environment you will not be able to capture VoIP data other than what is directed to you. If you are using hubs then all bets are off of course. That is a subject for another article.
Support
As with most other technologies, part of your purchasing and deployment planning MUST be to take the support model into consideration. Don’t just assume that your existing vendor that supports your current internet connection to the external world is going to be there if you have IP trunk problems, understand what terminology like QoS, jitter, and other VoIP lingo means, or even how to correct them if problems occur. As when introducing any new technology you need to have a sit-down with everyone involved in the proposed value chain and establish an understanding of expectations, possible support needs, costs, and schedules. You may find out that your provider is by default blocking the native ports that the typical VoIP protocols require simply because they are not used to requiring them to be open for other clients. If you are ready to move to IP for your voice communications just understand that while you may have been willing to put up with slowness in the afternoons when you tried to use the web to order your dinner so you could pick it up on the way home, a slow data connection can wreak havoc with voice quality and the ability to establish a call. You may need to consider a separate IP connection just dedicated to voice, and in fact you may need to start considering redundant connections using two different providers for your voice if you have not already done so for your data. Additionally, ensure that your vendor has the proper debugging tools in place, knows how to use them, and is willing to offer training to your staff, or that you are willing to use third parties to get them trained, so that they can be used to keep the system running in top condition. Remember that voice communication is still considered a top priority in today’s business world and loosing that, even for a few hours, can make a customer start looking for someone to replace you as a vendor.
Extension Points
Many people today are used to just using the phone to talk, or maybe send faxes, but once the move to IP is made the benefits will start to bring on questions about other methods of application integration, and additional ways to leverage the new communications system. One thing that you should always consider on any new system, not just VoIP, are ways that you can utilize it going forward for things other than just your current needs. A car would not be much use if you could only drive it back and forth to work would it? The same goes for your telephony solution. Right from the start you should consider investigating the extension areas of all the solutions you look at and at least gain an understanding of the features and benefits that each system may or may not offer. For example, it could be very disappointing to get a system all in place and six months latter determine that you still need to add a bank of analog trunk lines to and receive faxes because your solution did not include the ability for Fax over IP (FoIP) codecs. Making blanket assumptions like ‘just because traditional faxes use our existing voice lines the VoIP system should also do fax’ can lead to some very tense moments across a boardroom table. Also consider integration with other areas like Instant Messaging (IM) and application integration such as the ability to build basic Interactive Voice Response (IVR) menus (IE: ‘To talk to support, please press 1, to talk to sales, please press 2,…) into the system and create simple auto attendant applications. These simple features can help add some great value that may not have been considered previously, and allow you to recoup the costs of a VoIP implementation over a shorter timeline than previously anticipated. Areas like this can allow you to bring systems together under one area and thus cut down the size of your external vendor list.
Conclusion
As you can see, the move to VoIP is fraught with decisions, technical considerations, and even some simple human capital management opportunities, but the gains in productivity, efficiency, and the ability to leverage existing infrastructure and gain some valuable benefits in the areas of long term manageability, application integration, multi-modal communications options and simpler to manage infrastructure far outweigh the potential problems as long as the map forward is well thought out and planned. As with most IT based business decisions it is always good to ensure that everyone understands the possible features and benefits as well as the potential risks and how they can be mitigated to derive the value that is expected.
Disclosures and References
As part of my previous experience in VoIP technology I spent 10 years as a product and training specialist working for both Intel Corporation and Dialogic Corporation in the area of Digital PBX TDM to IP interfacing with regards to the Netstructure PBX/IP Media gateway product line. In addition, my secondary focus was working closely with vendors offering tightly integrated VoIP solutions such as Microsoft Exchnage Unified Messaging and IBM Lotus Sametime using these devices as well as the design and development of product training classes, certification programs for user and administrative positions, and product documentation collateral.
 Google is often regarded as the best search engine in the world, which often returns the best matching web pages that users are looking for in the search results. However, with the amazing and overwhelming amount of blogs and websites been created everyday, where much of it is of spam, useless, plagiarist, blunt copy and paste or even autoblog which automatically pull and post duplicating contents from various sources, Google may allow some of these sites to slip into its search results.
Google is often regarded as the best search engine in the world, which often returns the best matching web pages that users are looking for in the search results. However, with the amazing and overwhelming amount of blogs and websites been created everyday, where much of it is of spam, useless, plagiarist, blunt copy and paste or even autoblog which automatically pull and post duplicating contents from various sources, Google may allow some of these sites to slip into its search results.Google search engine does not have built-in capability to filter or remove unwanted websites or domains from the search results. However, Google does provide Google Custom Search Engine service under Google Co-op which allows anyone to create their own search engine by themselves. Google Custom Search Engine allows user to exclude domains that user does not want to appear in search results, or include only selected domains.
Use the following Google Custom Search Engine trick to blacklist or exclude domains or websites from the Google search engine.
1. Register or sign into the Google Account.
2. Visit Google Custom Search Engine homepage.
3. click on Create a Custom Search Engine button
4 Set up your search engine by giving the name and description, selecting language and Standard edition (free and no charge), and tick check box of I have read and agree to the Terms of Service.
5. Click Next.
6. Choose or customize a style.
7. Click Next.
8. Under “Next steps” section, click on Include more sites.
9 .Remove any domain the listed under the Included sites section, by selecting the domain, and clicking Delete button.
10.Under “Excluded Sites” section, click on Exclude sites.
11.Enter the web page URL or domain name of the site that you want to exclude from the search results. User can choose to exclude all pages whose address contains the URL, exclude just this specific page or URL pattern entered, or dynamically extract links from this page and exclude them from the search engine based on the rule of exclude all pages the page links to, exclude all partial sites the page links to, or exclude all sites the page links to.
Tip: Click on Exclude sites in bulk to enter the blacklisted sites or URLs of web pages in bulk. For bulk entry, user can exclude all pages on these sites or exclude just the specific pages entered.
12.Click on Save when done.
13.The custom search engine which excludes blacklisted or unwanted sites, domains or web pages is now ready for use.
To preview and test the search engine, click on Preview link under the Control Panel.
To get the URL of the custom search engine, right click on the name title of the search engine, and select Copy Link Location or Copy Shortcut (IE). The URL of the custom search engine can be bookmarked, made favorite or homepage for easy access.
 Your Flashdisk didn't responding? i think it's really annoying. Someone ask me about his Toshiba Flashdisk which won't work properly, it just show report disk drive and not responding in any PC. I don't say that Toshiba flash drive is bad, but many people meets that problem. Here i'll explain how to fix it, Try to follow the instructions on this page, it might the Flashdisk is infected by any malicious file.
Your Flashdisk didn't responding? i think it's really annoying. Someone ask me about his Toshiba Flashdisk which won't work properly, it just show report disk drive and not responding in any PC. I don't say that Toshiba flash drive is bad, but many people meets that problem. Here i'll explain how to fix it, Try to follow the instructions on this page, it might the Flashdisk is infected by any malicious file.Follow this guide :
- Go to Toshiba Downloads, navigate to your model and look for updated flash card oand the Toshiba Value Added Package. Good time to update other drivers while there.
- Download the one you need - SAVE - go to where you put them - RIGHT CLICK - RUN AS ADMIN - REBOOT
- after each installation - you should check in Device Manager to make sure the drivers were updated as some (such as sound)
- You might need to be run more than once as they Roll Back until finally the current driver is installed. Other things you can try include removing possible corruption from system.
- Start - type this in Search Box -> COMMAND find at top and RIGHT CLICK - RUN AS ADMIN
- Enter this at the prompt - sfc /scannow
- How to analyze the log file entries that the Microsoft Windows Resource Checker (SFC.exe) program
- generates in Windows Vista cbs.log
- Try running checkdisk - schedule it to run at next start and then Apply OK your way out then restart.
- How to Run Check Disk at Startup in Vista
Hope this help your Toshiba Flashdisk Not Responding.
What's VPN? VPN(Virtual Private Network)technology included in Windows Server 2003 helps enable cost-effective, secure remote access to private networks. VPN allows administrators to take advantage of the Internet to help provide the functionality and security of private WAN connections at a lower cost. In Windows Server 2003, VPN is enabled using the Routing and Remote Access service. VPN is part of a comprehensive network access solution that includes support for authentication and authorization services, and advanced network security technologies.
There are two main strategies that help provide secure connectivity between private networks and enabling network access for remote users.
Dial-up or leased line connections
A dial-up or leased line connection creates a physical connection to a port on a remote access server on a private network. However, using dial-up or leased lines to provide network access is expensive when compared to the cost of providing network access using a VPN connection.
VPN connections
VPN connections use either Point-to-Point Tunneling Protocol (PPTP) or Layer Two Tunneling Protocol/Internet Protocol security (L2TP/IPSec) over an intermediate network, such as the Internet. By using the Internet as a connection medium, VPN saves the cost of long-distance phone service and hardware costs associated with using dial-up or leased line connections. A VPN solution includes advanced security technologies such as data encryption, authentication, authorization, and Network Access Quarantine Control.
Note *Network Access Quarantine Control is used to delay remote access to a private network until the configuration of the remote access computer has been examined and validated.
Using VPN, administrators can connect remote or mobile workers (VPN clients) to private networks. Remote users can work as if their computers are physically connected to the network. To accomplish this, VPN clients can use a Connection Manager profile to initiate a connection to a VPN server. The VPN server can communicate with an Internet Authentication Service (IAS) server to authenticate and authorize a user session and maintain the connection until it is terminated by the VPN client or by the VPN server. All services typically available to a LAN-connected client (including file and print sharing, Web server access, and messaging) are enabled by VPN.
VPN clients can use standard tools to access resources. For example, clients can use Windows Explorer to make drive connections and to connect to printers. Connections are persistent: Users do not need to reconnect to network resources during their VPN sessions. Because drive letters and universal naming convention (UNC) names are fully supported by VPN, most commercial and custom applications work without modification.
VPN Scenarios
Virtual private networks are point-to-point connections across a private or public network such as the Internet. A VPN client uses special TCP/IP-based protocols, called tunneling protocols, to make a virtual call to a virtual port on a VPN server. In a typical VPN deployment, a client initiates a virtual point-to-point connection to a remote access server over the Internet. The remote access server answers the call, authenticates the caller, and transfers data between the VPN client and the organization’s private network.
To emulate a point-to-point link, data is encapsulated, or wrapped, with a header. The header provides routing information that enables the data to traverse the shared or public network to reach its endpoint. To emulate a private link, the data being sent is encrypted for confidentiality. Packets that are intercepted on the shared or public network are indecipherable without the encryption keys. The link in which the private data is encapsulated and encrypted is known as a VPN connection.

Remote Access VPN
Remote access VPN connections enable users working at home or on the road to access a server on a private network using the infrastructure provided by a public network, such as the Internet. From the user’s perspective, the VPN is a point-to-point connection between the computer (the VPN client) and an organization’s server. The exact infrastructure of the shared or public network is irrelevant because it appears logically as if the data is sent over a dedicated private link.
Site-to-Site VPN
Site-to-site VPN connections (also known as router-to-router VPN connections) enable organizations to have routed connections between separate offices or with other organizations over a public network while helping to maintain secure communications. A routed VPN connection across the Internet logically operates as a dedicated WAN link. When networks are connected over the Internet, as shown in the following figure, a router forwards packets to another router across a VPN connection. To the routers, the VPN connection operates as a data-link layer link.
A site-to-site VPN connection connects two portions of a private network. The VPN server provides a routed connection to the network to which the VPN server is attached. The calling router (the VPN client) authenticates itself to the answering router (the VPN server), and, for mutual authentication, the answering router authenticates itself to the calling router. In a site-to site VPN connection, the packets sent from either router across the VPN connection typically do not originate at the routers.
READ MORE
There are two main strategies that help provide secure connectivity between private networks and enabling network access for remote users.
Dial-up or leased line connections
A dial-up or leased line connection creates a physical connection to a port on a remote access server on a private network. However, using dial-up or leased lines to provide network access is expensive when compared to the cost of providing network access using a VPN connection.
VPN connections
VPN connections use either Point-to-Point Tunneling Protocol (PPTP) or Layer Two Tunneling Protocol/Internet Protocol security (L2TP/IPSec) over an intermediate network, such as the Internet. By using the Internet as a connection medium, VPN saves the cost of long-distance phone service and hardware costs associated with using dial-up or leased line connections. A VPN solution includes advanced security technologies such as data encryption, authentication, authorization, and Network Access Quarantine Control.
Note *Network Access Quarantine Control is used to delay remote access to a private network until the configuration of the remote access computer has been examined and validated.
Using VPN, administrators can connect remote or mobile workers (VPN clients) to private networks. Remote users can work as if their computers are physically connected to the network. To accomplish this, VPN clients can use a Connection Manager profile to initiate a connection to a VPN server. The VPN server can communicate with an Internet Authentication Service (IAS) server to authenticate and authorize a user session and maintain the connection until it is terminated by the VPN client or by the VPN server. All services typically available to a LAN-connected client (including file and print sharing, Web server access, and messaging) are enabled by VPN.
VPN clients can use standard tools to access resources. For example, clients can use Windows Explorer to make drive connections and to connect to printers. Connections are persistent: Users do not need to reconnect to network resources during their VPN sessions. Because drive letters and universal naming convention (UNC) names are fully supported by VPN, most commercial and custom applications work without modification.
VPN Scenarios
Virtual private networks are point-to-point connections across a private or public network such as the Internet. A VPN client uses special TCP/IP-based protocols, called tunneling protocols, to make a virtual call to a virtual port on a VPN server. In a typical VPN deployment, a client initiates a virtual point-to-point connection to a remote access server over the Internet. The remote access server answers the call, authenticates the caller, and transfers data between the VPN client and the organization’s private network.
To emulate a point-to-point link, data is encapsulated, or wrapped, with a header. The header provides routing information that enables the data to traverse the shared or public network to reach its endpoint. To emulate a private link, the data being sent is encrypted for confidentiality. Packets that are intercepted on the shared or public network are indecipherable without the encryption keys. The link in which the private data is encapsulated and encrypted is known as a VPN connection.
Remote Access VPN
Remote access VPN connections enable users working at home or on the road to access a server on a private network using the infrastructure provided by a public network, such as the Internet. From the user’s perspective, the VPN is a point-to-point connection between the computer (the VPN client) and an organization’s server. The exact infrastructure of the shared or public network is irrelevant because it appears logically as if the data is sent over a dedicated private link.
Site-to-Site VPN
Site-to-site VPN connections (also known as router-to-router VPN connections) enable organizations to have routed connections between separate offices or with other organizations over a public network while helping to maintain secure communications. A routed VPN connection across the Internet logically operates as a dedicated WAN link. When networks are connected over the Internet, as shown in the following figure, a router forwards packets to another router across a VPN connection. To the routers, the VPN connection operates as a data-link layer link.
A site-to-site VPN connection connects two portions of a private network. The VPN server provides a routed connection to the network to which the VPN server is attached. The calling router (the VPN client) authenticates itself to the answering router (the VPN server), and, for mutual authentication, the answering router authenticates itself to the calling router. In a site-to site VPN connection, the packets sent from either router across the VPN connection typically do not originate at the routers.
 Windows 7 wireless, setting up, defining features of this network will be the lack of network passwords for local connections(both wirelessly or wired) and no single “boss” computer. Devices on the network will act as peers – no computer will rely on another computer to be present on the network – in order to reach the Internet, but it won’t be an ad-hoc network. File and folder sharing, of course, will depend on other computers being present, but we’ll look at specifying what folders we’ll share with others and these we will share and share alike.
Windows 7 wireless, setting up, defining features of this network will be the lack of network passwords for local connections(both wirelessly or wired) and no single “boss” computer. Devices on the network will act as peers – no computer will rely on another computer to be present on the network – in order to reach the Internet, but it won’t be an ad-hoc network. File and folder sharing, of course, will depend on other computers being present, but we’ll look at specifying what folders we’ll share with others and these we will share and share alike.Router Configurations
The most boss-like object in the network is the wireless router. For our purposes, we’ll presuppose that each computer can connect to the router. In our test network, the Vista desktop computer has the wired connection to the router and was used to set the router up. It’s very important that the router is not left at defaults and is set up properly because the security of the simplified network is based on the router and on having both a strong network password and an encrypted connection. By strong password, we mean a mix of letters and numbers that can’t be guessed or easily “cracked” by brute force. Your router setup program may suggest a pseudo-random password based on the encryption you selected. This is very safe to use. By encryption, we mean Wi-Fi Protected Access, or WPA-PSK. The “PSK” part stands for “pre-shared key,” which is that secure password.
Since setup varies and you’ll need to use the documentation for your router to perform it, we’ll only briefly touch further on this. You want to set it to broadcast your network name or service set identifier (SSID). You’ll want to make sure that each computer on the network can reach the Internet. A somewhat common problem you may encounter is that a PC can connect wirelessly to the router and seems to be passing some data when you view “Status” for the device, but the web browser can’t reach any web pages.
This can mean that the computer was set up by default for wireless networking(with Microsoft networks, of course), but not for Internet access. It is, however, easy to fix.
 SEO learning for increasing traffic which really important for optimizing your site. By increasing traffic to your site you will get the other parts of your site increase. They can be your Alexa rank and the more important is your online earning that automatically will increase too. So you must able to find the ways that can effect to your traffic ascendant. If you are disable to find the ways, doing tips and tricks from another webmaster who are willing to share their experiences freely.
SEO learning for increasing traffic which really important for optimizing your site. By increasing traffic to your site you will get the other parts of your site increase. They can be your Alexa rank and the more important is your online earning that automatically will increase too. So you must able to find the ways that can effect to your traffic ascendant. If you are disable to find the ways, doing tips and tricks from another webmaster who are willing to share their experiences freely.In connection with topic of this post, I would like to share my little knowledge about SEO that you can use to get huge traffic. But actually there are many choices for us to get it and all of you own better knowledge and experience about it than me. Beside using my SEO technique what I want to show you here is about the way to write title and the way to write first page of your post.
What I have done to most of my post titles is composing them from some keywords that usually searched by people. Maybe you ever found there are some titles that false to be said as a title. This might caused by I am not the expert in combining these keywords. But what you need to underlined is make your post title contained with multiple keywords.
Then the second is about writing your first page of your post. I am not forcing you to do this but I this is what I always do to my first line of my post. I rewrite my post title and combine it with the other word until appropriately, it become a sentence.
This is my habit in writing. I don’t have any goal, I don’t mean to become a guru. I know that all of you have better knowledge than me. It is up to you if to use this tips when you interested. But if you are not interested to this post, think that this only an proof really use SEO to write. I am sorry, I just an online farmer who farming through this blog. Once more I really sorry for all mistakes I have made accidentally. Hope my trick can increase your website traffic.
 Facebook Texas Hold'Em are most favourite game for some peoles facebook user. Here, in this page will inform you of various poker cheats on Facebook as they become available. A number of cheats come up for Facebook Zynga poker from time to time, and although these are periodically caught and blocked by Facebook, new ones are developed frequently.
Facebook Texas Hold'Em are most favourite game for some peoles facebook user. Here, in this page will inform you of various poker cheats on Facebook as they become available. A number of cheats come up for Facebook Zynga poker from time to time, and although these are periodically caught and blocked by Facebook, new ones are developed frequently.Since cheats are developed frequently, the methods for gaining chips can vary. Sometimes, these cheats are simple methods to employ, while other times a hack can be used to add money to your poker account or make certain cards available more often. This page will provide links to current cheats and will provide information on the availability and consequences of using these cheats.
Aside from Facebook, Zynga Poker can also be played on MySpace and MyYahoo. The actual game is Texas Hold Em. In order to play Zynga Poker, players must have Adobe Flash. Players can acquire extra poker chips by accepting daily bonus chips sent by friends. The game also features contests like the Shoutout Grand Prize of the Week as well as a Weekly Tournament. In July of 2010 Facebook's Zynga Poker offered free chips and prizes during a "Summer Fun" hourly contest. Other prizes included items like a Zynga Poker t-shirt.
Facebook Poker Cheats
A common cheat used is the "ghost" cheat, whereby a player uses an alternate Facebook account to create a ghost player on his or her table. This way, the player has a higher chance of winning by playing as two or more players at the same time on the same table.
Several cheats and hacks have been developed to help players acquire poker chips more quickly than they are earned through normal gameplay. Be advised that these cheats are against the terms of service of each game, and using them puts your gaming account at risk. This page contains links to available cheats, but because the community and game developer monitor illicit activity, the cheats available may be limited and changed often.
 Website are the basic tools for us to share on the internet, especially for online promotion. Links from the inside (called internal links) of your site will get you to the top of search engine rankings, but if internal linking isn’t getting you where you need to go, then it’s time to bring in some help from outside of your site. Over time, your link building efforts will increase your ability to do things with internal links as well.
Website are the basic tools for us to share on the internet, especially for online promotion. Links from the inside (called internal links) of your site will get you to the top of search engine rankings, but if internal linking isn’t getting you where you need to go, then it’s time to bring in some help from outside of your site. Over time, your link building efforts will increase your ability to do things with internal links as well.Please remember, link building is the only method to increase our website search engine ranking. If we can do link building well, we have done the right online promotion method. With each planning cycle, take stock of your links, and the effectiveness of your link building activities. Activities that have been particularly successful are worth pursuing further or expanding. Those that haven’t delivered need to be improved or removed from your plan.
Because I put a strong emphasis on profitable promotions, I like to try something new with every planning cycle. I always want to have at least one new type of promotion going on, with the goal in mind of creating a profitable marketing activity that will create links as a side benefit.
If you have paid for advertising from vertical directories, take a look at the traffic these links are bringing in, and how well it converts into leads and sales. If you find a particularly profitable type of advertising, then look for ways to expand it, possibly reducing the budget in other areas where you aren’t generating a profit.
In the long run, we want our link building campaign to pay for itself. That’s not an easy goal to reach right away, but it is possible to get there over time. So, don;t think the other way with our online promotion method, just focus for the link building campaign.
 SEO are the most important thing when we have a site, one of the worst mistakes that novices make is trying to focus on a single word or phrase for SEO keyword, and attempt to build a good website that will rank well. Extremely general terms such as these are very competitive, difficult for search engines to handle well (in terms of giving good results to searchers), and hardly worth the trouble in the first place.
SEO are the most important thing when we have a site, one of the worst mistakes that novices make is trying to focus on a single word or phrase for SEO keyword, and attempt to build a good website that will rank well. Extremely general terms such as these are very competitive, difficult for search engines to handle well (in terms of giving good results to searchers), and hardly worth the trouble in the first place.Let’s imagine that, after spending hundreds of hours tweaking, perfecting, and promoting your site, you managed to get a #1 ranking for “real estate.” Unless you sell real estate of all kinds in every part of the world, a substantial amount of the traffic you’ll get will come from people who are looking for something you don’t have to offer.
Although you may not optimize your site for such keywords. SEO keyword learning is very important that you know what they are, as it applies to your site. As you work through this post, make a list of the 5-10 “major” keywords that describe your website. It's named SEO keyword learning.
Internet is certainly one of the best ways of reaching out to people easily. Web hosting is a kind of internet hosting service through which even individuals can make their own website available on the net. Normally all organizations broadcast their website with the help of web hosting service providers. Web hosting service providers provide storage space, connectivity and all the related services necessary, to provide the files of a website on the internet. There are a lot of such providers available these days. To choose the best among them, one can rely on the reviews and ratings provided by webhostinggeeks.com.
This website publishes website news and latest trends in web hosting, apart from rating the top web hosting providers, considering every aspect of their service like reliability, firewall protection, uptime speed and support and so on. If you are in search of a cheap web hosting information provider then you can compare the cost of services of the providers listed here against their quality of services, mentioned in the reviews and choose the most feasible provider. Some organizations require large disk space and the bandwidth provided in shared servers will not be adequate for hosting their site. In this case, they can opt for dedicated servers. Webhostinggeeks.com gives you a list of best dedicated servers to choose from. Careful analysis has to be done by the organization before deciding on shifting their web base to dedicated servers because a lot of cost and technical support in included in this type of hosting.
READ MORE
This website publishes website news and latest trends in web hosting, apart from rating the top web hosting providers, considering every aspect of their service like reliability, firewall protection, uptime speed and support and so on. If you are in search of a cheap web hosting information provider then you can compare the cost of services of the providers listed here against their quality of services, mentioned in the reviews and choose the most feasible provider. Some organizations require large disk space and the bandwidth provided in shared servers will not be adequate for hosting their site. In this case, they can opt for dedicated servers. Webhostinggeeks.com gives you a list of best dedicated servers to choose from. Careful analysis has to be done by the organization before deciding on shifting their web base to dedicated servers because a lot of cost and technical support in included in this type of hosting.
Ever you tired to remember password that lock access to your document, this night kartolocyber will share tips to remove password for Ms. Word 2007. Check this out blogger....
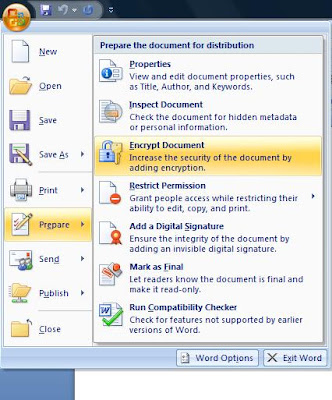
While encrypting and locking word documents is easier in Microsoft Word 2007, removing Word password is equally easier.Here is how you remove passwords or unlock word documents.
How to remove Word password?
* Open the Word 2007 document that has been encrypted and password protected.
It will ask you for the password.Enter the password and click OK
* Click on the office icon on the top left
* Select Prepare >> Encrypt document
* An Encrypt document dialog box pops up with the password set (in asterisk)
* Clear the password and click Ok
* Save and close the Word 2007 document
That is all folks!!! If you open the Word 2007 document again, it would no longer ask you for the password. Isn’t password protection and removal easy in Office 2007? You do not require any third party utility to password protect or encrypt your important Word documents and Excel files. While locking Office 2007 documents with strong passwords is easy, removing the password is equally easier.
READ MORE

While encrypting and locking word documents is easier in Microsoft Word 2007, removing Word password is equally easier.Here is how you remove passwords or unlock word documents.
How to remove Word password?
* Open the Word 2007 document that has been encrypted and password protected.
It will ask you for the password.Enter the password and click OK
* Click on the office icon on the top left
* Select Prepare >> Encrypt document
* An Encrypt document dialog box pops up with the password set (in asterisk)
* Clear the password and click Ok
* Save and close the Word 2007 document
That is all folks!!! If you open the Word 2007 document again, it would no longer ask you for the password. Isn’t password protection and removal easy in Office 2007? You do not require any third party utility to password protect or encrypt your important Word documents and Excel files. While locking Office 2007 documents with strong passwords is easy, removing the password is equally easier.
Of all the precious metals, gold is the most popular as an investment. Investors generally buy gold as a hedge or safe haven against any economic, political, social or currency-based crises. These crises include investment market declines, currency failure, inflation, war and social unrest. Investors also buy gold during times of a bull market in an attempt to gain financially. Investors generally buy gold for two main reasons: because they believe that gold prices will continue to rise and thus that they can gain financially, and/or as a hedge or a perceived safe haven against any economic, political, social or currency-based crises. Of course prices can fall as well as rise, so investors must make a best guess on what the future holds.
A gold coin is a coin made mostly or entirely of gold. Gold has been used for coins practically since the invention of coinage, originally because of gold’s intrinsic value. In modern times, most gold coins are intended either to be sold to collectors, or to be used as bullion coins — coins whose nominal value is irrelevant and which serve primarily as a method of investing in gold.
While obsolete gold coins are primarily collected for their numismatic value, gold bullion coins today derive their value from the metal (gold) content — and as such are viewed by some investors as a “hedge” against inflation or a store of value.Bullion coins are also produced in fractions of an ounce – typically half ounce, quarter ounce, and one-tenth ounce. Bullion coins sometimes carry a face value as legal tender, The face value is minted on the coin, and it is done so in order to bestow legal tender status on a coin, which generally makes it easier to import or export across national borders. However, their real value is measured as dictated by their troy weight, the current market price of the precious metal contained, and the prevailing premium that market wishes to pay for those particular bullion coins. The face value is always significantly less than the bullion value of the coin.
READ MORE
A gold coin is a coin made mostly or entirely of gold. Gold has been used for coins practically since the invention of coinage, originally because of gold’s intrinsic value. In modern times, most gold coins are intended either to be sold to collectors, or to be used as bullion coins — coins whose nominal value is irrelevant and which serve primarily as a method of investing in gold.
While obsolete gold coins are primarily collected for their numismatic value, gold bullion coins today derive their value from the metal (gold) content — and as such are viewed by some investors as a “hedge” against inflation or a store of value.Bullion coins are also produced in fractions of an ounce – typically half ounce, quarter ounce, and one-tenth ounce. Bullion coins sometimes carry a face value as legal tender, The face value is minted on the coin, and it is done so in order to bestow legal tender status on a coin, which generally makes it easier to import or export across national borders. However, their real value is measured as dictated by their troy weight, the current market price of the precious metal contained, and the prevailing premium that market wishes to pay for those particular bullion coins. The face value is always significantly less than the bullion value of the coin.
nite blogger, do you know about main function of computer? One of computer’s main function is to store datas. Computer can store data on harddrives, optical medias, etc. Optical media storage, which are read-only, has the advantage to keep computer data safe. This is due to read-only access to keep data safe from malware or viruses attacks. In addition to computer data, optical media such as CD-R and DVD-R is also used in the audio and video industries.
at the beggining in the United States, there was a market separation between ‘Music CD-R’ and ‘Data CD-R’, the former being several times more expensive than the latter due to industry copyright. Physically, there is no difference between the discs save for the Disc Application Flag that identifies their type: standalone audio recorders will only accept ‘Music CD-R’, while computer CD-R drives can use either type of media to burn either type of data files. Until then, Taiyo Yuden was developed dye materials made it possible for CD-R discs to be compatible with Audio CD and CD-ROM discs.
According to Wikipedia, the basic formulations of dye used in Taiyo Yuden CD-Rs is Cyanine. Cyanine dye CD-Rs were the earliest ones developed, and their formulation is patented by Taiyo Yuden. CD-Rs based on this dye are mostly green in color. The earlier models were very chemically unstable and this made cyanine based discs unsuitable for archival use; they could fade and become unreadable in a few years. Many manufacturers like Taiyo Yuden use proprietary chemical additives to make more stable cyanine discs (”metal stabilized Cyanine”, “Super Cyanine”). Older cyanine dye based CD-Rs, as well as all the hybrid dyes based on cyanine, were very sensitive to UV-rays and could have become unreadable after only a few days if they were exposed to direct sunlight. Although the additives used have made cyanine more stable, it is still the most sensitive of the dyes in UV rays (showing signs of degradation within a week of direct sunlight exposure). A common mistake users make is to leave the CD-Rs with the “clear” (recording) surface upwards, in order to protect it from scratches, as this lets the sun hit the recording surface directly.
Beside CD-Rs, they also manufactured Taiyo Yuden DVD-Rs. DVD media manufactured my Taiyo Yuden known by following media codes, for more information about it you can see on wikipedia.
hope this article can help blogger for choose the best Optical storage for you data.
READ MORE
at the beggining in the United States, there was a market separation between ‘Music CD-R’ and ‘Data CD-R’, the former being several times more expensive than the latter due to industry copyright. Physically, there is no difference between the discs save for the Disc Application Flag that identifies their type: standalone audio recorders will only accept ‘Music CD-R’, while computer CD-R drives can use either type of media to burn either type of data files. Until then, Taiyo Yuden was developed dye materials made it possible for CD-R discs to be compatible with Audio CD and CD-ROM discs.
According to Wikipedia, the basic formulations of dye used in Taiyo Yuden CD-Rs is Cyanine. Cyanine dye CD-Rs were the earliest ones developed, and their formulation is patented by Taiyo Yuden. CD-Rs based on this dye are mostly green in color. The earlier models were very chemically unstable and this made cyanine based discs unsuitable for archival use; they could fade and become unreadable in a few years. Many manufacturers like Taiyo Yuden use proprietary chemical additives to make more stable cyanine discs (”metal stabilized Cyanine”, “Super Cyanine”). Older cyanine dye based CD-Rs, as well as all the hybrid dyes based on cyanine, were very sensitive to UV-rays and could have become unreadable after only a few days if they were exposed to direct sunlight. Although the additives used have made cyanine more stable, it is still the most sensitive of the dyes in UV rays (showing signs of degradation within a week of direct sunlight exposure). A common mistake users make is to leave the CD-Rs with the “clear” (recording) surface upwards, in order to protect it from scratches, as this lets the sun hit the recording surface directly.
Beside CD-Rs, they also manufactured Taiyo Yuden DVD-Rs. DVD media manufactured my Taiyo Yuden known by following media codes, for more information about it you can see on wikipedia.
hope this article can help blogger for choose the best Optical storage for you data.
Wpdesigner.com is a top blog that grow with development of the innovative wordpress themes. A lot of great themes from 2 columns and 3 columns are provided on this site. Themost popular and used you maybe know are JWM(Jello Wala Mello) wordpress theme, digg 3 columns, and Peaceful Rush wordpress themes. Not only create and design wordpress themes, this blog is also give you a lot of great info. Like Tips, tutorials, and the others that will very useful, including the best webhosting to choose.
You all know that Wpdesigner.com is a beautiful sites with very useful contents and good performance. But, that all will be useless if they choose a bad host for their sites. Because, visitor will enjoy visiting our site, if the content is balanced with the rapid access. So, don’t be hesitate while choosing the best webhosting for your site, although it’s rather expensive. Don’t worry if you confuse in establish the best one. Wpdesigner has give you the top 10 webhosts company that have trusted by a lot of great sites in the world. Like bluehost, host gator, go daddy, and etc. All of them have a high reputation and credibility in global rivalry. It’s because they all give best price, best service, best performance to the webmaster.
So, don’t be afraid to take the best. Because performance is everything. Just try and click to Wpdesigner.com for more information.
READ MORE
You all know that Wpdesigner.com is a beautiful sites with very useful contents and good performance. But, that all will be useless if they choose a bad host for their sites. Because, visitor will enjoy visiting our site, if the content is balanced with the rapid access. So, don’t be hesitate while choosing the best webhosting for your site, although it’s rather expensive. Don’t worry if you confuse in establish the best one. Wpdesigner has give you the top 10 webhosts company that have trusted by a lot of great sites in the world. Like bluehost, host gator, go daddy, and etc. All of them have a high reputation and credibility in global rivalry. It’s because they all give best price, best service, best performance to the webmaster.
So, don’t be afraid to take the best. Because performance is everything. Just try and click to Wpdesigner.com for more information.
Over there are many things that they can do at home beside washing the car or just sweeping out the house that make them bored. Video Games
is the reason why people can stay at home in a long time though at a dirty and spooky room. Do you believe it? If you hard to believe it, try to buy a console game
then you can feel that the time in this world have been stopped by it.
If you want to buy video games through internet you’d better search it through reference site of website that provides you a guide to buy
such a thing based on internet. If you’re looking for the best place to receive best directory with its detailed information you can search it through Shop Wiki. In this directory store you can compare and even you can make this online directory store as your best reference site. They have also different kinds of video games controllers
that you can buy if you want too. Depending on your needs on what do you want to buy.You can see their owesome buying guide.
They also can give you handheld for those console or even the tips and tricks
to make playing games more fun. You also can surf this site after you buy the video games in order to know more the systems that you have or the tricks to finish your favorite games. Shopping what you need online will save your time, energy and money. Please note that not just video games, they also have various items sold on this web from many selections of stores. Bookmark this site now and enjoy your online shopping with Shop Wiki.
READ MORE
is the reason why people can stay at home in a long time though at a dirty and spooky room. Do you believe it? If you hard to believe it, try to buy a console game
then you can feel that the time in this world have been stopped by it.
If you want to buy video games through internet you’d better search it through reference site of website that provides you a guide to buy
such a thing based on internet. If you’re looking for the best place to receive best directory with its detailed information you can search it through Shop Wiki. In this directory store you can compare and even you can make this online directory store as your best reference site. They have also different kinds of video games controllers
that you can buy if you want too. Depending on your needs on what do you want to buy.You can see their owesome buying guide.
They also can give you handheld for those console or even the tips and tricks
to make playing games more fun. You also can surf this site after you buy the video games in order to know more the systems that you have or the tricks to finish your favorite games. Shopping what you need online will save your time, energy and money. Please note that not just video games, they also have various items sold on this web from many selections of stores. Bookmark this site now and enjoy your online shopping with Shop Wiki.
Nowadays, the growing of technology was very fast. It’s remain us, that our self must also can follow those situation. It means that we must work harder if we want to follow the growing of technology. That situation is familiar with the employee that has working on the company. If they not improve their skill, they will fallen into the lowest level on the company. I think, It will happen to everybody. Especially on IT company that must get a new revolution from minute to minute. For you that want to choose this sector, you must be careful. You must study harder to get this.
There is a lot of method in learning that can help us understanding the IT environment. For example, we can read a book or get them at school. But, it’s impossible for the employee that’s very busy. It will be no more time to read. I offer a great solution them. That’s by doing distance learning. Such as follow an online course and watching the training video. A site that provide that for you is countrywidetraining.com. Countrywide Training provides you world class IT training, certification training, computer training and other types of computer training, and it also provide you the ability for computer professionals everywhere to quickly and easily schedule IT training and technical training classes over the internet.
Beside that features, this site has a top level on the learning revolution. They only fill the course with the professional trainer, that can make us easily on learning the training progress. After you sign up on this course, you will get a complete computer based training (CBT) course and a practice exam for each course that you take. There’s a lot of programs on this site. Like Cisco Training, CompTIA, Microsoft Training, Networking and etc.They all are the vital part of IT company.
So, let’s sign up and check what programs that will you choose. Just click to www.countrywidetraining.com. Get your future in your hand.
READ MORE
There is a lot of method in learning that can help us understanding the IT environment. For example, we can read a book or get them at school. But, it’s impossible for the employee that’s very busy. It will be no more time to read. I offer a great solution them. That’s by doing distance learning. Such as follow an online course and watching the training video. A site that provide that for you is countrywidetraining.com. Countrywide Training provides you world class IT training, certification training, computer training and other types of computer training, and it also provide you the ability for computer professionals everywhere to quickly and easily schedule IT training and technical training classes over the internet.
Beside that features, this site has a top level on the learning revolution. They only fill the course with the professional trainer, that can make us easily on learning the training progress. After you sign up on this course, you will get a complete computer based training (CBT) course and a practice exam for each course that you take. There’s a lot of programs on this site. Like Cisco Training, CompTIA, Microsoft Training, Networking and etc.They all are the vital part of IT company.
So, let’s sign up and check what programs that will you choose. Just click to www.countrywidetraining.com. Get your future in your hand.
i think anyone know about this. similar in concept to CD-R, Blank DVD-R (or, DVD-Recordable) is a write-once medium that can contain any type of information normally stored on mass produced DVD discs - video, audio, images, data files, multimedia programs, and so on. Depending on the type of information recorded, DVD-R discs are usable on virtually any compatible DVD playback device, including DVD-ROM drives and DVD Video players. An early release of DVD-R was important to the development of DVD-ROM titles since software developers needed a simple and relatively cheap way of producing test discs before going into full production.
but If you need Back up your data to the save media, you can use CD-R Media or DVD-R Media for your media. you can find Top Quality CD-R & DVD-R at a Great Price at Blank DVD-R Got Media Shop. you can find medias you need, it's offer offers a variety of media : DVD-R, DVD+R, DVD R DL (Dual Layer), Blu-ray Media, BD-R and etc.
there's one think that you must know that Data on a DVD-R cannot be changed, whereas a DVD-RW (DVD-rewritable) can be rewritten multiple (1000+) times. DVD-R(W) is one of three competing industry standard DVD recordable formats; the others are DVD+R(W) and DVD-RAM.
READ MORE
but If you need Back up your data to the save media, you can use CD-R Media or DVD-R Media for your media. you can find Top Quality CD-R & DVD-R at a Great Price at Blank DVD-R Got Media Shop. you can find medias you need, it's offer offers a variety of media : DVD-R, DVD+R, DVD R DL (Dual Layer), Blu-ray Media, BD-R and etc.
there's one think that you must know that Data on a DVD-R cannot be changed, whereas a DVD-RW (DVD-rewritable) can be rewritten multiple (1000+) times. DVD-R(W) is one of three competing industry standard DVD recordable formats; the others are DVD+R(W) and DVD-RAM.
In this modern life, the human being can’t separate from the growing of technology. Especially about computer. It’s very important for us to learn computer, even a little. Moreover, you must have a skill in using computer if you want to apply a job. Such as Microsoft Office and Data Entry. I won’t explain about it. I will tell you about the part of networking. A part of computer and internet that can’t liberated. That’s wireless network. Firstly, you all knowing what is networking. Yes, networking is group of computer that connect one another. The easiest way in network connection is using UTB cable. It can allow us to share files and share internet with another. But, it’s limited with the distance. It can only connect in one room. So, we need wireless. A new way in internet connection.
Wireless is how we can connect to the internet without a cable in long distance. There’s a company that provide us internet access via wireless. That is “Internet Service Provider”, that called ISP. ISP selling internet connection service to us in many ways. And the greatest one is wireless. Usually, ISP will give us a modem network and antena that will be set in our home roof. Why in roof? Because it need a free place for signal transfer. If there’s a lot of noise, such as high building and towers, the internet connection will be slow or maybe broken. So, you must suppose your place before applying wireless broadband access.
There’s another way in wireless network. That is Wi-fi. A network connection that suitable for public place. Like station, university and school. Wi-fi is a network connection that can be used freely. And using automatic IP or DHCP. Just switch on the wireless switch and we can start to access the internet. So, that’s why wireless is the most favourite way in internet network connection. And because it's easy to Understanding Wireless Networking.
READ MORE
Wireless is how we can connect to the internet without a cable in long distance. There’s a company that provide us internet access via wireless. That is “Internet Service Provider”, that called ISP. ISP selling internet connection service to us in many ways. And the greatest one is wireless. Usually, ISP will give us a modem network and antena that will be set in our home roof. Why in roof? Because it need a free place for signal transfer. If there’s a lot of noise, such as high building and towers, the internet connection will be slow or maybe broken. So, you must suppose your place before applying wireless broadband access.
There’s another way in wireless network. That is Wi-fi. A network connection that suitable for public place. Like station, university and school. Wi-fi is a network connection that can be used freely. And using automatic IP or DHCP. Just switch on the wireless switch and we can start to access the internet. So, that’s why wireless is the most favourite way in internet network connection. And because it's easy to Understanding Wireless Networking.
I remember about my friend who tell me about trouble in his notebook. His notebook was attacked by a virus and he lose some system data that make some his application program can’t work properly. Some corrupt data was reported there. i just told to him for reinstall his notebook. Well, his windows back fine and free from virus, but he lose application who was installed there and his windows haven’t worked properly yet. I little confused about it. Some master program may be back up there, but some others program and drivers aren’t there. we has tried to software store but I we keep can’t find all software and driver we needed.
Someday after that day, I try to looking for what we needed in internet. Much sites who offer and have much driver who I need. Until I visit to special drivers shop, and I call this site with the Drivers. There I can get driver who I need. Simple sites for exceptionally which have much drivers. Just click short index button there and smiley when you see what you need there, or if you fully remember what you need just type keyword driver and the Drivers will find that driver for you. So, if you want looking for drivers or update your driver, don’t worried, just visit the Drivers.
READ MORE
Someday after that day, I try to looking for what we needed in internet. Much sites who offer and have much driver who I need. Until I visit to special drivers shop, and I call this site with the Drivers. There I can get driver who I need. Simple sites for exceptionally which have much drivers. Just click short index button there and smiley when you see what you need there, or if you fully remember what you need just type keyword driver and the Drivers will find that driver for you. So, if you want looking for drivers or update your driver, don’t worried, just visit the Drivers.